
Cloudflare has mitigated a distributed denial-of-service (DDoS) attack that peaked at a record-breaking 22.2 terabits per second (Tbps) and 10.6 billion packets per second (Bpps).
DDoS attacks typically exhaust either system or network resources, aiming to make services slow or unavailable to legitimate users.
Record-breaking DDoS attacks are becoming more frequent, as just three weeks ago, Cloudflare disclosed that it mitigated a massive 11.5 Tbps and 5.1 Bpps attack, the largest publicly announced at the time.
Two months before that, the company dealt with another ecord attack that peaked at 7.3 Tbps. In April, the internet giant warned that it was dealing with a record number of DDoS attacks this year.
The latest DDoS incident, also volumentric, lasted 40 seconds and is by far the largest ever mitigated.
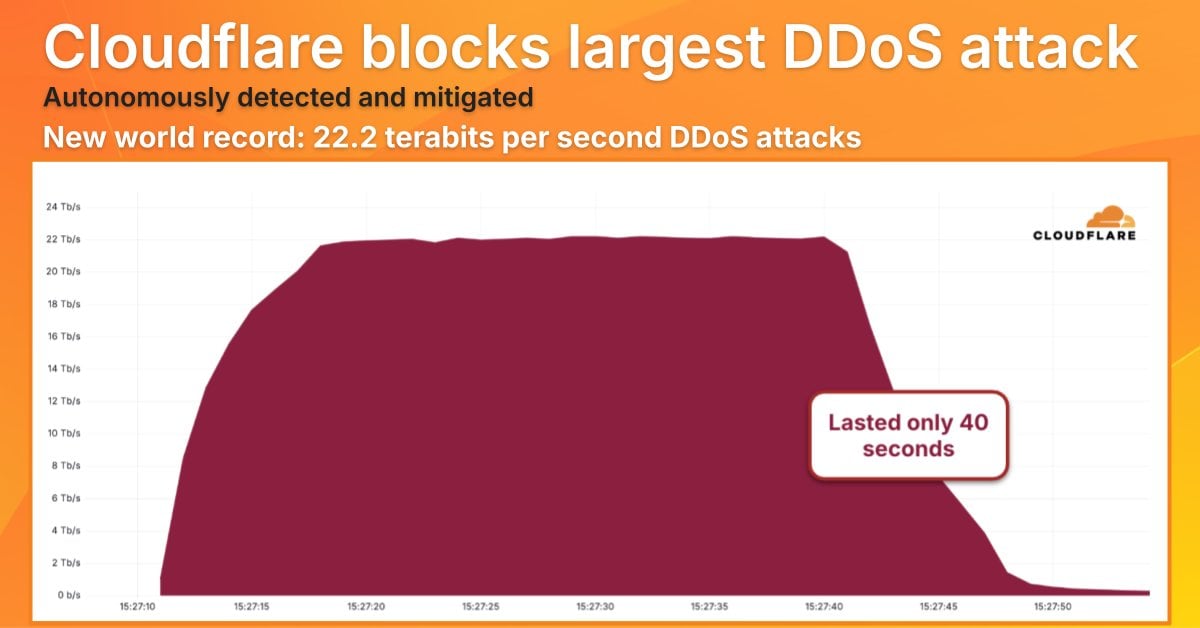
Source: Cloudflare
Despite the short assault period, the volume of traffic directed at the victim was enormous, roughly equivalent to streaming one million 4K videos simultaneously.
The packet rate of 10.6 Bpps can be translated to roughly 1.3 web page refreshes per second from every person on the planet.
The large volume of packets makes it particularly difficult for firewalls, routers, and load balancers to process the requests, even if the total bandwidth is manageable.
Although Cloudflare has not shared many details about the last two DDoS attacks, XLab research division at Chinese cybersecurity company Qi'anxin attributed an 11.5 Tb DDoS attack to the AISURU botnet.
According to the researchers, AISURU has infected more than 300,000 devices worldwide, with a sudden increase occuring in April 2025 after the compromise of a Totolink router firmware update server.
The botnet also targets vulnerabilities in IP cameras, DVRs/NVRs, Realtek chips, and routers from T-Mobile, Zyxel, D-Link, and Linksys.
Break down IAM silos like Bitpanda, KnowBe4, and PathAI
Broken IAM isn't just an IT problem - the impact ripples across your whole business.
This practical guide covers why traditional IAM practices fail to keep up with modern demands, examples of what "good" IAM looks like, and a simple checklist for building a scalable strategy.









Comments
Surfernaut - 3 months ago
Back in 1999 I saw a huge influx of cyber attacks coming from China. Sent router log files to the FBI cyber crime page but nothing was ever done or addressed. I'm sure the majority of these attacks originate from the communist reds.
Drags - 3 months ago
"Back in 1999 I saw a huge influx of cyber attacks coming from China. Sent router log files to the FBI cyber crime page but nothing was ever done or addressed. I'm sure the majority of these attacks originate from the communist reds."
and yet, when checking into traffic origin of those attacks, a majority will be US traffic due to lax security from the US of A. Would still love to see the data to back up your "I'm sure the majority" claim.
jacklim - 3 months ago
Amazing Post
ZdejPoham - 3 months ago
... 10.6 billion packets per second (Bpps)...
Normal billion (10^12) or american billion (10^9)? And how many school buses would that be?