
Image: ThreatFabric
A new Android banking trojan dubbed BlackRock steals credentials and credit card information from a list of 337 apps many of them used for many non-financial purposes.
The malware was discovered in May by ThreatFabric analysts and it is derived from the leaked source code of the Xerxes banking malware, a known strain of the LokiBot Android trojan.
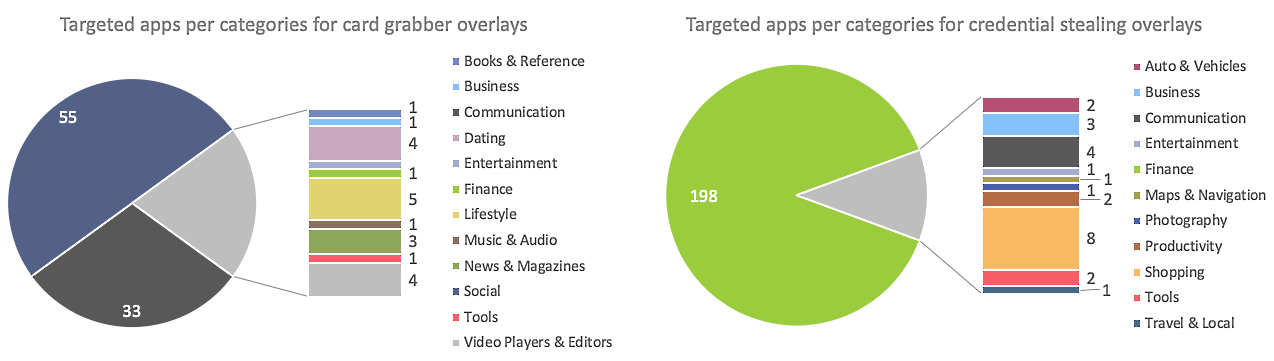
Besides being the only Android malware based on Xerxes' source code, BlackRock also features another peculiarity: unlike other banking trojans, it targets a lot of non-financial Android apps, with a focus on social, communication, networking, and dating platforms.
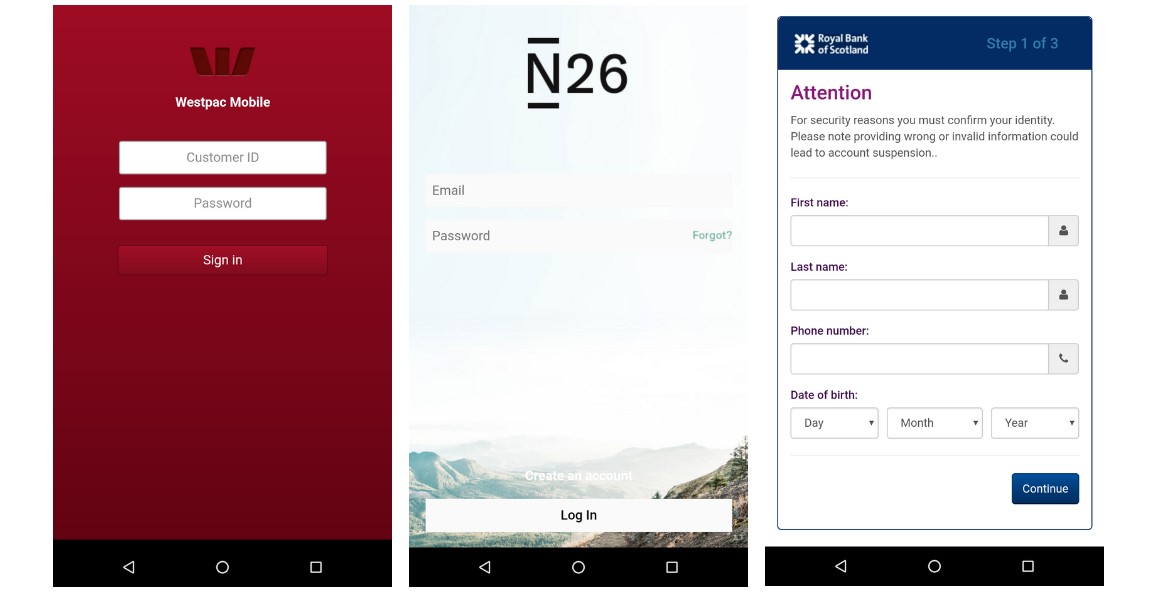
BlackRock camouflages itself as Google Update to request Accessibility Service privileges and it will hide its icon to When launched by one of its victims.
"Once the user grants the requested Accessibility Service privilege, BlackRock starts by granting itself additional permissions," ThreatFabric said.
"Those additional permissions are required for the bot to fully function without having to interact any further with the victim."
The operators can then control the malware remotely to launch overlay attacks and issue a multitude of commands including logging keystrokes, spamming the victims' contact lists with text messages, setting the malware as the default SMS manager, pushing system notifications to the C2 server, and blocking victims from launching or using antivirus or system cleaning software.
BlackRock's creators have also made sure that no unnecessary features from Xerxes' code are left, removing any capabilities that weren't helpful in their goals to steal logins and financial info from infected Android devices.
The malware also makes use of Android work profiles to control the compromised device without requiring admin permissions but, instead, creating its own managed profile with admin rights.
BlackRock's credential theft target list of 226 apps includes Microsoft Outlook, Gmail, Google Play services, Uber, Amazon, Netflix, Cash App, as well as multiple cryptocurrency wallet apps such as Coinbase, BitPay, Binance, and Coinbase, and banks like Santander, Barclays, RBS, Lloyds, ING, and Wells Fargo.
The credit card theft target list contains 111 applications including but not limited to Telegram, WhatsApp, Twitter, Skype, Instagram, Facebook, Play Store, YouTube, VK, Reddit, TikTok, Tinder, and Grindr.
"The second half of 2020 will come with its surprises, after Alien, Eventbot and BlackRock we can expect that financially motivated threat actors will build new banking Trojans and continue improving the existing ones," ThreatFabric concluded.
"With the changes that we expect to be made to mobile banking Trojans, the line between banking malware and spyware becomes thinner, banking malware will pose a threat for more organizations and their infrastructure, an organic change that we observed on windows banking malware years ago."
Break down IAM silos like Bitpanda, KnowBe4, and PathAI
Broken IAM isn't just an IT problem - the impact ripples across your whole business.
This practical guide covers why traditional IAM practices fail to keep up with modern demands, examples of what "good" IAM looks like, and a simple checklist for building a scalable strategy.









Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now