
Security researchers have detected a new wave of cryptocurrency-mining malware infecting servers across the web, and this one is using multiple exploits to gain access to vulnerable and unpatched systems to install a Monero miner.
Experts from AlienVault say this new campaign —which they dubbed MassMiner— uses exploits for vulnerabilities such as CVE-2017-10271 (Oracle WebLogic), CVE-2017-0143 (Windows SMB), and CVE-2017-5638 (Apache Struts).
MassMiner campaign uses famous exploits
The MassMiner crew sure has an excellent taste when it comes to exploits. All of the above are well-known and highly efficient vulnerabilities.
CVE-2017-10271 has been under active exploitation since last year, and at least one gang made a killing with it, racking up over $226,000 from covert cryptocurrency mining operations. The vulnerability is still one of the most actively targeted server flaw, even today.
CVE-2017-0143 is the more famous of the three, being known as EternalBlue; an exploit developed by the US NSA and leaked online by a hacker group known as The Shadow Brokers. It's been used for a lot of malware ops, including the WannaCry and NotPetya ransomware outbreaks from last year. For the MassMiner attacks, AlienVault says hackers are using EternalBlue to install the DoublePulsar backdoor on vulnerable hosts.
Last but not least, CVE-2017-5638 is the same exploit that hackers used to breach US financial firm Equifax, last summer.
In addition, crooks are also leveraging SQLck, a tool for carrying out brute-force attacks against Microsoft SQL databases, which, if compromised, attackers also use as an intermediary point to launch SQL scripts and install a local cryptocurrency miner.
The entire infection chain has been detailed in a write-up by AlienVault researcher Chris Doman, who also put together the following graph, for a graphical explanation of the entire process.
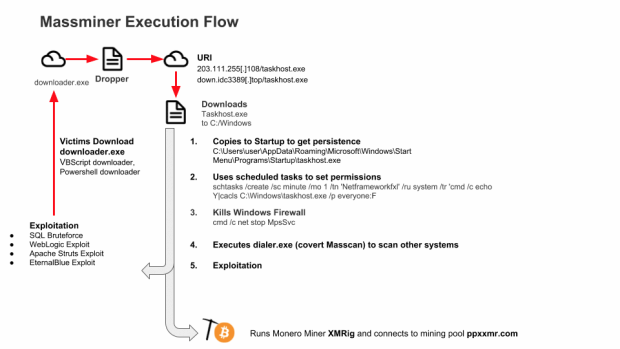
Hackers own $295,000, albeit not all from MassMiner
Monero addresses associated with this group have been used to mine around 1,200 Monero, nearly $295,000. However, it is unclear if all the money came from the MassMiner campaign, or crooks had other sources of "revenue."
While the MassMiner campaign was only recently discovered and uses its own unique infection mechanism, different from what researchers have seen in the past, Doman told Bleeping Computer today that there are clues suggesting MassMiner may be related to the infamous Smominru. This a botnet that infected over 526,000 Windows machines last year for the purpose of covert cryptocurrency mining alone, and supposedly made over $2.3 million for its creators.
MassMiner is also not the only recent coin-mining operation that has started combining multiple exploits to improve its chances of infecting more victims than it would have infected if it used one exploit at a time. The ReddisWannaMine campaign is another, targeting Redis, Apache Solr, and Windows Server instances.
Another recently exposed coin-mining operation is PyRoMine, detected by Fortinet last week. PyRoMine used two NSA exploits —EternalBlue and EternalRomance— to infect unpatched Windows Server instances. PyRoMine was a relatively new campaign, which got off the ground only at the start of April, and Fortinet says it only mined 2.4 Monero, or the equivalent of $600 at today's exchange rate.
It has become quite evident to most infosec experts that coinminers are one of 2018's most widespread malware threat, far more popular than ransomware. Nonetheless, adware families remain the undisputed kings of the malware scene.
Break down IAM silos like Bitpanda, KnowBe4, and PathAI
Broken IAM isn't just an IT problem - the impact ripples across your whole business.
This practical guide covers why traditional IAM practices fail to keep up with modern demands, examples of what "good" IAM looks like, and a simple checklist for building a scalable strategy.









Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now