-
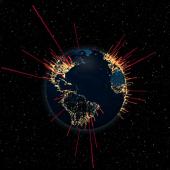
Nation-state actor hit Google with the largest DDoS attack
In an overview of distributed denial-of-service (DDoS) trends targeting its network links, Google revealed that in 2017 a nation-state actor used massive firepower that amounted to more than 2.7 terabits per second.
- October 16, 2020
- 05:30 PM
 0
0
-
Network intruders selling access to high-value companies
Breaching corporate networks and selling access to them is a business in and of itself. For many hackers, this is how they make their living, others do it forced by financial struggles to supplement their revenue.
- August 11, 2020
- 02:43 PM
 0
0
-
New Webinar: Choose Your Own Investigation — Browser Attack Edition

Modern attacks have shifted focus to the browser, yet detection tools remain largely blind to the crucial activity happening there.
Join Push Security on February 11th for an interactive "choose-your-own-adventure" webinar on ClickFix, credential phishing, and other in-browser attacks we've observed in the wild.
-
Critical SharePoint flaw dissected, RCE details now available
Details are now available for exploiting a critical security vulnerability that affects Microsoft SharePoint, increasing the risk of attacks on unpatched systems.
- July 22, 2020
- 11:33 AM
 0
0
-
Hackers are quick to notice exposed Elasticsearch servers
Bad guys find unprotected Elasticsearch servers exposed on the web faster than search engines can index them. A study found that threat actors are mainly going for cryptocurrency mining and credential theft.
- June 12, 2020
- 03:27 AM
 0
0
-
Critical Citrix ShareFile bugs could give access to private files
Citrix has fixed three vulnerabilities in multiple versions of ShareFile storage zone controllers that could be exploited without authentication for access to private data areas.
- May 06, 2020
- 12:34 PM
 1
1
-
Hackers exploit Salt RCE bugs in widespread attacks, PoCs public
Hackers kept busy this weekend exploiting vulnerable Salt instances used in various infrastructures for server management and automation.
- May 04, 2020
- 01:19 PM
 0
0
-
LineageOS outage caused by hackers breaching main infrastructure
Administrators of LineageOS Android custom operating system were on high alert on Saturday after hackers breached their main infrastructure, causing a full outage.
- May 04, 2020
- 02:32 AM
 1
1
-
New Critical RCE Bug in OpenBSD SMTP Server Threatens Linux Distros
Security researchers have discovered a new critical vulnerability in the OpenSMTPD email server. An attacker could exploit it remotely to run shell commands as root on the underlying operating system.
- February 25, 2020
- 05:49 AM
 0
0
-
Tesla Pays $10K for Microsoft SQL Server Reporting Services Bug
Tesla paid a $10,000 bounty for a vulnerability in Microsoft SQL Server Reporting Services (SSRS) that had received a patch five days before getting the bug submission.
- February 20, 2020
- 07:00 AM
 1
1
-
Windows, Linux Devices at Risk Due to Unsigned Peripheral Firmware
Researchers have discovered multiple instances of unsigned firmware in computer peripherals that can be used by malicious actors to attack laptops and servers running Windows and Linux.
- February 18, 2020
- 06:00 AM
 1
1
-
Critical Remote Code Execution Bug Fixed in OpenBSD SMTP Server
A critical vulnerability in the free OpenSMTPD email server present in many Unix-based systems can be exploited to run shell commands with root privileges.
- January 29, 2020
- 10:51 AM
 0
0
-
Bulletproof Hosting Service in Former NATO Bunker Goes Down
Authorities in Germany this week shut down the services of a bulletproof hosting provider set up in a former NATO bunker that went five floors underground.
- September 30, 2019
- 03:23 AM
 0
0
-
Unpatched Squid Servers Exposed to DoS, Code Execution Attacks
Multiple versions of the Squid web proxy cache server built with Basic Authentication features are currently vulnerable to code execution and denial-of-service (DoS) attacks triggered by the exploitation of a heap buffer overflow security flaw.
- August 22, 2019
- 02:19 PM
 0
0
-
Exposed Sphinx Servers Are No Challenge for Hackers
Attackers can take advantage of Sphinx web servers exposed on the internet to access, alter, or remove data in the database, warns CERT-Bund, Germany's computer emergency response team.
- August 20, 2019
- 12:00 PM
 0
0
-
Millions of Exim Mail Servers Are Currently Being Attacked
Millions of mail servers running vulnerable Exim mail transfer agent (MTA) versions are currently under siege, with attackers gaining permanent root access via SSH to the exploited machines according to security researchers.
- June 13, 2019
- 02:32 PM
 0
0
-
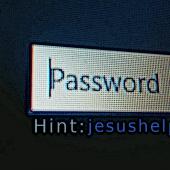
'jesushelpme' Password Sums Up CyberSec Agency Security State
Agents of the Information Network Security Agency (INSA) - the top-level cyber security agency in Ethiopia, used laughingly weak credentials to protect their email accounts.
- June 10, 2019
- 11:16 AM
 2
2
-
Millions of Exim Mail Servers Exposed to Local, Remote Attacks
A critical severity vulnerability present in multiple versions of the Exim mail transfer agent (MTA) software makes it possible for unauthenticated remote attackers to execute arbitrary commands on mail servers for some non-default server configurations.
- June 06, 2019
- 02:21 PM
 0
0
-
BlackSquid Uses 7 Exploits to Infect Web Servers with Miners
A newly discovered cryptomining threat targeting web servers, network drives, and removable drives comes filled to the brim with exploits and precautions against analysis tools and environments.
- June 03, 2019
- 08:59 PM
 0
0
-
Apache Bug Lets Normal Users Gain Root Access Via Scripts
A privilege escalation vulnerability of important severity in the Apache HTTP server allowing users with the right to write and run scripts to gain root on Unix systems was fixed in Apache httpd 2.4.39.
- April 02, 2019
- 09:51 AM
 0
0
-
Port of Barcelona Suffers Cyberattack
The Port of Barcelona was Thursday morning the victim of a cyberattack that affected some of its servers and systems, forcing the organization to launch the contingency plan designed specifically for these incidents.
- September 21, 2018
- 05:15 PM
 0
0