A new CryptoMix, or CryptFile2, variant was released that is now using the .[payment_email].ID[VICTIM_16_CHAR_ID].WALLET extension for encrypted files. This is very annoying as it makes it more difficult for victims to easily identify what ransomware they are infected with when they perform web searches. This is because the .WALLET extension has been used by Dharma/Crysis, Sanctions, and now we have CryptoMix. Currently payment email addresses are shield0@usa.com, admin@hoist.desi, and crysis@life.com.
This variant was discovered by independent security researcher R0bert R0senb0rg and later identified as CryptoMix by MalwareHunterTeam. I decided to take a look at the sample and take a deeper dive to see what has changed since the previous Revenge variant was released.
Unfortunately, at this time there is no way to decrypt files encrypted by this Wallet for free. For those who wish to discuss this ransomware or receive support, you can always use our CryptoMix or CrypMix Ransomware Help Topic.
As a note, in this article I will be referring to this infection as the Wallet Ransomware as that will most likely be how the victim's will search for it. It is important to remember, though, that this ransomware is not a brand new infection, but rather just a new version of the CryptoMix ransomware family.
Update: 5/1/17 5:03PM EST - Updated the article a bit to include another payment email address provided by xXToffeeXx.
How the Wallet Ransomware Encrypts a Victim's Files
Unfortunately, at this time we have no knowledge as to how the Wallet Ransomware is currently being distributed. What we do know is that once the executable is started, it will generate a unique 16 hexadecimal victim ID and an encryption key on the computer and then send this information back to the Command & Control server.
It will then begin to scan the computer for files to encrypt. Unlike most ransomware infections, and the previous Revenge version, this version does not target specific extensions, but rather encrypts any files it detects as long as they are not located in certain whitelisted folders. The list of whitelisted folders are:
WINDOWS, PACKAGES, COOKIES, PROGRAMDATA, MICROSOFT, BOOT, APPLICATION DATA, WINNT, INETCACHE, NVIDIA, SYSTEM VOLUME INFORMATION, $RECYCLE.BIN, TEMP, PROGRAM FILES, PROGRAM FILES (X86), CACHE, TEMPORARY INTERNET FILES, WEBCACHE, and APPDATA
When Wallet encrypts a file it will do so using AES encryption and then rename the encrypted file. When renameing the file, it will ROT-13 the original file name and then append the .[SHIELD0@USA.COM].ID[VICTIM_16_CHAR_ID].WALLET, or [admin@hoist.desi].ID[VICTIM_16_CHAR_ID].WALLET, or [crysis@life.com].ID[VICTIM_16_CHAR_ID].WALLET extensions, depending on the variant, to the encrypted filename.
For example, a file called test.jpg would be encrypted and renamed as grfg.wct.[SHIELD0@USA.COM].ID[1111111111111111].WALLET.
Note: Wallet will also scan unmapped network shares for files to encrypt. Therefore, be sure to lock down your network by securing network shares so only those that need to can write to the shares.
In each folder that Wallet encrypts a file, it will also create a ransom note named #_RESTORING_FILES_#.TXT. Unlike older versions of CryptoMix, this variant does not create a HTML version of the ransom note.
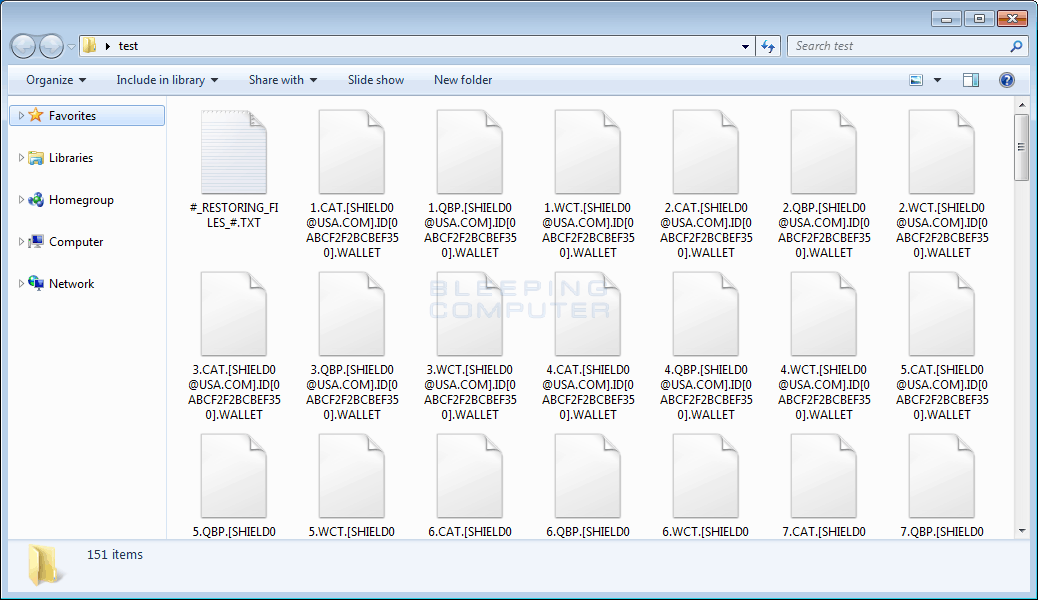
Wallet will then display a fake alert that states:
The instruction at 0xe9c71f6c referenced memory at 0x00000000C. The memory could not be read.
Click on Yes in the next window for restore work explorer.exe.
Like the fake alert in Revenge, the broken English in the Wallet alert should give victim's a hint that this alert is not legitimate.
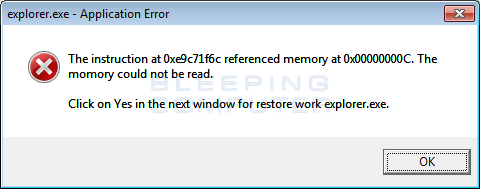
When the victim presses the OK button, the ransomware will use WMIC to launch an elevated version of the ransomware in order to execute bcdedit and to remove the volume shadow copies. This will cause a UAC, or User Account Control, prompt to appear like below. The above fake alert is used to try and convince the victim to press Yes at the below UAC prompt.
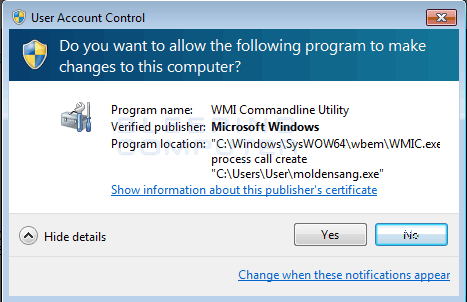
The victim will continue to see this fake alert until they press the Yes button at the UAC prompt. Once they do so, the ransomware will execute the following commands that disable the Windows startup recovery and to clear the Windows Shadow Volume Copies.
cmd.exe /C bcdedit /set {default} recoveryenabled No
cmd.exe /C bcdedit /set {default} bootstatuspolicy ignoreallfailures
C:\Windows\System32\cmd.exe" /C vssadmin.exe Delete Shadows /All /Quiet
Finally, the Wallet Ransomware will display a ransom note called #_RESTORING_FILES_#.TXT.
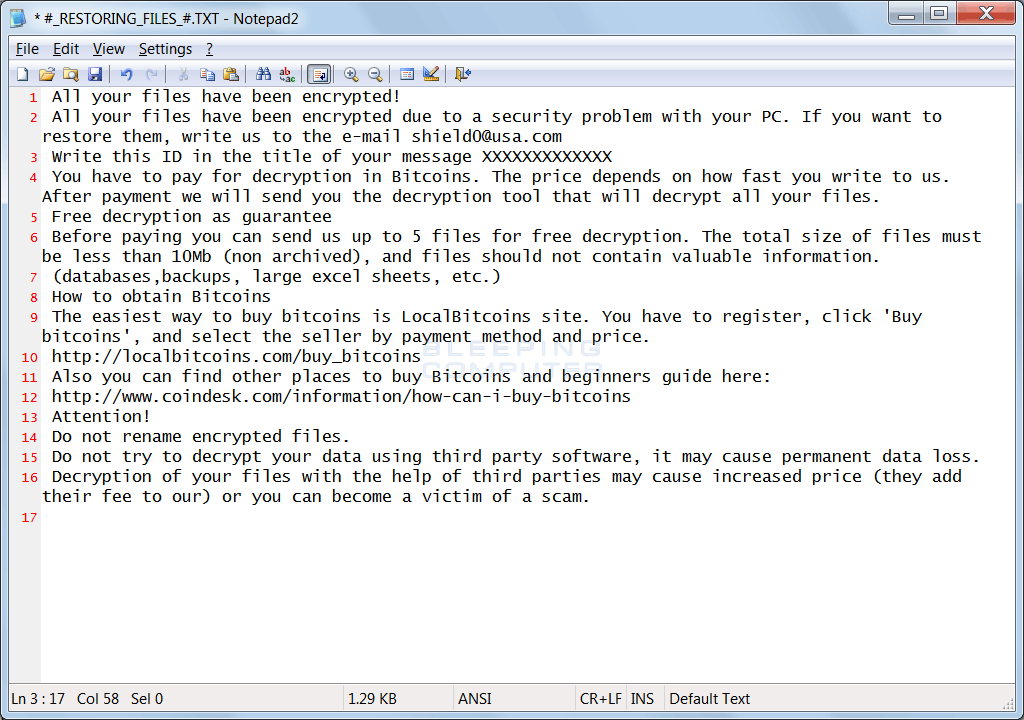
This ransom note contains information regarding what happened to your files, a personal identification ID, and an email addresses that can be used to contact the ransom developer for payment instructions. The current email addressses that have been seen with this variant are shield0@usa.com, admin@hoist.desi, and crysis@life.com. Finally, the developer is currently offering 5 free decryptions to prove that they can actually decrypt files.
Unfortunately, at this time there is no way to decrypt files encrypted by this Wallet for free. For those who wish to discuss this ransomware or receive support, you can always use our CryptoMix or CrypMix Ransomware Help Topic.
File Associated with the Wallet Ransomware Variant:
#_RESTORING_FILES_#.TXT
Wallet Ransomware Hashes:
SHA256:
8dc1f63089a3363715436feabca1c05cf6ff0505d20426a27665258e21aeadd9 (shield0@usa.com)
9eeee6a68082969ede5935da29c0a0442f0d9657f491562ba3c1004109705b6f (shield0@usa.com)
a0d06fe487b45a85f988ab7833d53ed9093fc4d4265123a5d3b2c97714d25123 (shield0@usa.com)
ce5b951daa9192741467f4260cbe3e8dd02c370bafe0f0e057005f40d427914a (admin@hoist.desi)
Wallet Ransomware Network Communication:
185.125.32.14/check/gif.php
Wallet Ransomware Associated Emails:
shield0@usa.com
admin@hoist.desi
crysis@life.com
Example Wallet Ransom Note Text:
All your files have been encrypted!
All your files have been encrypted due to a security problem with your PC. If you want to restore them, write us to the e-mail shield0@usa.com
Write this ID in the title of your message 0ABCF2F2BCBEF350
You have to pay for decryption in Bitcoins. The price depends on how fast you write to us. After payment we will send you the decryption tool that will decrypt all your files.
Free decryption as guarantee
Before paying you can send us up to 5 files for free decryption. The total size of files must be less than 10Mb (non archived), and files should not contain valuable information.
(databases,backups, large excel sheets, etc.)
How to obtain Bitcoins
The easiest way to buy bitcoins is LocalBitcoins site. You have to register, click 'Buy bitcoins', and select the seller by payment method and price.
http://localbitcoins.com/buy_bitcoins
Also you can find other places to buy Bitcoins and beginners guide here:
http://www.coindesk.com/information/how-can-i-buy-bitcoins
Attention!
Do not rename encrypted files.
Do not try to decrypt your data using third party software, it may cause permanent data loss.
Decryption of your files with the help of third parties may cause increased price (they add their fee to our) or you can become a victim of a scam.
Fake Explorer.exe Alert Text:
The instruction at 0xe9c71f6c referenced memory at 0x00000000C. The memory could not be read.
Click on Yes in the next window for restore work explorer.exe.
Break down IAM silos like Bitpanda, KnowBe4, and PathAI
Broken IAM isn't just an IT problem - the impact ripples across your whole business.
This practical guide covers why traditional IAM practices fail to keep up with modern demands, examples of what "good" IAM looks like, and a simple checklist for building a scalable strategy.









Comments
DecryptRansom - 8 years ago
I might be able to help decrypt the .wallet if you would like to send over a sample I can analyze it. Send encrypted file and same one from a backup if possible to ransomsample@outlook.com and I will take a look.