Lots of Android ransomware news this week even though Google feels they are pretty rare. Also some updates to tools created by Michael Gillespie (CryptoSearch & ID-Ransomware), a new RaaS, a new PyCL ransomware being distributed via RIG, and ransomware asking for 6 bitcoin ransoms while making fun of USA sanctions on Russia.
Contributors and those who provided new ransomware information and stories this week include: @PolarToffee, @fwosar, @malwrhunterteam, @BleepinComputer, @struppigel, @demonslay335, @malwareforme, @jorntvdw, @FourOctets, @DanielGallagher, @campuscodi, @JAMESWT_MHT, @Seifreed, @JakubKroustek, @kafeine, @FreeBSDfan, @rommeljoven17, @BroadAnalysis, @nyxbone, @Malwarebytes, @Google, @zscaler, and @Lookout.
If you are interested in ransomware or InfoSec, I suggest you follow them on Twitter.
March 25th 2017
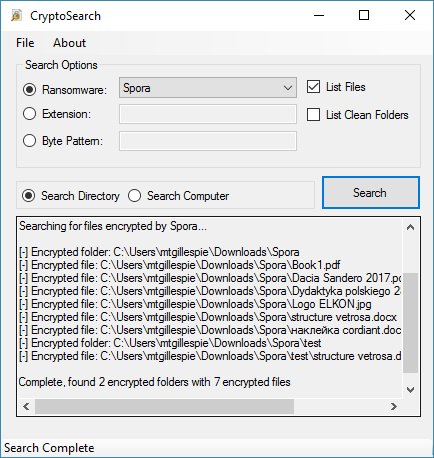
CryptoSearch Updated to Support Files Encrypted by Spora
Michael Gillespie has updated CryptoSearch so that it now supports files encrypted by Spora Ransomware.
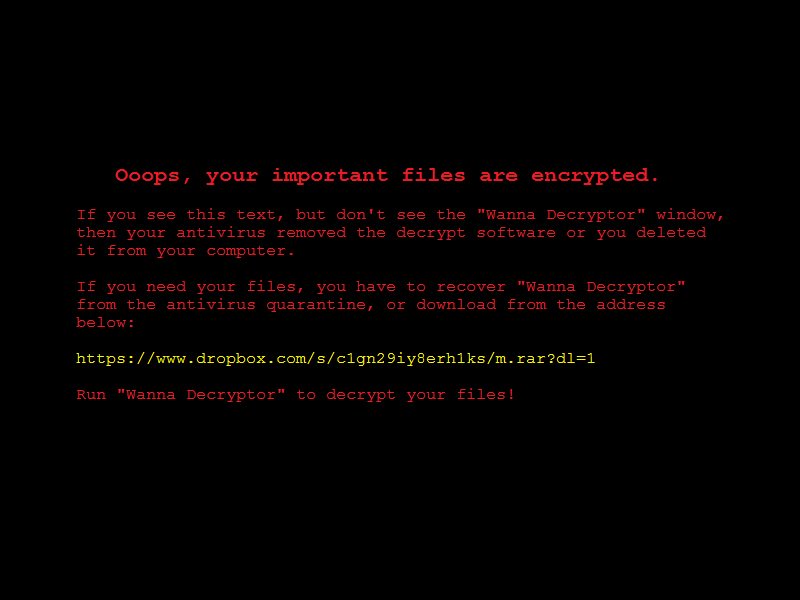
Updated Version of the WCry Ransomware
GData security researcher Karsten Hahn found an updated version of the WCry Ransomware.
Spanish Ransomware Pretends to be a Windows Update
Karsten Hahn found a Spanish ransomware that uses Smart Install Maker and bunch of .vbs scripts to encrypt a computer. When run it pretends to be Windows Update.
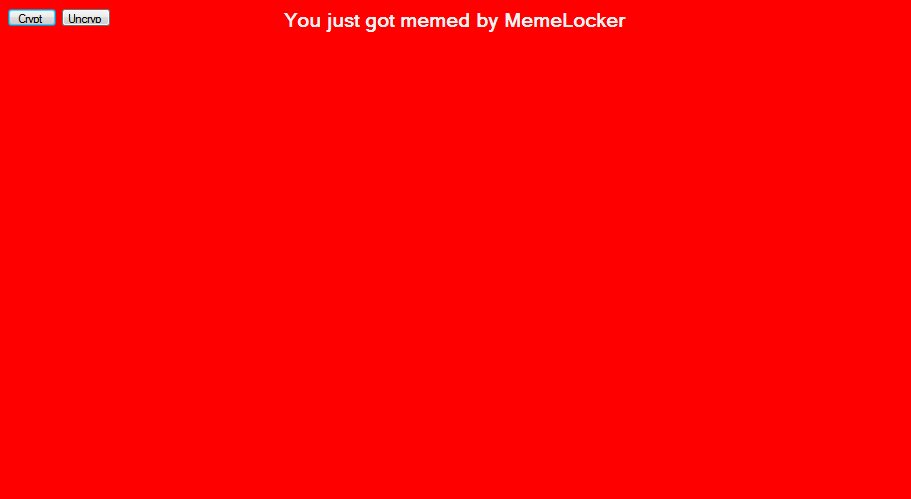
In-Dev MemeLocker Discovered
Karsten Hahn and MalwareHunterteam keeps pumping out the new ransomware infections with the discovery of MemeLocker. This ransomware is in development, but based on its name, I hope we wont see pictures of cats everywhere.
March 28th 2017
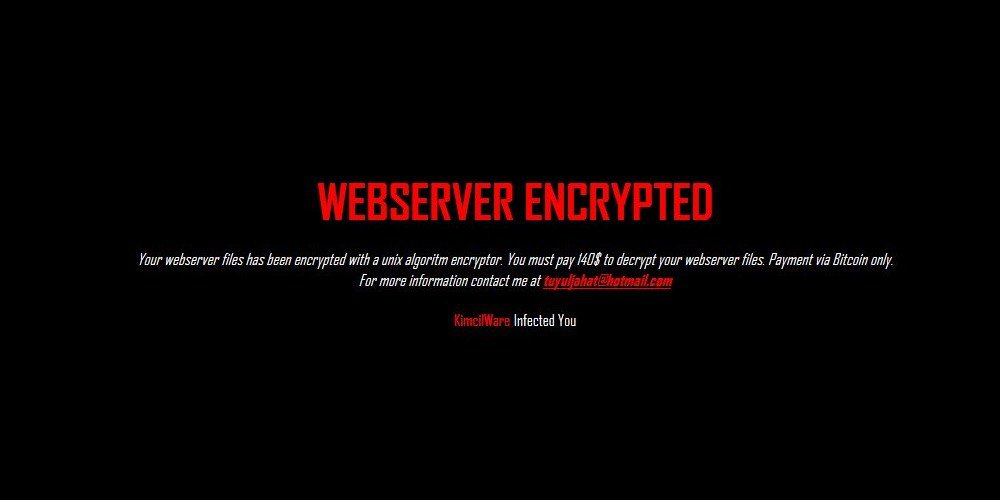
Unskilled Group Behind Many Junk Ransomware Strains
A person or group of malware authors calling themselves "Mafia Malware Indonesia" claimed responsibility for writing a collection of ransomware families that includes threats such as KimcilWare, MireWare, MafiaWare, CryPy, and the recent SADStory and the L0CK3R74H4T ransomware.
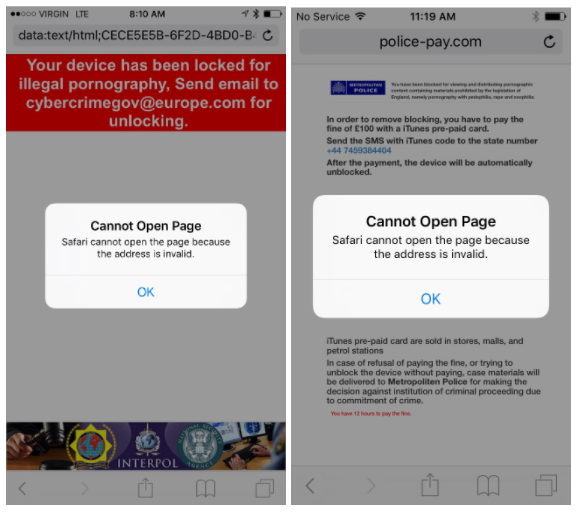
Yesterday's iOS 10.3 Update Bring Safari Ransomware Campaign to an End
According to Lookout, the iOS 10.3 update, released yesterday, has thwarted a screen-locking ransomware campaign that used a bug in mobile Safari to lock users' browsers and demand a ransom paid in iTunes pre-paid gift cards.
PyCL Ransomware Delivered via RIG EK in Distribution Test
This past Saturday security researchers Kafeine, MalwareHunterteam, BroadAnalysis, and David Martínez discovered a new ransomware being distributed through EITest into the RIG exploit kit. As this ransomware was only distributed for one day and does not securely encrypt files, it makes me believe that this may have been a test distribution run.
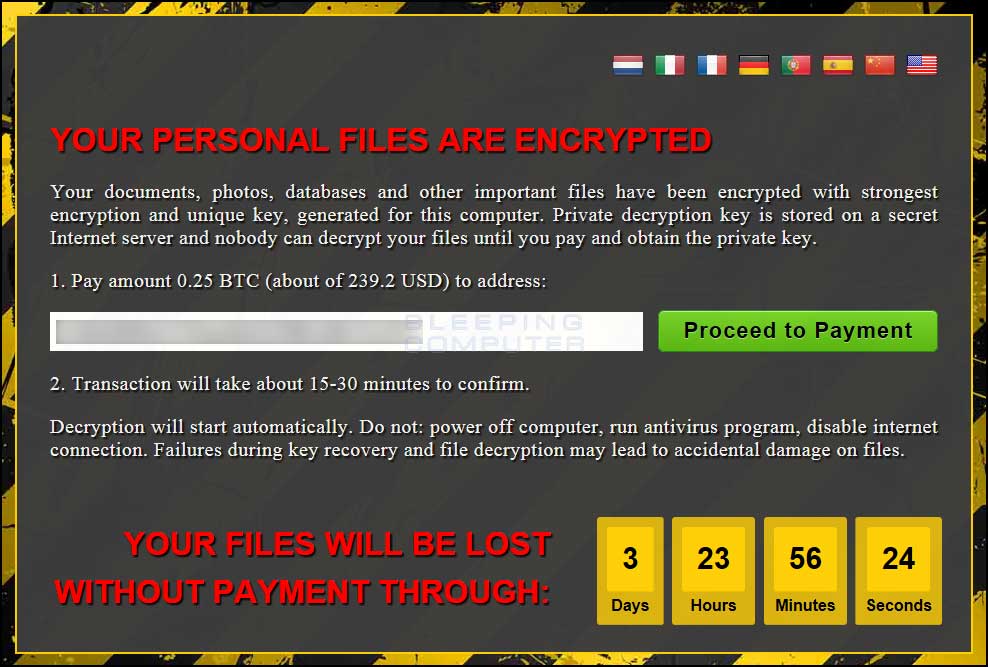
R Ransomware Discovered
R is for Ransomware according to the new ransomware discovered by MalwareHunterTeam. Not sure what the big S is for at the bottom of the ransom page.
Skulls are Creepy According to the AnDROid Ransomware
MalwareHunterTeam discovered another ransomware today called AnDROid. This ransomware appends the .android extension to encrypted files. Even cooler the skull is animated. Such skillz!!

Ransom Hunt Underway for pr0tect Ransomware
Michael Gillespie initiated a ransomware hunt for that uses the .pr0tect and drops a ransom note called READ ME ABOUT DECRYPTION.txt.
March 29th 2017
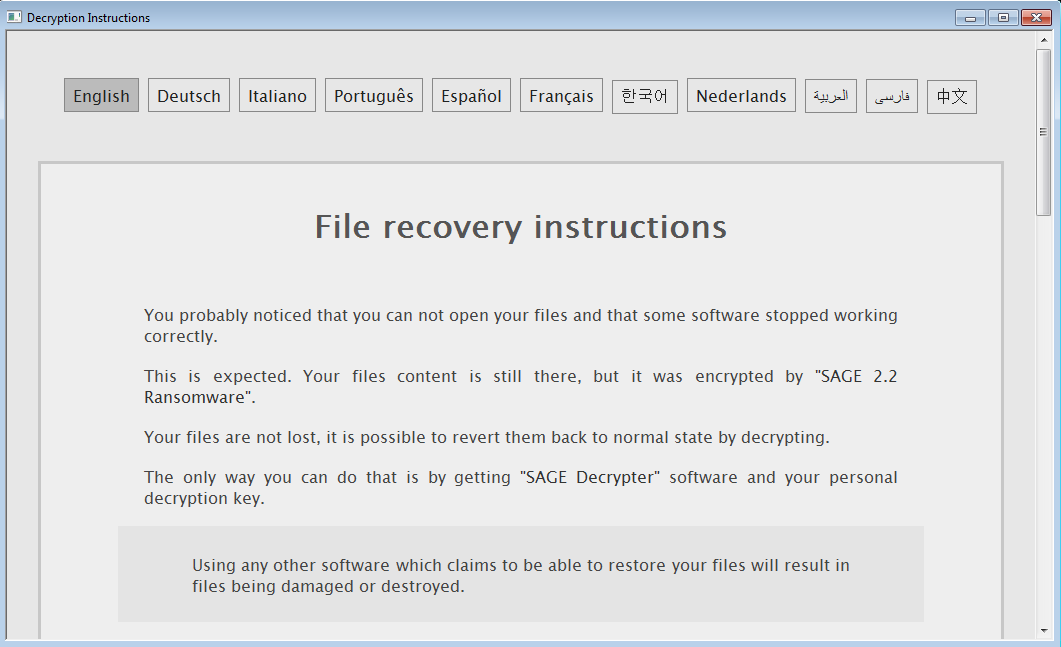
Explained: Sage ransomware
Malwarebytes explains how Sage is yet another ransomware that has become a common threat nowadays. Similarly to Spora, it has capabilities to encrypt files offline. The malware is actively developed and currently, we are facing an outbreak of version 2.2. of this product.
HappyDayzz Sample Found
MalwareHunterTeam found a sample of the HappyDayzz Ransomware. What is interesting about this ransomware is that it uses different encryption algorithms depending on the response from the C2 server.
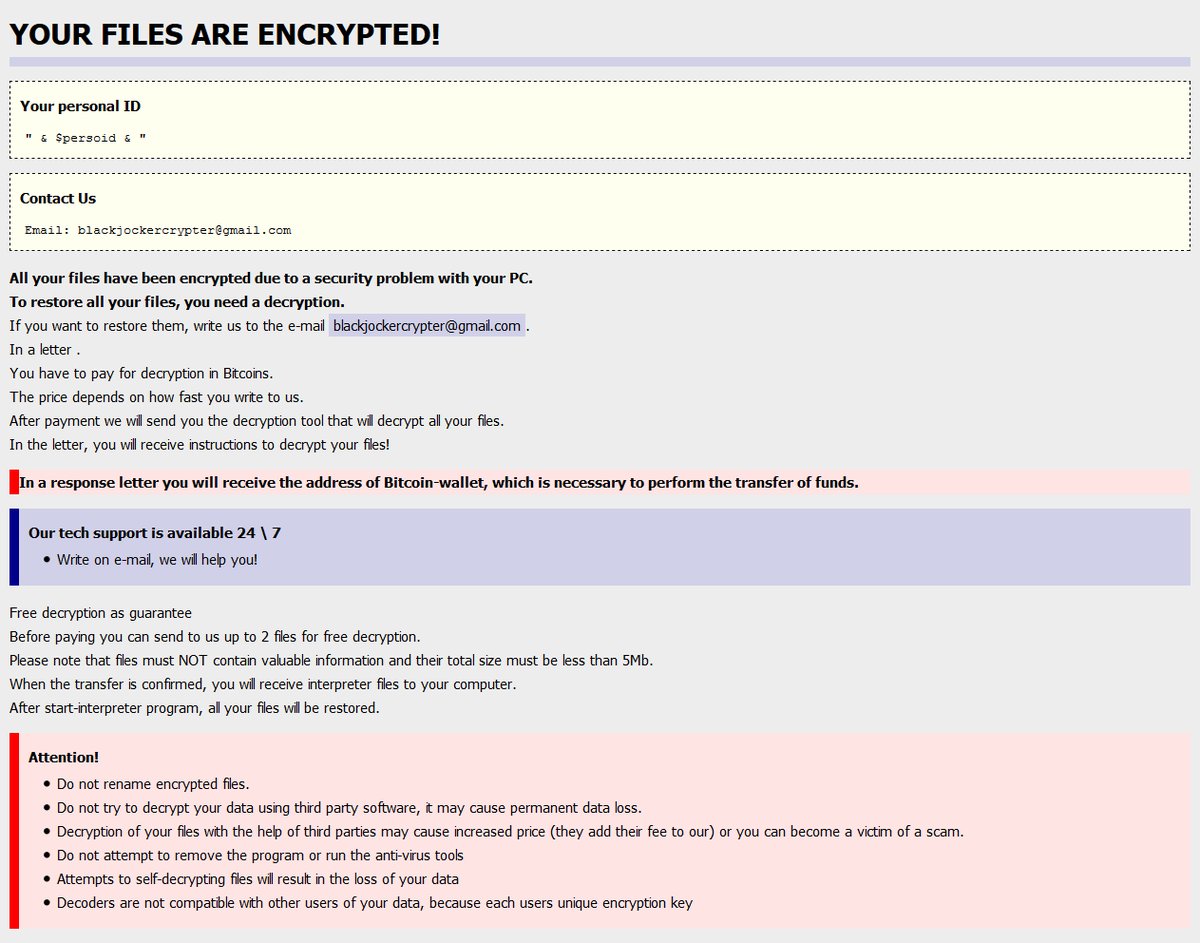
DoNotChange Ransomware Discovered
MalwareHunterTeam found a sample of the DoNotChange Ransomware.
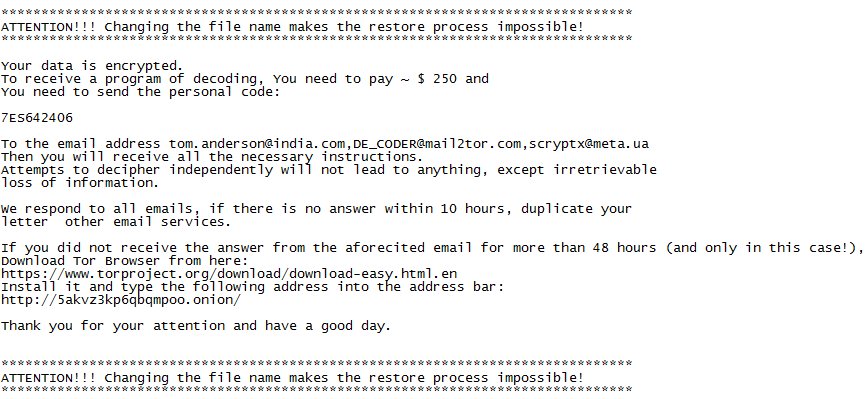
New RaaS called File Frozr Discovered
Rommel Joven discovered a new RaaS called File Frozr.
March 30th 2017
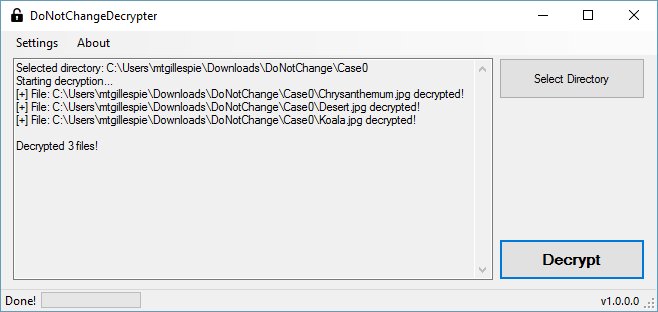
Decryptor for the DoNotChange Ransomware Released
Michael Gillespie released a decryptor for the DoNotChange Ransomware. Instructions can be found here.
Google: Ransomware on Android Is Exceedingly Rare
Android apps spreading ransomware aren't as common as most users and security experts think, says Jason Woloz, Sr. Program Manager for Android Security at @Google.
CryptoSearch Updated to Support Files Encrypted by FadeSoft
Michael Gillespie released an updated version of CryptoSearch that supports files encrypted by FadeSoft.
ID-Ransomware can now Identify Files Encrypted by FadeSoft
Michael Gillespie added support for FadeSoft identification to ID-Ransomware.
March 31st 2017
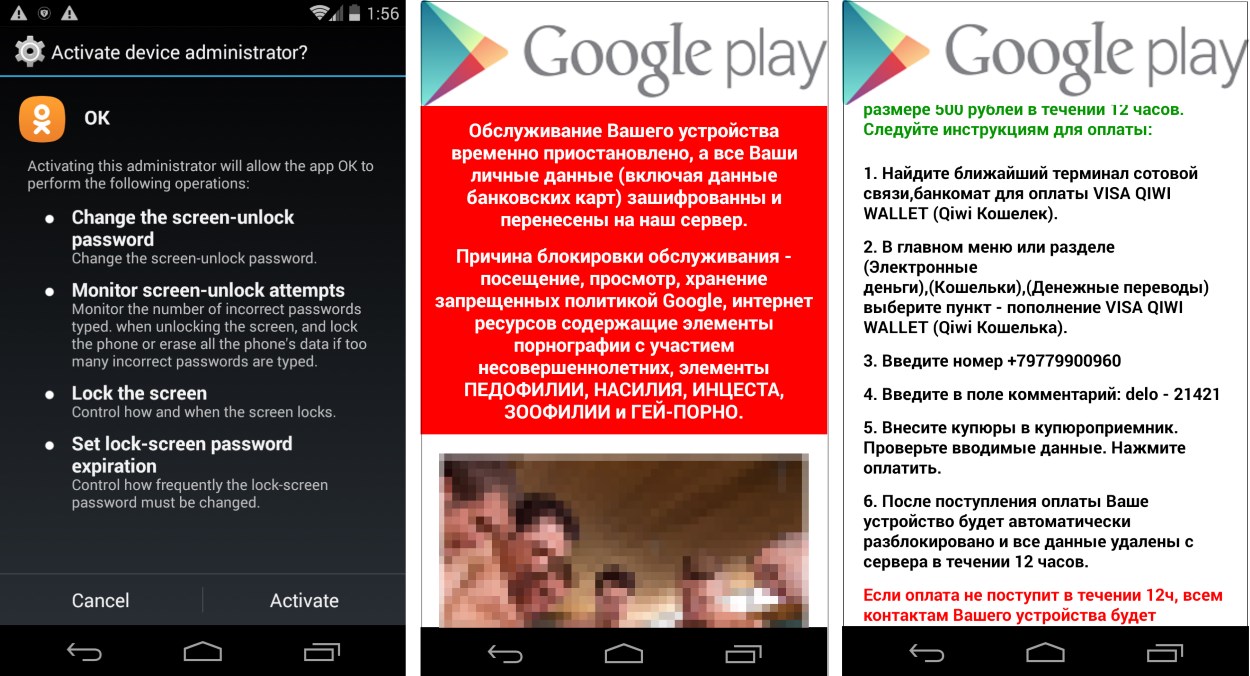
New Android Ransomware Evades All Mobile Antivirus Solutions
Zscaler has spotted a new strain of Android ransomware that could evade detection on all mobile antivirus engines at the time of its discovery. Currently targeting Russian-speaking users, this ransomware lacks basic decryption functionality. This means that users infected with this ransomware version cannot unlock their phones and regain access to their data, even if they pay the ransom.
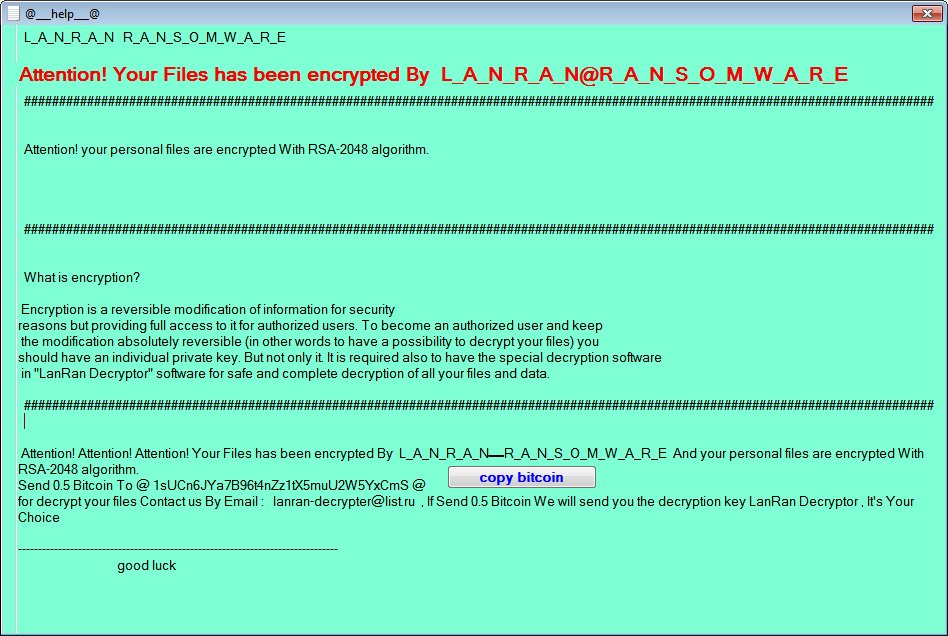
Introducing the Ugly LanRan Ransomware
Don't ransomware developers have any pride anymore? This is obviously not apparent with the LanRan ransomware discovered by Karsten Hahn. This ransomware appears to be in-dev as it just sets the background and displays an ugly ransom lock screen. The contact email for this crapsomware is lanran-decrypter@list.ru.
New Variant of the Fantom Ransomware
MalwareHunterTeam discovered a new variant of the Fantom Ransomware. When I took a look, its quite different then its predecessors. This variant will encrypt files and rename them to a base64 encoded filename with an extension that is based on the time the ransomware started. The extension format is .. An example is Ny5wbmc=.11232323. The ransom note is named in a similar manner with a name like RESTORE-FILES..11232323.hta.
It logs the status of the infection process by retrieving one of these two images hxxp://iplogger.ru/1qzM6.gif or hxxp://iplogger.ru/1wzM6.gif. If its detects the user is from Russia, it terminates the process and deletes the infection from the computer.
New version of CrypVault Found
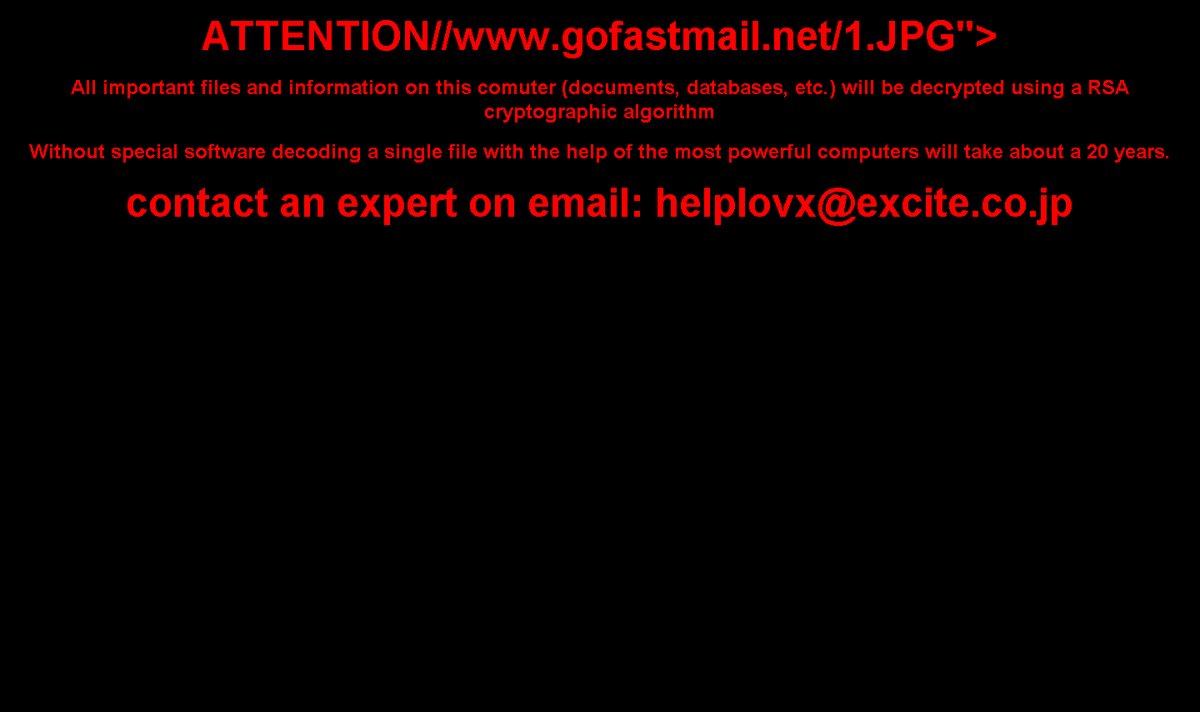
Karsten Hahn found a new version of CrypVault. This variant tells victims to contact helplovx@excite.co.jp.
Ransom Hunt Underway for Cradle Ransomware
Michael Gillespie initiated a ransomware hunt for that uses the extension .cradle and drops a ransom note called _HOW_TO_UNLOCK_FILES_.html.
Sanctions Ransomware Makes Fun of USA Sanctions Against Russia
If you want to know what some ransomware developers think about the USA, you can get a good idea from the ransom note of the Sanctions Ransomware that was released in March. Dubbed Sanctions Ransomware due to the image in the ransom note, the developer makes it fairly obvious how they feel about the USA and their attempts to sanction Russia.

Break down IAM silos like Bitpanda, KnowBe4, and PathAI
Broken IAM isn't just an IT problem - the impact ripples across your whole business.
This practical guide covers why traditional IAM practices fail to keep up with modern demands, examples of what "good" IAM looks like, and a simple checklist for building a scalable strategy.









Comments
Amigo-A - 8 years ago
Grinler
Why You call here CrypVault, if has already be taken in forum BC the name VaultCrypt?
https://www.bleepingcomputer.com/forums/t/570390/vaultcrypt-uses-batch-files-and-open-source-gnupg-to-hold-your-files-hostage/
Amigo-A - 8 years ago
Due to the end of the month, I consider it my duty to present a number of other extortionists that have been added to my digest and some of them have been entered into Ransomware ID, but have yet not been submitted on analysis. I hope so that in the near future they will also be studied in detail and described.
I have a request: about the details found to inform me in PM or in the appropriate support topics.
MacAndChess Ransomware based HiddenTear
https://id-ransomware.blogspot.ru/2017/03/macandchess-ransomware.html
AnonFive aka D3vilH0rn Ransomware based HiddenTear
https://id-ransomware.blogspot.ru/2017/03/anonfive-ransomware.html
Help50 Ransomware from Russian Internet segment
https://id-ransomware.blogspot.ru/2017/03/help50-ransomware.html
Cry9 Ransomware, variant CryptON
https://id-ransomware.blogspot.ru/2017/03/cry9-ransomware.html
French HT aka Putty Ransomware
https://id-ransomware.blogspot.ru/2017/03/french-ht-putty-ransomware.html
NxRansomware Ransomware, Open Source
https://id-ransomware.blogspot.ru/2017/03/nxransomware.html
Amigo-A - 8 years ago
Named above, like Spanish Ransomware, is called CryptoJacky.
http://id-ransomware.blogspot.ru/2017/03/cryptojacky-ransomware.html
He received an upgrade to the 3rd version.
If earlier it had the status of a test crypto-ransomware and encrypted only files with test extensions .xxx, then in the new 3rd version it already encrypts files and spreads like fake Windows-files and other fake programs.