
A ransomware gang is taking extortion to a new level by publicly hacking corporate websites to publicly display ransom notes.
This new extortion strategy is being conducted by Industrial Spy, a data extortion gang that recently began using ransomware as part of their attacks.
As part of their attacks, Industrial Spy will breach networks, steal data, and deploy ransomware on devices. The threat actors then threaten to sell the stolen data on their Tor marketplace if a ransom is not paid.
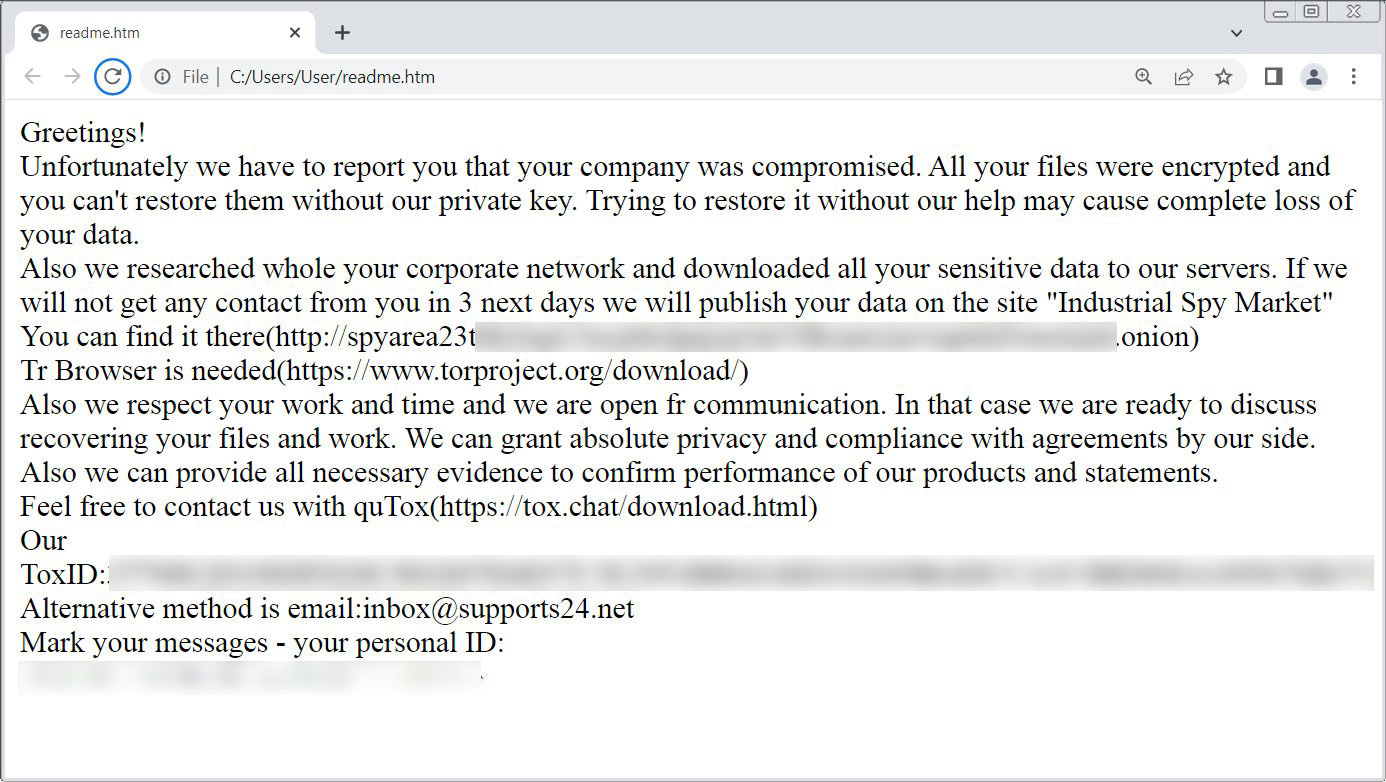
Source: BleepingComputer
Defacing websites as part of data extortion
Today, Industrial Spy began selling data they claim was stolen from a French company named SATT Sud-Est for $500,000.
As first noticed by security researcher MalwareHunterTeam, this attack stands out because the threat actors also hacked the company's website to display a message warning that 200GB had been stolen and would soon be up for sale if the victim did not pay a ransom.
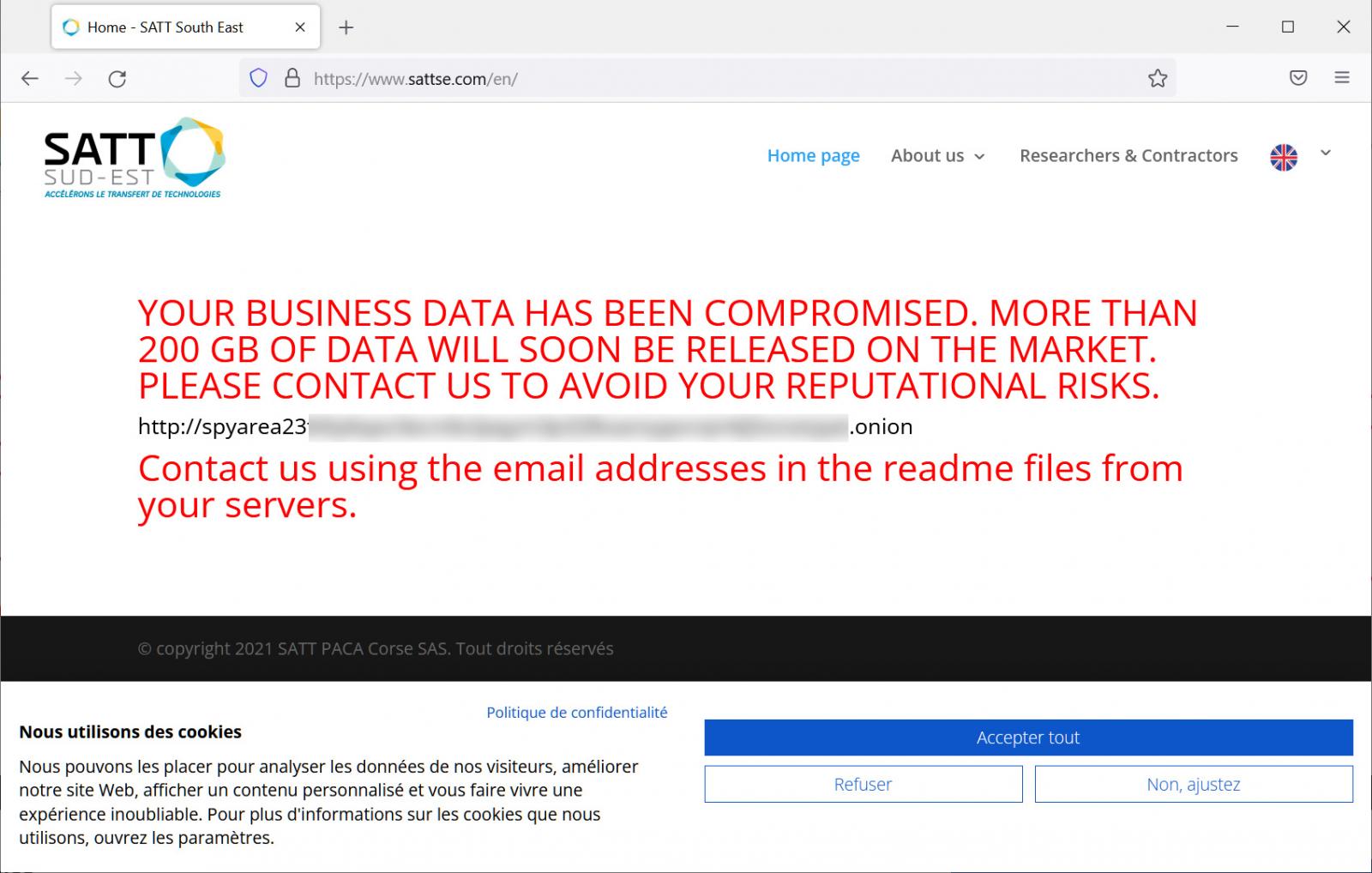
Source: BleepingComputer
When ransomware gangs extort a victim, they typically give them a short window, usually a few weeks, to negotiate and pay a ransom before they start leaking data.
During this negotiation process, the threat actors promise to keep the attack secret, provide a decryption key, and delete all data if a ransom is paid.
After this period, the threat actors will use various methods to increase pressure, including DDoS attacks on corporate websites, emailing customers and business partners, and calling executives with threats.
These tactics are all done privately or with minimal exposure on their data leak sites, which are usually only visited by cybersecurity researchers and the media.
However, this is the first time we have seen a ransomware gang defacing a website to very publicly display a ransom note.
While this tactic is outside the norm, it allows the ransomware gang to apply further pressure on a victim, as it pushes the attack into the spotlight where customers and business partners can more easily see it.
It is not believed, though, that this new tactic will see widespread use as web servers are not typically hosted on corporate networks but rather with hosting providers.
Therefore, threat actors would need to find a vulnerability in the website or gain access to credentials when they steal data from internal networks.
BleepingComputer has contacted SATT Sud-Est to confirm if the attack is legitimate but did not receive a response.
Break down IAM silos like Bitpanda, KnowBe4, and PathAI
Broken IAM isn't just an IT problem - the impact ripples across your whole business.
This practical guide covers why traditional IAM practices fail to keep up with modern demands, examples of what "good" IAM looks like, and a simple checklist for building a scalable strategy.









Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now