
A design flaw in the file transfer interaction between a client host and a MySQL server allows an attacker running a malicious MySQL server to get access to any data the connected client has read access to.
Someone can leverage this issue to retrieve sensitive information from an improperly configured web server that allows connections to untrusted servers, or from database management applications.
Security implications are known
The problem is with the LOAD DATA statement used with the LOCAL modifier, which is referenced as a security risk in the MySQL documentation.
The way the developers explain it, clients receive file-transfer requests from the MySQL server based on the information the client provides in the LOAD DATA statement. A malicious server, however, could reply with a LOAD DATA LOCAL statement and demand any file for which the client has read rights.
“A patched server could in fact reply with a file-transfer request to any statement, not just LOAD DATA LOCAL, so a more fundamental issue is that clients should not connect to untrusted servers,” reads the MySQL documentation.
The same applies with web servers, which act as clients when connecting to a MySQL server. In this case, an attacker can use the flaw to steal the /etc/passwd file, which holds user account records.
Files can be obtained this way only if the server knows their full path. However, this can be learned by requesting the “/proc/self/environ’ file, which provides the environment variable of the running process, thus exposing the home directory and details about the internal folder structure.
Readily available rogue MySQL server
In a discussion on Reddit yesterday sparked by security researcher Willem de Groot, users chimed in with possible scenarios for a malicious MySQL server. Stealing SSH keys and access details for cryptocurrency wallets were first on the list.
According to de Groot, Magecart attacks in October 2018 took advantage of the MySQL flaw to inject into shopping sites code for stealing payment card details at checkout.
Code for a rogue MySQL server has been available on GitHub for the past five years, so it would not come as a surprise if cybercriminals used it in their attacks.
In a blog post last week, de Groot explains how crooks used this flaw to extract sensitive details with the help of Adminer, a tool for managing PostgreSQL and MySQL databases.
The purpose of the attackers appears have been to be stealing a file ('local.xml') where the Magento commerce platform stores its database password.
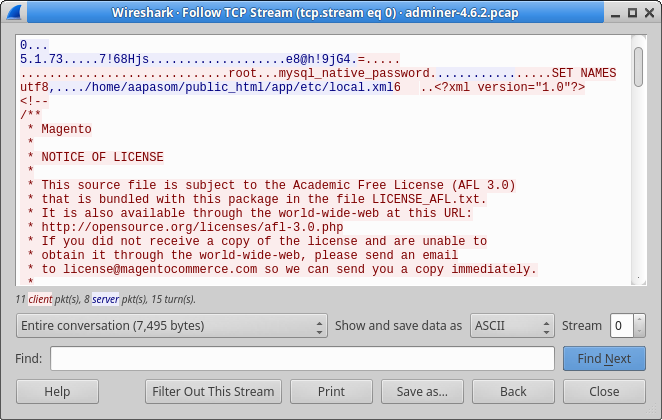
This was possible on websites running a vulnerable version of Adminer (revisions 4.3.1 through 4.6.2 were found to be affected by the bug). Admins should move to a safer version of the product, at least 4.6.3.
Break down IAM silos like Bitpanda, KnowBe4, and PathAI
Broken IAM isn't just an IT problem - the impact ripples across your whole business.
This practical guide covers why traditional IAM practices fail to keep up with modern demands, examples of what "good" IAM looks like, and a simple checklist for building a scalable strategy.









Comments
Dominique1 - 6 years ago
Well, this is disappointing! It's the MySql CLIENT that is vulnerable. The API is so simple compared to a whole OS. How could they not see that? It's beyond me!