
U.S. medical imaging provider SimonMed Imaging is notifying more than 1.2 million individuals of a data breach that exposed their sensitive information.
SimonMed Imaging is an outpatient medical imaging and radiology services provider, including MRI and CT scans, X-ray, ultrasound, mammography, PET, nuclear medicine, bone density, and interventional radiology procedures.
The radiology company operates about 170 medical centers 11 U.S. states, and has an annual revenue of more than $500 million.
Three weeks of unauthorized access
According to the notice shared with the authorities, hackers compromised SimonMed's systems and had access to the company network at the beginning of the year between January 21 and February 5.
SimonMed learned about the breach on January 27, from one of its vendors, who alerted "that they were experiencing a security incident." After starting an investigation, the medical company confirmed the next day suspicious activity on its network.
“Upon discovering we were the victim of a criminal attack, we immediately began an investigation and took steps to contain the situation,", the company states.
The action taken included resetting passwords, multifactor authentication, adding endpoint detection and response (EDR) monitoring, removing third-party vendors' direct access to systems within SimonMed’s environment and its associated tools, and restricted inbound and outbound traffic to trusted connections
The company also notified law enforcement and the services of data security and privacy professionals.
SimonMed did not publicly share exactly what information was stolen by the attackers besides their full names, but considering the types of data medical imaging firms store on their systems, it may include highly sensitive information.
Still, the company underlined that it has no evidence that the accessed information has been misused to conduct fraud or identity theft as of October 10, the day the notice was circulated.
Letter recipients are offered a free-of-charge subscription to identity theft services through Experian.
Medusa claimed the attack
Medusa ransomware announced SimonMed Imaging on its extortion portal on February 7 claiming that it had stolen 212 GB of data.
The hackers also leaked some data, as proof of the attack, consisting of ID scans, spreadsheets with patient details, payment details, and account balances, medical reports, and raw scans.
At the time, the threat actors demanded a ransom payment of $1million and $10,000 for one-day extension before publishing all the stolen files.
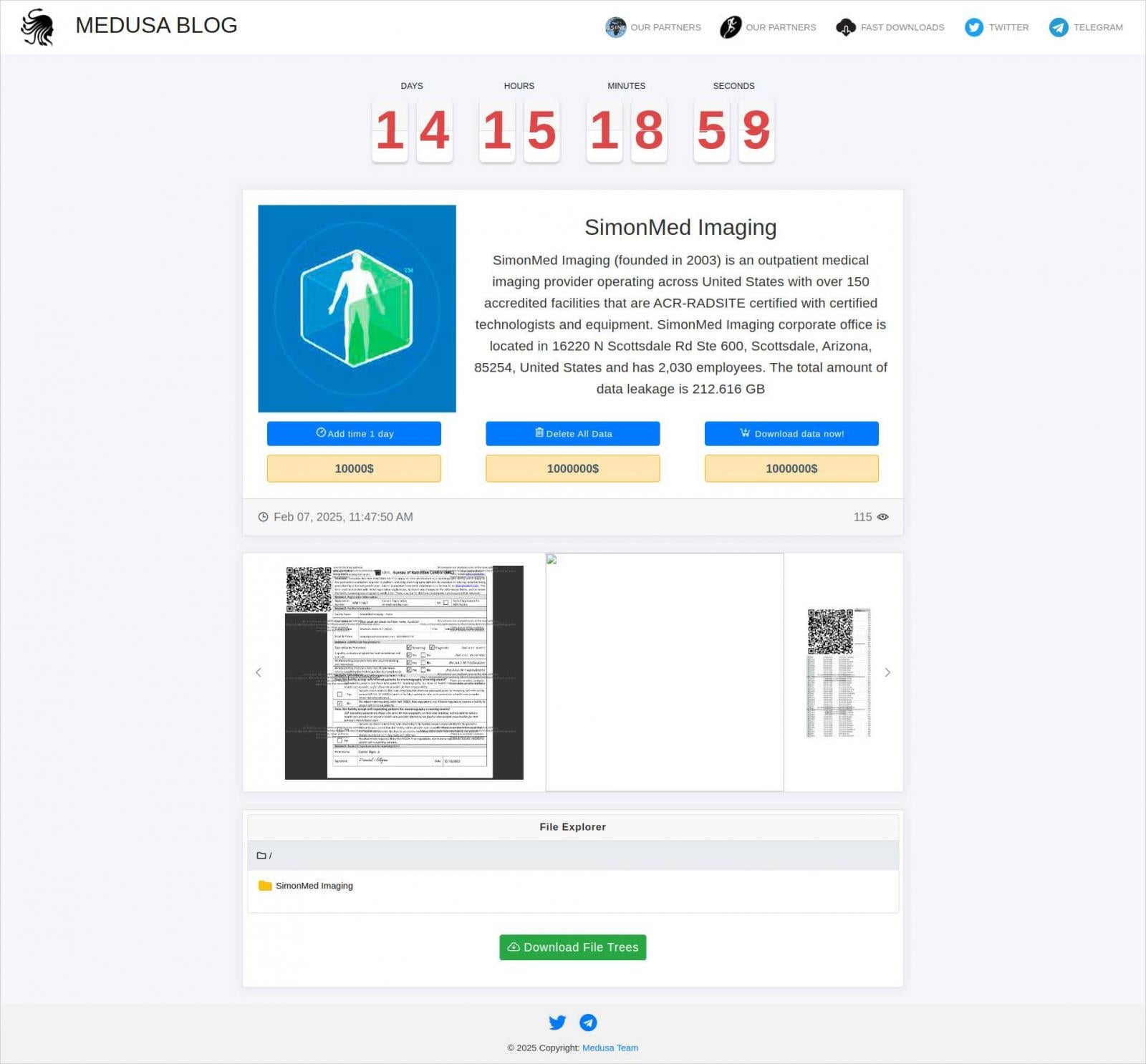
Source: KELA
Currently, SimonMed Imaging is no longer listed on Medusa ransomware's data leak site. This typically suggests that the company negotiated a ransom and paid the hackers.
The Medusa ransomware-as-a-service (RaaS) operation launched in 2023 and gained its infamy with attacks such as the one on the Minneapolis Public Schools (MPS). The gang also targeted Toyota Financial Services.
A joint advisory by the FBI, CISA, and MS-ISAC from March 2025 warned about Medusa ransomware activity, noting that the threat group had impacted over 300 critical infrastructure organizations in the United States.
Break down IAM silos like Bitpanda, KnowBe4, and PathAI
Broken IAM isn't just an IT problem - the impact ripples across your whole business.
This practical guide covers why traditional IAM practices fail to keep up with modern demands, examples of what "good" IAM looks like, and a simple checklist for building a scalable strategy.








Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now