
China-linked cyber-espionage actors tracked as 'Bronze Butler' (Tick) exploited a Motex Lanscope Endpoint Manager vulnerability as a zero-day to deploy an updated version of their Gokcpdoor malware.
The discovery of this activity comes from Sophos researchers, who observed the threat actors exploiting the vulnerability in mid-2025 before it was patched to steal confidential information.
The flaw exploited in these attacks is CVE-2025-61932, a critical request origin verification flaw impacting Motex Lanscope Endpoint Manager versions 9.4.7.2 and earlier. It enables unauthenticated attackers to execute arbitrary code on the target with SYSTEM privileges via specially crafted packets.
Motex released fixes for CVE-2025-61932 on October 20, 2025, with CISA adding the flaw to its Known Exploited Vulnerabilities (KEV) catalog last week, urging federal agencies to patch by November 12, 2025.
Neither the vendor nor CISA shared specific details about the detected exploitation in their bulletins. However, Sophos' latest report indicates that CVE-2025-61932 has been under exploitation by hackers for at least a couple of months.
Bronze Butler leveraged CVE-2025-61932 to deploy the Gokcpdoor malware on targets, which establishes a proxy connection with the attackers' command-and-control (C2) infrastructure.
In the newest version seen in these attacks, Gokcpdoor has dropped support for the KCP protocol and added multiplexed C2 communication.
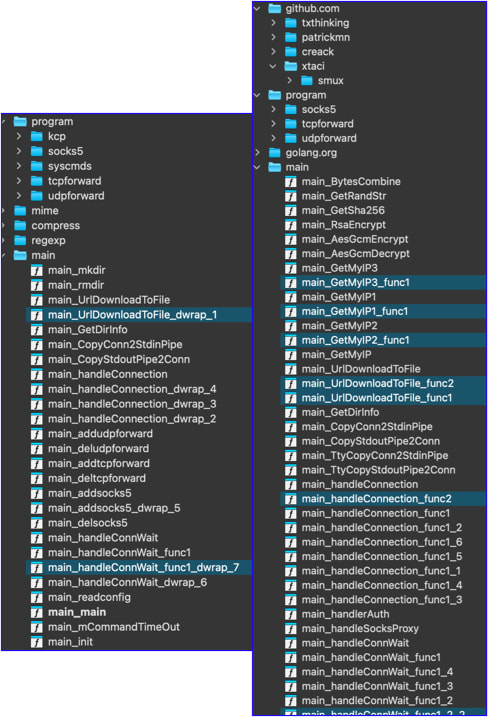
Source: Sophos
Sophos researchers have sampled two variants of the malware, a server implementation that listens for client connections on ports 38000 and 38002, and a client that connects to hard-coded C2 addresses and functions as a backdoor.
In some cases, the attackers employed the Havoc C2 framework instead, but in all instances, the final payload was loaded by OAED Loader and injected into legitimate executables using DLL sideloading for evasion.

Source: Sophos
Sophos also reports that Bronze Butler used the goddi Active Directory dumper, Remote Desktop, and the 7-Zip archiver tool for data exfiltration.
The hackers likely used cloud-based storage services as exfiltration points, with Sophos noting access to io, LimeWire, and Piping Server.
Organizations using Lanscope Endpoint Manager are recommended to upgrade their clients to a version that addresses CVE-2025-61932. Currently, there are no workarounds or mitigations for the vulnerability, so patching is the only recommended action.
Break down IAM silos like Bitpanda, KnowBe4, and PathAI
Broken IAM isn't just an IT problem - the impact ripples across your whole business.
This practical guide covers why traditional IAM practices fail to keep up with modern demands, examples of what "good" IAM looks like, and a simple checklist for building a scalable strategy.








Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now