
A vulnerability in multiple versions of OxygenOS, the Android-based operating system from OnePlus, allows any installed app to access SMS data and metadata without requiring permission or user interaction.
OnePlus, a subsidiary of Oppo, is a Shenzhen-based consumer electronics maker known for developing high-end smartphones at competitive pricing. While other major Chinese brands like Huawei and Xiaomi aren’t available in the U.S., OnePlus devices are officially available in the country.
The flaw, tracked as CVE-2025-10184, and discovered by Rapid7 researchers, is currently unpatched and exploitable. The Chinese OEM failed to respond to Rapid7’s disclosures to this day, and the cybersecurity company published the technical details along with a proof-of-concept (PoC) exploit.
Source of the problem
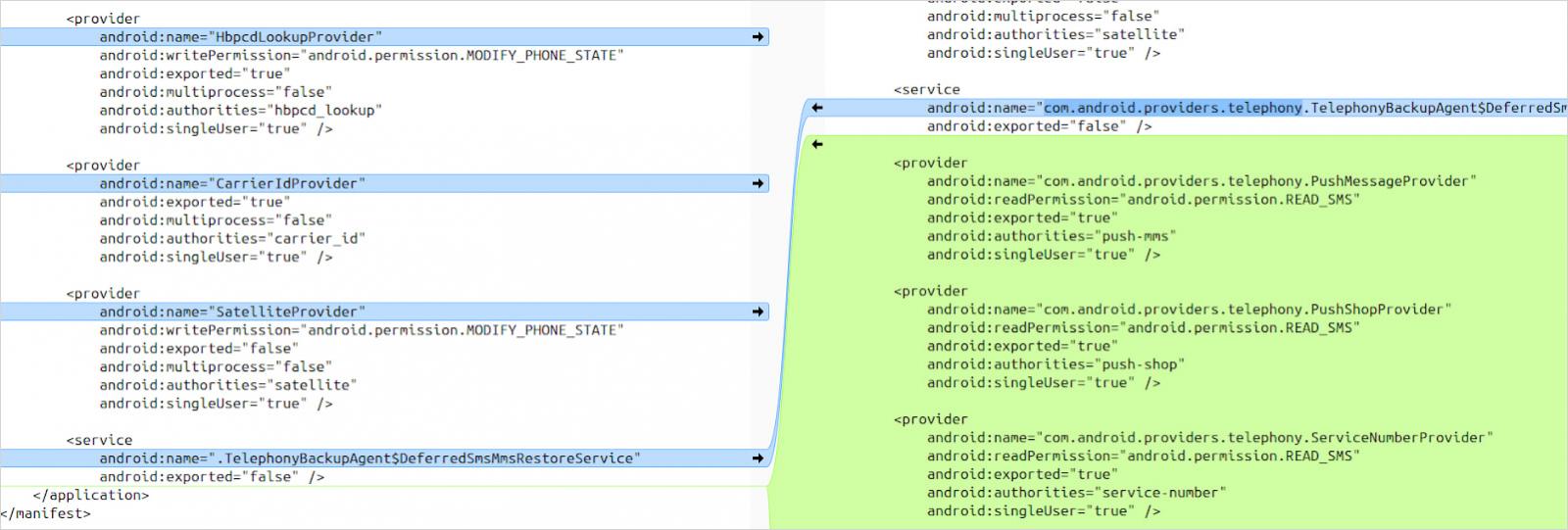
The problem arises from OnePlus changing the stock Android Telephony package to introduce additional exported content providers like PushMessageProvider, PushShopProvider, and ServiceNumberProvider.
The manifest for these providers does not declare a write permission for ‘READ_SMS,’ leaving it open to any app by default, even those that don’t have SMS permissions.
Source: Rapid7
To make matters worse, client-supplied inputs aren’t sanitized, allowing “blind SQL injection” that could reconstruct SMS content from the device database, bruteforcing it one character at a time.
“By using an algorithm to repeat this process for each character in each row returned by the sub query, it’s possible to exfiltrate the database content, using the return value from the update method as an indicator of true/false,” describes Rapid7 in the report.
So, while the read permission for SMS is correctly set, the write permission isn’t, allowing the inference of SMS content when certain prerequisites are met:
- Exposed table must already contain at least one row, so update() can return a non-zero “rows changed” result.
- The provider must allow insert() so an attacker can create a dummy row to operate on if the table is empty.
- The sms table must be in the same SQLite database file because the injected subquery must be able to reference it.
Source: Rapid7
Impact and response
The issue impacts all versions of OxygenOS from 12 to the latest one, which is 15, which is the latest, built on top of Android 15.
Rapid7 researchers tested and confirmed vulnerability on OnePlus 8T and 10 Pro, running various OxygenOS versions and Telephony package numbers, but noted that their list is almost definitely non-exhaustive.
“While the build numbers above [on the table] are specific to the test devices, as the issue affects a core component of Android, we expect this vulnerability to affect other OnePlus devices running the above versions of OxygenOS, i.e., it does not seem to be a hardware-specific issue,” explained Rapid7.
| Device / Model | Package version | OxygenOS version | Build Number |
| OnePlus 8T / KB2003 | 3.4.135 | 12 | KB2003_11_C.3 |
| OnePlus 10 Pro 5G / NE2213 | 14.10.30 | 14 | NE2213_14.0.0.700(EX01) |
| OnePlus 10 Pro 5G / NE2213 | 15.30.5 | 15 | NE2213_15.0.0.502(EX01) |
| OnePlus 10 Pro 5G / NE2213 | 15.30.10 | 15 | NE2213_15.0.0.700(EX01) |
| OnePlus 10 Pro 5G / NE2213 | 15.40. | 15 | NE2213_15.0.0.901(EX01) |
The researchers tried to contact OnePlus to share their findings on May 1 and followed up on alternative email addresses multiple times until August 16.
After receiving no response to seven separate communication attempts, the security firm publicly disclosed the details for CVE-2025-10184.
Shortly after publication of Rapid7's report, OnePlus acknowledged the disclosure and said they have launched an investigation into the problem.
BleepingComputer has contacted OnePlus to request a comment, but we are still awaiting a response.
Until a patch is made available, it is recommended to keep the number of installed apps on your OnePlus device to a minimum, only trust reputable publishers, and switch from SMS-based two-factor authentication to OTP apps like Google Authenticator.
Since SMS isn’t properly isolated on OnePlus devices, sensitive communications should only occur on end-to-end encrypted apps.
Update 9/25 - OnePlus sent BleepingComputer the following statement:
"We acknowledge the recent disclosure of CVE-2025-10184 and have implemented a fix. This will be rolled out globally via software update starting from mid-October. OnePlus remains committed to protecting customer data and will continue to prioritize security improvements." - OnePlus spokesperson
Break down IAM silos like Bitpanda, KnowBe4, and PathAI
Broken IAM isn't just an IT problem - the impact ripples across your whole business.
This practical guide covers why traditional IAM practices fail to keep up with modern demands, examples of what "good" IAM looks like, and a simple checklist for building a scalable strategy.








Comments
XSp - 3 months ago
Yeah, it pretty much confirms my suspicion about OnePlus...
I had a OnePlus 3 way back several years ago, when a major security flaw that allowed attackers to exfiltrate a ton of very sensitive information out of several models happened, right close to another report that their phones were already collecting a truckload of sensitive information without disclosure.
The whole CyanogenOS getting killed and OxygenOS replacing it, that whole fracas being fresh in mind.
Look up for OnePlus BlueBorne, and OnePlus data collection... easy to find enough reports on both cases.
The response from the company, which was fairly active back then, was not only tone deaf, it seemed to me that no one there really understood the implications and the severity of the problems identified. This attitude of not responding properly, not giving enough credit and seriousness to the problems found, or even not understanding the implications of such problems appearing on their devices offering weird workarounds and treating it as if it was something acceptable in terms of security and privacy practices raised all alarms for me personally.
Occasional vulnerabilities and weak security practices I can even understand, but the exchange I had with them just seemed to show something more deeply ingrained. Can't say if it's malicious, or just incompetence, but either way it's not what you'd expect from a company building a device that will be handling so much sensitive personal information.
That was when I decided and wrote a direct response to them that I'd never buy anything else from the company. Seems to me they didn't change much since then.
Not that you have many brands to chose from these days that do things differently, particularly in my local market, but you can only eliminate the stuff you know for sure isn't working, and keep trying for next "least worse" unfortunately.
Just to be clear though, this has nothing to do with the company being Chinese subsidiary, related to Oppo, or whatever. My question here is purely technical. In fact, I think the constant "spy for CCP" mudslinging is counter productive and unnecessary, particularly when so many western and western allied companies are pulling the exact same crap for the exact same problems - bad security practices and advertiser money.
It's just that when these seem to be systemic, and there doesn't seem to be any sincere interest coming from those companies to improve their internal procedures to solve things like that, it needs to be called out for what it is, regardless of politics, ideology, or country of origin.
In any case, I'll continue not recommending stuff from the company, just as much as I don't recommend stuff from say, Lenovo for incidents and responses that happened way back with the Superfish stuff. I just see these companies repeatedly being called out for poor or flawed practices, but they keep pumping money for online advertisement via influencers and tech bloggers, instead of actually adopting better practices. It's a vicious cycle.
Drags - 3 months ago
Like the US of A is any different, thanks to the "lovely" patriot act.
At least OnePlus was one of the few companies, back in the day at least, where you could still put another ROM on the phone, without loosing warranty, and it was issue solved.
Lenovo is still better than Dell, in my opinion, so each to their own.