
With Twitter hackers, 10/10 vulnerabilities, and Cloudflare outages this week, thankfully ransomware has been pretty slow this week.
The biggest news is Orange confirming they were hit with a Nefilim ransomware attack and business customer's data being stolen. We also saw an interesting ransomware that utilizes the Age encryption tool.
Other than that, it has mostly been smaller attackers and new ransomware variants released.
Contributors and those who provided new ransomware information and stories this week include: @demonslay335, @VK_Intel, @struppigel, @malwrhunterteam, @fwosar, @BleepinComputer, @LawrenceAbrams, @Seifreed, @serghei, @DanielGallagher, @PolarToffee, @FourOctets, @jorntvdw, @Ionut_Ilascu, @malwareforme, @JakubKroustek, @xiaopao80087499, @fbgwls245, @Amigo_A_, @campuscodi, and @360TotalSec.
July 12th 2020
New Matrix Ransomware variant
xiaopao found a new Matrix Ransomware variant that appends the .AL8P extension and drops a ransom note named Readme_AL8P.rtf.
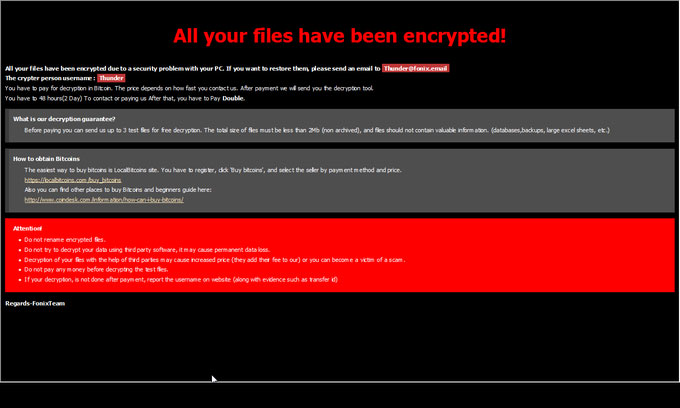
New FonixCrypter variant
dnwls0719 found a new FonixCrypter variant that appends the .XINOF extension.
July 13th 2020
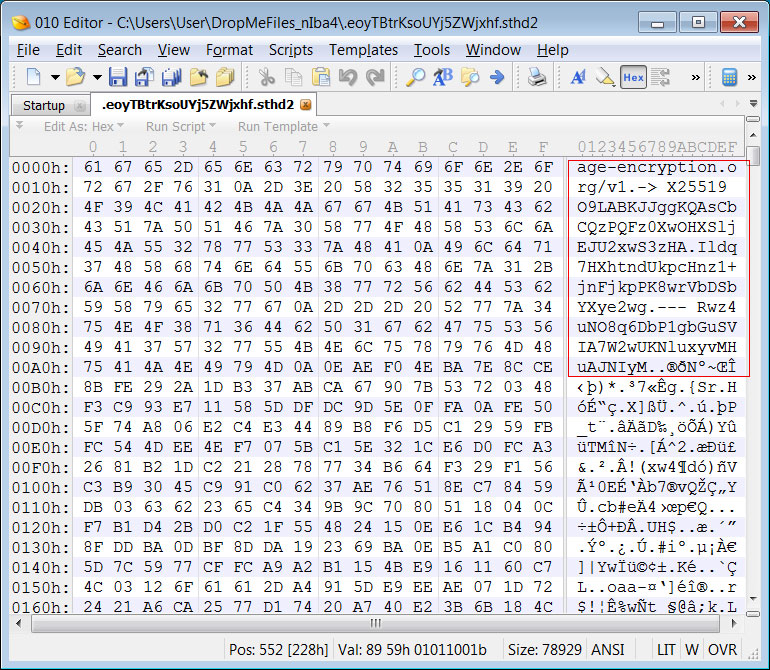
New AgeLocker Ransomware uses Googler's utility to encrypt files
A new and targeted ransomware named AgeLocker utilizes the 'Age' encryption tool created by a Google employee to encrypt victim's files.
New REPL STOP Ransomware variant
Michael Gillespie found a new STOP Ransomware variant that appends the .repl extension to encrypted files.
New DATA and SMPL Dharma Ransomware variants
Jakub Kroustek found two new variants of the Dharma Ransomware that append either the .data or .smpl extension to encrypted files.
The chance of data being stolen in a ransomware attack is greater than one in ten
The data theft and name-and-shame tactics initiated by Maze in November 2019 and subsequently adopted by multiple other groups have blurred the line between ransomware attack and data breach.
July 14th 2020
New ZBW Makop Ransomware variant
Michael Gillespie found a new Makop Ransomware variant that appends the .zbw extension and drops a ransom note named readme-warning.txt.
July 15th 2020
New FastWind Ransomware hunt
Michael Gillespie is looking for a new ransomware that appends the .FastWind extension and drops a ransom note named ransomware.txt.
FlowEncryption file encryption
Recently, 360 Security Center has detected that a file encryption virus in the form of a hoax has appeared on the network. In view of the encrypted file suffix of the virus is named “.flowEncryption”, we named it “flowEncryption file encryption virus”.
July 16th 2020
Orange confirms ransomware attack exposing business customers' data
Orange has confirmed to BleepingComputer that they suffered a ransomware attack exposing the data of twenty of their enterprise customers.
New Matrix Ransomware variant
Michael Gillespie found a new Makop Ransomware variant that appends the .BNFD extension to encrypted files.
July 17th 2020
Cloud provider stopped ransomware attack but had to pay ransom demand anyway
Blackbaud, a provider of software and cloud hosting solutions, said it stopped a ransomware attack from encrypting files earlier this year but still had to pay a ransom demand anyway after hackers stole data from the company's network and threatened to publish it online.
New SPARE Dharma Ransomware variant
Michael Gillespie found a new Dharma Ransomware variant that appends the .spare extension to encrypted files.
New Maoloa Ransomware variant
Michael Gillespie found a new Maoloa Ransomware variant that appends the .Globeimposter-Alpha865qqz extension to encrypted files.
New REPL STOP Ransomware variant
Michael Gillespie found a new STOP Ransomware variant that appends the .kuus extension to encrypted files.
That's it for this week! Hope everyone has a nice weekend!
Break down IAM silos like Bitpanda, KnowBe4, and PathAI
Broken IAM isn't just an IT problem - the impact ripples across your whole business.
This practical guide covers why traditional IAM practices fail to keep up with modern demands, examples of what "good" IAM looks like, and a simple checklist for building a scalable strategy.








Comments
GrandJunction - 5 years ago
https://www.hybrid-analysis.com/
https://0patch.com/patches.html
https://old.reddit.com/r/micropatching/
https://www.digitaldefense.com/professional-services/frontline-social-test/
https://www.comparitech.com/blog/information-security/common-phishing-scams-how-to-avoid/
GrandJunction - 5 years ago
Ports that one should consider blocking on both TCP / UDP
135-139, 445, 1433, 3000-7000, 7070, 63333
https://www.bleepingcomputer.com/news/security/ebay-port-scans-visitors-computers-for-remote-access-programs/
https://raw.githubusercontent.com/blocklistproject/Lists/master/ransomware.txt
https://ubackup.com/anti-ransomware/how-to-block-port-445-in-windows-3889.html
https://www.dummies.com/computers/operating-systems/windows-10/how-to-block-ransomware-in-windows-10-with-controlled-folder-access/
https://blog.malwarebytes.com/security-world/business-security-world/2018/08/protect-rdp-access-ransomware-attacks/