
A faulty component in the latest CrowdStrike Falcon update is crashing Windows systems, impacting various organizations and services across the world, including airports, TV stations, and hospitals.
The glitch is affecting Windows workstations and servers, with users reporting massive outages that took offline entire companies and fleets of hundreds of thousands of computers.
According to some reports, emergency services in the U.S. and Canada have also been impacted.
Workaround for CrowdStrike glitched update
For the past few hours, users have been complaining about Windows hosts being stuck in a boot loop or showing the Blue Screen of Death (BSOD) after installing the latest update for CrowdStrike Falcon Sensor.
The security vendor acknowledged the issue and published a technical alert explaining that its engineers “identified a content deployment related to this issue and reverted those changes.”
“Symptoms include hosts experiencing a bugcheck\blue screen error related to the Falcon Sensor,” CrowdStrike says in the tech alert.
The company revealed that the culprit is a Channel File, which contains data for the sensor (e.g. instructions). Since it is just a component of the update for the sensor, this type of file can be addressed individually without removing the Falcon Sensor update.
For those already affected, CrowdStrike provides the following workaround steps:
- Boot Windows into Safe Mode or the Windows Recovery Environment
- Navigate to the C:\Windows\System32\drivers\CrowdStrike directory
- Locate the file matching “C-00000291*.sys”, and delete it.
- Boot the host normally.
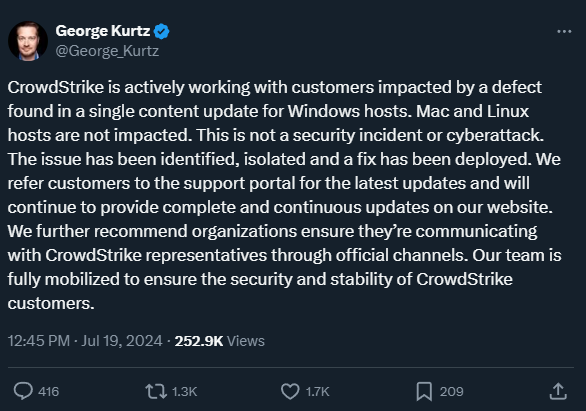
George Kurtz, the President and CEO of CrowdStrike announced a few minutes ago that the company “is actively working with customers” and confirmed that the problems are caused “by a defect found in a single content update for Windows hosts.”
“We further recommend organizations ensure they’re communicating with CrowdStrike representatives through official channels. Our team is fully mobilized to ensure the security and stability of CrowdStrike customers” - George Kurtz
CrowdStrike’s CEO says that a fix is available and advises customers to access the support portal for the latest updates.
source: George Kurtz
In an updated statement, CrowdStrike says that "the problematic channel file [C-00000291*.sys" with timestamp of 0409 UTC] has been reverted" and the good version of it is C-00000291*.sys with timestamp of 0527 UTC or later.
The company also provides two options to address the issue in cloud and virtual environments, one variant being to roll back to a snapshot before 04:09 UTC. The second option is the following seven-step procedure:
- Detach the operating system disk volume from the impacted virtual server
- Create a snapshot or backup of the disk volume before proceeding further as a precaution against unintended changes
- Attach/mount the volume to to a new virtual server
- Navigate to the %WINDIR%\System32\drivers\CrowdStrike directory
- Locate the file matching “C-00000291*.sys”, and delete it.
- Detach the volume from the new virtual server
- Reattach the fixed volume to the impacted virtual server
Outage hits airlines and hospitals worldwide
By the time of the correction, though, many large organizations across multiple verticals had already been affected.
Some reports say that CrowdStrike’s update impacted some 911 emergency service agencies in the state of New York (EMS, police, fire department), Alaska, and Arizona, as well as 911 services in parts of Canada.
A 911 telecommunicator in Illinois said that they were “working off of paper until things come back.”
There also reports that the health hotline in Catalonia, Spain, is impacted and authorities are asking citizens not to call 061 unless there is an emergency.
Dutch broadcasting organization NOS said that the glitch created disruptions at Schiphol Airport and “forced several flights to be grounded” (operated by KLM and Transavia).
Melbourne Airport said that it was experiencing “a global technology issue which is impacting check-in procedures for some airlines.” The most affected are passengers departing internationally via Jetstar and Scoot airlines.
A few hours ago, in the latest update, the Zurich Airport says that "flights with destination Zurich that are already in the air are still allowed to land," no aircrafts "are currently taking off for Zurich Airport," and there are no departures to the U.S.
Furthermore, there are delays and cancellations and passengers of individual airlines must be checked in manually.
Other airports affected are in Berlin, Barcelona, Brisbane, Edinburgh, Amsterdam, and London.
In the U.S., the Federal Aviation Administration received requests to assist multiple airlines (American Airlines, United, Delta) with ground stops until "a technical issue impacting IT systems" is resolved.
On JFK and LaGuardia airports in the U.S., flights have been grounded due to outages from the CrowdStrike update, leaving passengers stranded.
Some hospitals in the Netherlands - Scheper in Emmen, Slingeland Hospital in Achterhoek, and emergency posts in Hoogeveen and Stadskanaal were also impacted.
In Barcelona, the Terrassa University Hospital and the Catalan Oncology Institute experienced issues earlier today due to the CrowdStrike issue but have started to return to normal activity.
In the U.S., Bellevue hospital in New York and NYU Langone Hospital are also impacted.
On Friday morning, multiple television stations and news outlets, such as Sky News and ABC suffered disruptions as computers crashed.
A large number of users started to spill their frustration in Reddit comments about tens and even hundred of thousands of computers crashing after CrowdStrike’s update and the impact on their companies:
Malaysia here, 70% of our laptops are down and stuck in boot, HQ from Japan ordered a company wide shutdown
210K BSODS all at 10:57 PST....and it keeps going up...this is bad....
Workstations and servers here in Aus... fleet of 50k+ - someone is going to have fun.
Failing here is Australia too. Our entire company is offline
Same here in OZ. Entire company is down.
Half the company down. Somehow it has hit our AWS servers also. Major service downtime for our customers
Entire org and trading entities down here. Half of IT are locked out.
Seeing major issues here in NZ at the moment, company wide outage impacting servers and workstations.
Supporting Philippines and China Locations. All experiencing the same as well
Despite a fix being deployed and CrowdStrike providing a workaround for Windows hosts already crashing, companies will feel the effects from the issue for a while.
Admins are going to have a long weekend, especially with computer fleets of tens or hundreds of thousands of computers, employees working remotely, off-premise data centers, or cloud environments where booting in safe mode is not an option.
Update [July 19, 09:59 ET]: Article edited to include mitigation details for cloud and virtual environments.
Break down IAM silos like Bitpanda, KnowBe4, and PathAI
Broken IAM isn't just an IT problem - the impact ripples across your whole business.
This practical guide covers why traditional IAM practices fail to keep up with modern demands, examples of what "good" IAM looks like, and a simple checklist for building a scalable strategy.








Comments
No1gr8 - 1 year ago
Being in at 1 am fixing servers is bad enough, and then the CrowdStrike CEO is like no big deal, just do the patch is salt in the wound.
dvblystone - 1 year ago
I am getting alerts from quite a few providers that they are being affected by this. Not going to be a good day for them or for us. I am not a Crowdstrike customer but I am feeling the effects of it.
jpramirez - 1 year ago
That surely will cause not only a backlash on CrowdStrike but also on any major vendor like them, and with reason, for something like this to happen all quality controls and test failed, development chain is broken.
dvblystone - 1 year ago
It is called testing in production. LOL
powerspork - 1 year ago
Microsoft does it all the time. Eventually, someone else looks at their methods and decide its a great idea.
DyingCrow - 1 year ago
This ramps up the concept of "domino effect" considerably?
dvblystone - 1 year ago
I think they need to stop saying that this is not a cybersecurity incident. They are a cybersecurity company with a cybersecurity product that caused an incident. Therefore it IS a cybersecurity incident.
KennethLeik - 1 year ago
No it is not. A cybersecurity incident would be if there was some vulnerability being exploited. This is just the same as any software developer adding a bugged version that makes Windows go into BSOD. The effect might be the same regarding unavailability, But the incident has to be classified as software bug incident, not cybersecurity!
dvblystone - 1 year ago
You are right, it is not a true cybersecurity incident. However, the more you say and try to deny something, the more you look guilty for it. That phrase should have never been used.
We can debate what should have been done or not done until the cows come home. Nothing will change what happened. I am hearing that the issue is being successfully resolved. I just hope that this does not ruin their reputation as a company and put them out of business.
Gh0st_Mav - 1 year ago
It depends on how you choose to view it. From the perspective of Crowdstrike customers, this incident has affected the availability of their services and going by the core tenets of cybersecurity (CIA:Confidentiality-Integrity-Availability), it can be classified as a cybersecurity incident. Its not necessarily a breach, but in the grand scheme of things as it concerns cybersecurity, availability was affected. From the perspective of Crowdstrike, it can be seen as a process issue. Someone dropped the ball along the lines of the operational chain.
DIMMReaper_ - 1 year ago
"I think they need to stop saying that this is not a cybersecurity incident. They are a cybersecurity company with a cybersecurity product that caused an incident. Therefore it IS a cybersecurity incident."
No this was a Cybersecurity company that rolled out an update without proper testing. It's not an incident is... stupidity that lead to likely the biggest IT Outage in the world, ever. The good thing is though, CS is a great product, it doesn't make me think less of them. They will fix this and make sure it never happens again. There's been other incidents like this with other providers, just not to this scale because everyone is drinking the CS Kool-aid, because it lets us sleep at night. Just sucked that it came right after a Cogent outage Monday, and a Microsoft issue Thurs/Friday. Between all that and having Covid... I'm beat lol.
itspoffy - 1 year ago
The impact is that of an attack regardless if it was self inflicted. Crowdstrike does a great job. The company I'm at now does not use it, but there is a saying, 1 oh s&&t destroys 1000 attaboys. I hope they recover and the backlash is limited.
CamboSoupBoy - 1 year ago
Or 10 million ;P
NoneRain - 1 year ago
This 'oh sh1t' just affected 8.5 million devices that needs manual intervention. Hope they made 'attaboys' enough....
NoneRain - 1 year ago
CrowdStrike really struck the crowd this time
ZeroYourHero - 1 year ago
I don't think Microsoft will come out of this unscathed. From what I see there are numerous design problems with WinRE that techs are enjoying right now.
johnlsenchak - 1 year ago
Workers are getting fired at " Crowd Strike" you know it's coming
ZeroYourHero - 1 year ago
Oh, that was Carl's fault. He's new.
__TheWatchman__ - 1 year ago
The general consensus at the moment is that the outage was caused by human error in the update that was pushed out. If this is the case, this incident should not be considered a "cyber security" incident even though it is related to a cyber security vendor.
If foul play is involved, then the incident can be considered as an insider threat case and should be considered a "cyber security" incident.
My question is - if the cause was merely human error, how did the update pass through all of CrowdStrike's rigorous quality control tests without any issues, and yet was able to cause a global outage that affected, as I understand it, all versions of the Windows operating system currently in use.
JohnC_21 - 1 year ago
Not all versions. Although I wouldn't exactly call Windows 3.1 current.
https://www.digitaltrends.com/computing/southwest-cloudstrike-windows-3-1/
stevansky - 1 year ago
"how did the update pass through all of CrowdStrike's rigorous quality control tests" I can see their quality control chief in their sombrero now, "Quality control tests? We don't need no stinkin' quality control tests!" as they approve the update and head home for the weekend.
Elastoer - 1 year ago
I wonder how long it will be before the US Congress holds hearings about this?
Syra - 1 year ago
The recent CrowdStrike outage has had significant impacts globally, affecting everything from airlines to hospitals. As detailed in the latest blog post, this incident underscores the importance of robust cybersecurity testing and rapid response strategies. For a deeper dive into the technical aspects and potential preventative measures, check out full analysis here:https://sennovate.com/why-the-crowdstrike-incident-is-not-solely-crowdstrikes-fault/