
Using a network of honeypots, researchers from McAfee examined the tools and tactics used by the Sodinokibi Ransomware (REvil) affiliates to infect their victims with ransomware and compromise other machines on the network.
As part of the Sodinokibi ransomware-as-a-service, ransomware executables are tagged with an affiliate's IDs and sub IDs in order to track who infected the victim and which affiliate should earn a commission for a payment.
At the same time, these affiliate IDs allow researchers to track their behavior as well and paint a picture of how they infect their victims and spread laterally throughout a network.
Monitoring the attackers
In a new report shared with BleepingComputer before publication, the McAfee Advanced Threat Research team used a global network of Remote Desktop Protocol (RDP) honeypots was used to track the activities of three Sodinokibi affiliate groups.
These affiliates, known as Group 1, affiliate #34, and affiliate #19, all initially compromised a system via RDP and then use this foothold to try and compromise the rest of the network.
To attempt to spread laterally throughout the network, all of the affiliates used mass port scanning tools to find accessible RDP servers and then used the NLBrute RDP brute forcing tool with custom password lists to try and gain access to servers.
Affiliate #34 and #19, though, showed more skillful tactics such as using custom Mimikatz batch files to harvest network credentials credentials, custom scripts to erase Windows event viewer logs, and the creation of hidden users.
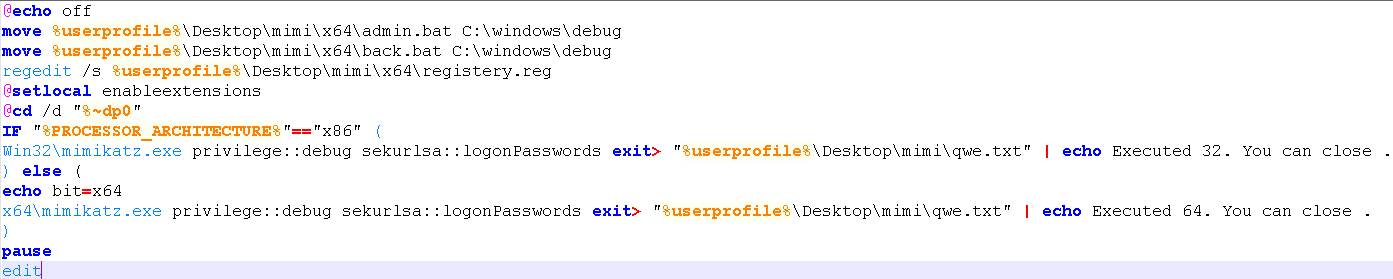
Affiliate #19 appears to be the most skillful, or thorough, as McAfee saw them attempt to utilize local exploits to gain administrative access on a compromised computer. By gaining access to an administrative account, the affiliate could more easily push out and execute the ransomware on other machines on the Windows domain.
In addition to the Sodinokibi Ransomware payload, Affiliate #34 also dropped cryptomining payloads such as MinerGate and XMRig.
From one of the MinerGate configuration files, McAfee was able to learn the email address used by one of the attackers and track it down to a possible Persian-speaking member of an RDP hacking crew.
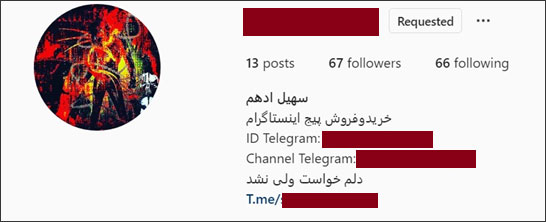
"Based on our analysis, this individual is likely part of some Persian-speaking credential cracking crew harvesting RDP credentials and other types of data. The individual is sharing information related to Masscan and Kport scan results for specific countries that can be used for brute force operations."
Everything search engine deployed to index documents
An interesting program that was deployed by affiliate #34 is the Everything file indexing software.
When installed, Everything will index all of the file and folder names found on the computer so that a user can quickly search for files based on an entered keyword. It is also possible to search for content within the indexed files, though at a much slower speed.
While McAfee was unable to monitor what searches were performed, they did state that a full index of the filesystem was completed.
"Unfortunately we haven’t got information that the actor was searching for specific keywords we did see a complete index of the filesystem," McAfee's John Fokker, Head of Cyber Investigations, told BleepingComputer via email.
BleepingComputer believes that the Everything software was installed so that the attackers could use it to search for sensitive files based on their names.
For example, if files contain the words "secret", "password", "bank accounts", "classified", "military", "10-Q", "10-K", etc, the attackers could then exfiltrate these files in their unencrypted form in order to steal trade secrets, steal financial information, get insider information for stock trades, or threaten to release the documents unless a ransom is payed.
While not common, in the past stolen data of a sensitive nature has been used to threaten victims to make a payment or the data would be publicly released.
The use of Everything as part of a ransomware deployment is an interesting tactic and one that all enterprise customers should be concerned about due to the increased risk of data theft.
Break down IAM silos like Bitpanda, KnowBe4, and PathAI
Broken IAM isn't just an IT problem - the impact ripples across your whole business.
This practical guide covers why traditional IAM practices fail to keep up with modern demands, examples of what "good" IAM looks like, and a simple checklist for building a scalable strategy.








Comments
woody188 - 6 years ago
Ransomware is an obfuscation technique with possible benefits. Data exfil is the true goal.