
The number of victims paying ransomware threat actors has reached a new low, with just 23% of the breached companies giving in to attackers' demands.
With some exceptions, the decline in payment resolution rates continues the trend that Coveware has observed for the past six years.
In the first quarter of 2024, the payment percentage was 28%. Although it increased over the next period, it continued to drop, reaching an all-time low in the third quarter of 2025.
One explanation for this is that organizations implemented stronger and more targeted protections against ransomware, and authorities increasing pressure for victims not to pay the hackers.
“Cyber defenders, law enforcement, and legal specialists should view this as validation of collective progress,” Coveware says.
“The work that gets put in to prevent attacks, minimize the impact of attacks, and successfully navigate a cyber extortion — each avoided payment constricts cyber attackers of oxygen.”
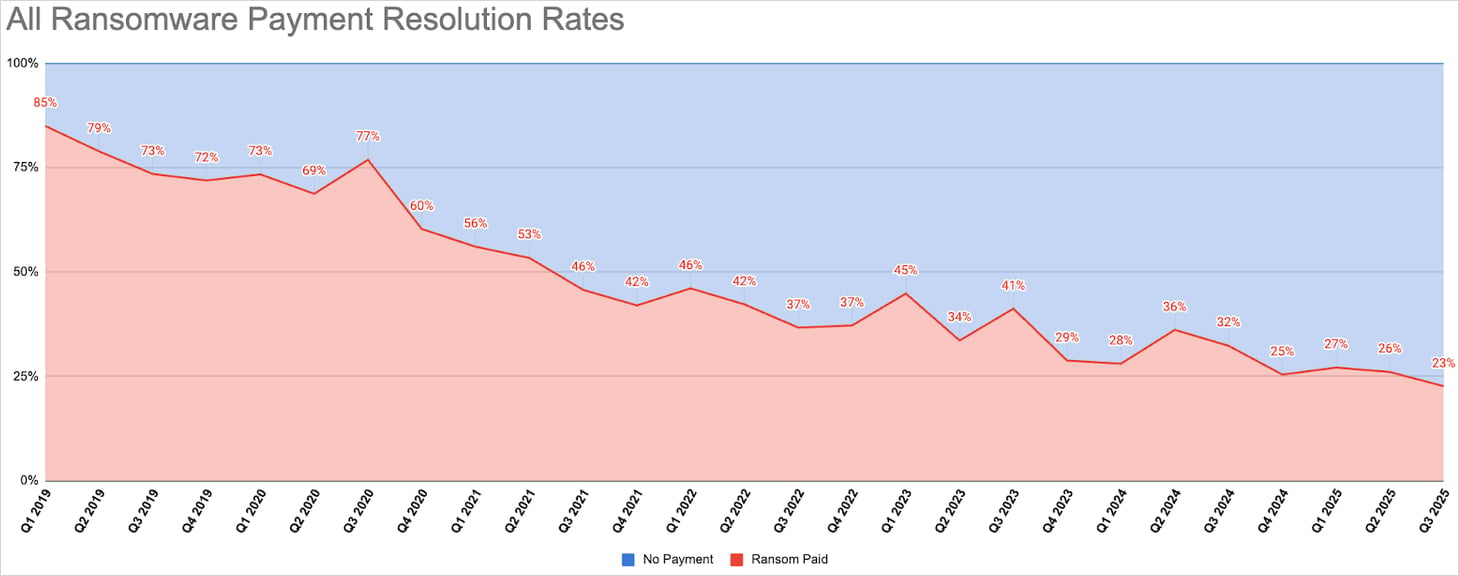
Source: Coveware
Over the years, ransomware groups moved from pure encryption attacks to double extortion that came with data theft and the threat of a public leak.
Coveware reports that more than 76% of the attacks it observed in Q3 2025 involved data exfiltration, which is now the primary objective for most ransomware groups.
The company says that when it isolates the attacks that do not encrypt the data and only steal it, the payment rate plummets to 19%, which is also a record for that sub-category.
The average and median ransomware payments fell in Q3 compared to the previous quarter, reaching $377,000 and $140,000, respectively, according to Coveware.
The shift may reflect large enterprises revising their ransom payment policies and recognizing that those funds are better spent on strengthening defenses against future attacks.
The researchers also note that threat groups like Akira and Qilin, which accounted for 44% of all recorded attacks in Q3 2025, have switched focus to medium-sized firms that are currently more likely to pay a ransom.
Another notable trend over the past year is the rise of remote access compromise as the leading attack vector, alongside a significant increase in the use of software vulnerabilities.
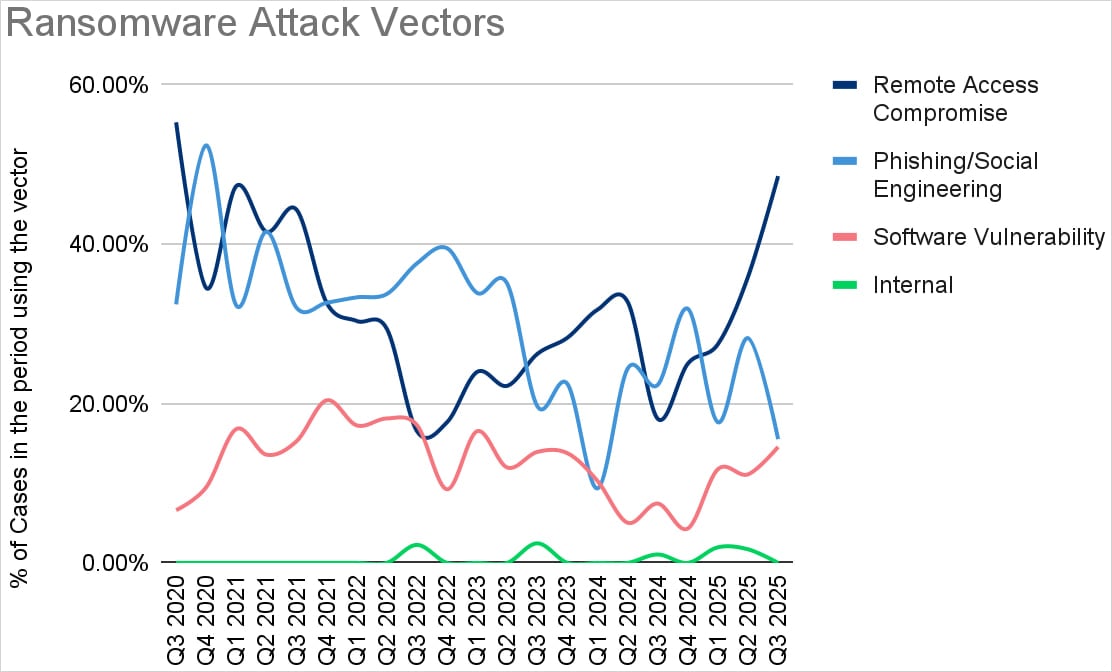
Source: Coveware
Coveware believes that diminishing profits are driving ransomware gangs to greater precision and that larger enterprises will be increasingly targeted as profit margins continue to shrink.
As larger organizations have strengthened their security posture, threat actors are likely to rely more on social engineering and insider recruitment, offering large bribes for help gaining initial access.
Break down IAM silos like Bitpanda, KnowBe4, and PathAI
Broken IAM isn't just an IT problem - the impact ripples across your whole business.
This practical guide covers why traditional IAM practices fail to keep up with modern demands, examples of what "good" IAM looks like, and a simple checklist for building a scalable strategy.









Comments
NoneRain - 2 months ago
Thanks God.
Directors are "discovering" that paying big bucks for criminals is not a good choice, even when they don't get leaked online.