
Image: Le Figaro
French daily newspaper Le Figaro exposed roughly 7.4 billion records containing personally identifiable information (PII) of reporters and employees, as well as of at least 42,000 users.
The data was exposed by an unsecured database owned by Le Figaro and containing over 8TB of data which was publicly accessible because of a misconfigured Elasticsearch server.
Le Figaro's site is the most visited news site in France with an audience of more than 23 million monthly unique visitors according to stats provided by Médiamétrie / NetRatings.
Out in the open since February 2020
The database discovered by a Safety Detectives team lead by security researcher Anurag Sen contained records with info on newly registered new accounts between February and April 2020, as well as records of pre-existing user accounts that were logging in during that period.
For pre-existing users, the database was only leaking PII data, while in the case of new records login credentials were also left out in the open for anyone to collect.
Based on the researchers' findings, the PII data exposed included emails, full names, home addresses including countries of residence and ZIP codes, passwords in plain text hashed using MD5, as well as IP addresses and tokens used for access to internal servers.
All this information was stored in Le Figaro's database in the form of API logs of the newspaper's mobile and desktop websites.
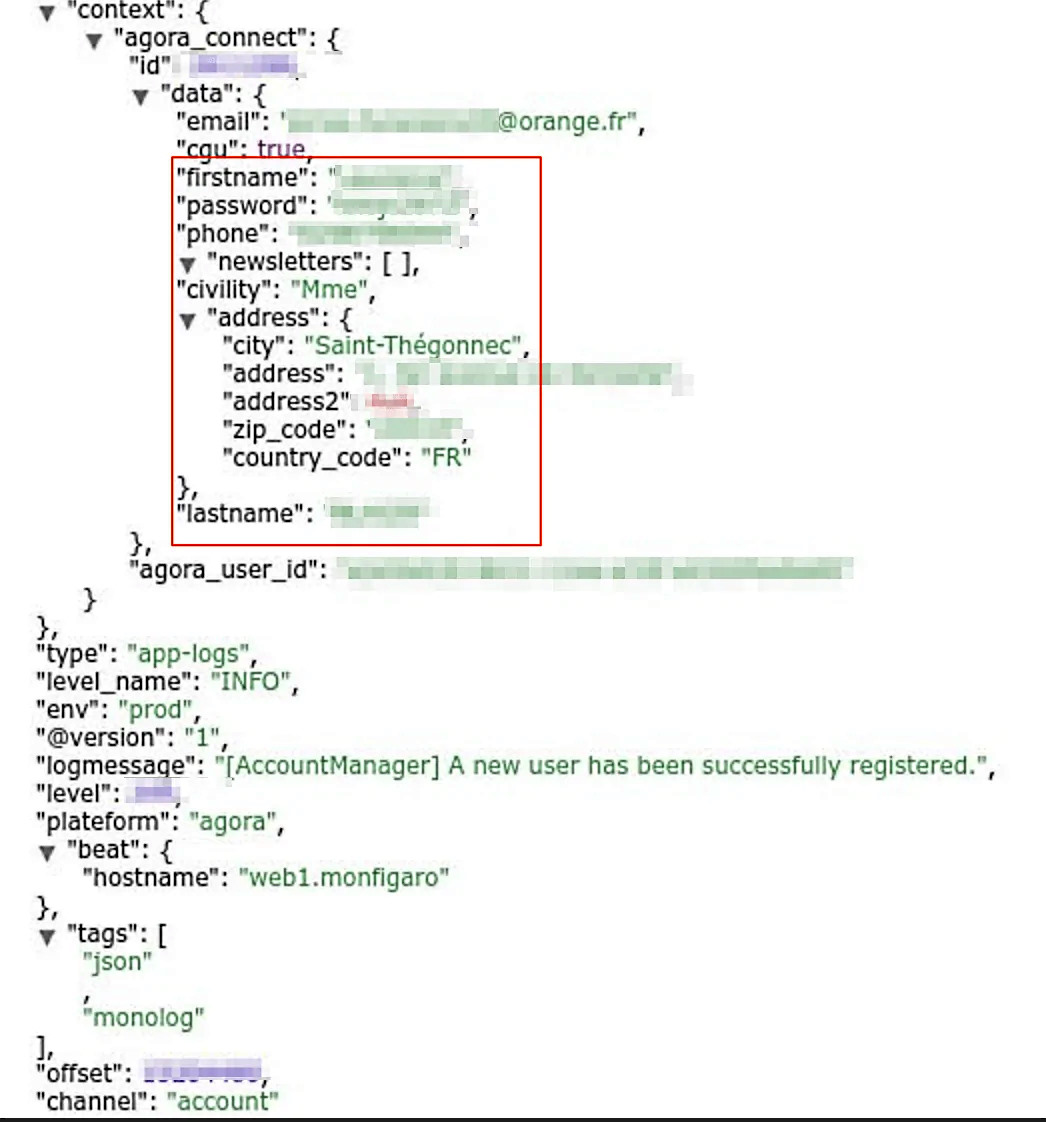
While the database's structure made it hard to estimate the exact number of users, journalists, and employees whose data was exposed, the researchers estimated that at least 42,000 records were exposed by this leaky Elasticsearch server.
Network technical info also exposed
Besides the API logs containing PII data, the database also contained a lot of technical logs with information on Le Figaro's backend servers and other info that could make it easier for a threat actor who would've obtained the info to launch a successful attack against the newspaper.
These included potential access to admin accounts, communication protocols, SQL query errors, and logs of network traffic between multiple Le Figaro servers.
To confirm that the database was indeed owned by the French newspaper, the researchers created a test user account on Le Figaro which later showed up within the API logs as a newly created user.
"Finally, and most worrisome of all, the database was completely exposed to the public – with no password required to access it," they explain. "Anyone with the knowledge of the database’s IP address could have gained access."
The data exposed by this misconfigured Elasticsearch cluster could be used by attackers for identity theft and fraud, for credential phishing attacks on other sites, to launch very convincing spear-phishing attacks against Le Figaro's users, journalists, and employees, and as a starting point for a cyberattack on Le Figaro's network and backend servers.
Securing ElasticSearch clusters
Although Elastic Stack's core security features are now free since May 2019 as announced by Elastic NV, publicly-accessible, misconfigured and unsecured ElasticSearch servers are regularly being spotted by security researchers who scour the web for unprotected databases.
While Elastisearch servers should only be accessible on a company's local network so that only the database's owners can access them as explained by ElasticSearch's dev team back in December 2013, this rarely happens.
Elastic NV recommends database admins to secure their ElasticSearch stack by "encrypting communications, role-based access control, IP filtering, and auditing," by setting up passwords for built-in users, and by properly configuring the clusters before deployment.
Break down IAM silos like Bitpanda, KnowBe4, and PathAI
Broken IAM isn't just an IT problem - the impact ripples across your whole business.
This practical guide covers why traditional IAM practices fail to keep up with modern demands, examples of what "good" IAM looks like, and a simple checklist for building a scalable strategy.









Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now