
An unsecured MongoDB instance belonging to health insurance marketing website MedicareSupplement.com was discovered online last month containing as many as 5 million records. The data cache included personal information as well as health details.
MedicareSupplement.com is owned and run by TZ Insurance Solutions. Its purpose is to help individuals find a suitable Medigap insurance plan, a form of private health insurance that covers costs the original Medicare does not. According to its Facebook page, the service helped more than 400,000 people find the right insurance plan.
The way the website works is by providing potential customers a comparison of the health plans available outside Medicare. Users have to enter personal information in an online form to get a free quote.
MongoDB instance for marketing leads
The public database was uncovered on May 13 by researchers from Compariteh working with Bob Diachenko, a security professional experienced in locating unprotected sensitive data online.
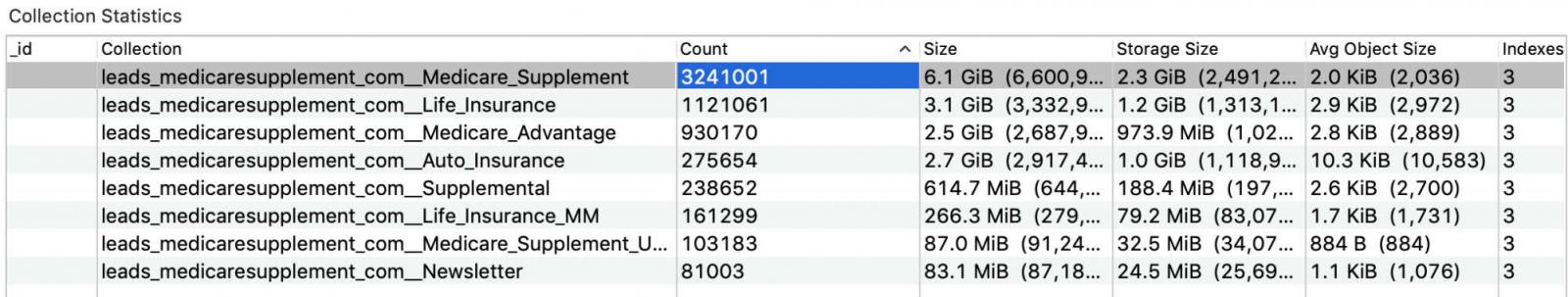
In a blog post on Thursday, the researchers note that the MongoDB instance they found seems to be part of the website's marketing leads database.
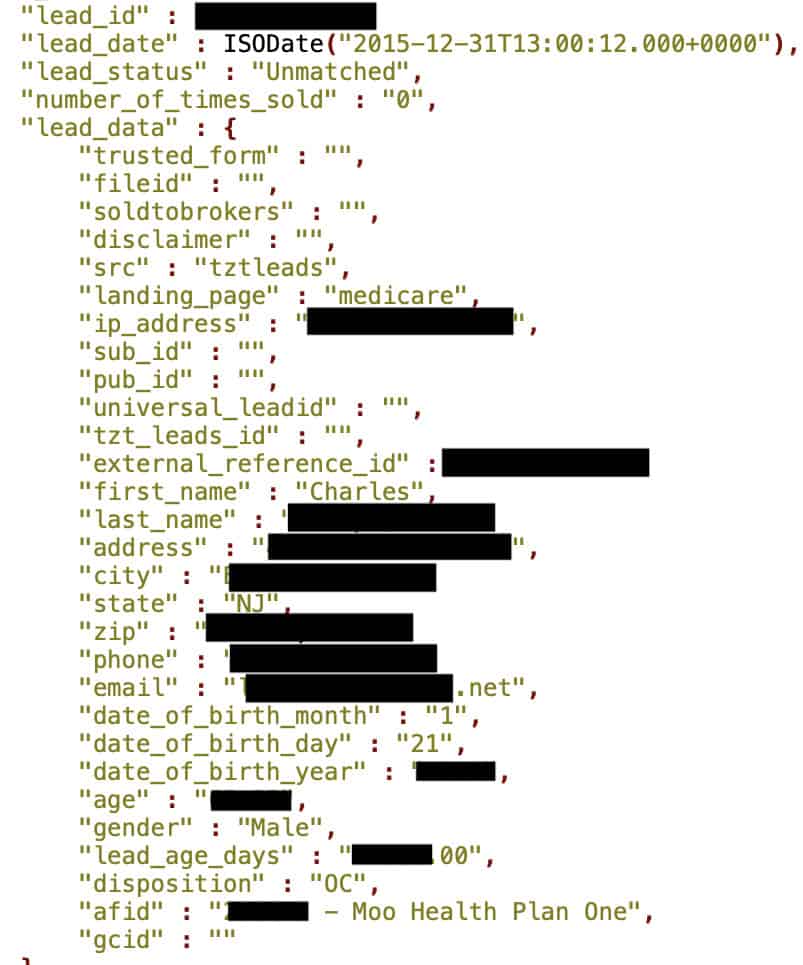
The details are sufficient to identify individuals and determine their interests as far as health insurance is concerned. These included the full names, postal addresses, email addresses, dates of birth, gender, phone numbers, and IP addresses.
"Some records—about 239,000—also indicated insurance interest area, for example, cancer insurance. Data was spread around several categories, including life, auto, medical, and supplemental insurance."
Hushed fix delivered
BinaryEdge search engine for digital assets online indexed the database on May 10. However, the information may have been available before this date and it is unclear for how long it stayed exposed or whether malicious parties accessed it.
The researchers contacted MedicareSupplement.com to alert them of the exposure, but site representatives did not reply back. They did modify the configuration of the MongoDB server to protect the database.
Diachenko warns of the potential risks arising from such incidents by saying that lack of authentication is an invitation for hackers to access the open MongoDB servers and install malware on them.
An attacker would also have full administrative privileges on the system exposed this way, allowing them to access server resources remotely "and even launch a code execution to steal or completely destroy any saved data the server contains."
Individuals affected by this data exposure incident could become targets of more carefully crafted spam messages, phishing, and fraud.
Medicare Supplement has an excellent overall rating from customers sharing on review platform Trustpilot their experience with company agents.
Break down IAM silos like Bitpanda, KnowBe4, and PathAI
Broken IAM isn't just an IT problem - the impact ripples across your whole business.
This practical guide covers why traditional IAM practices fail to keep up with modern demands, examples of what "good" IAM looks like, and a simple checklist for building a scalable strategy.









Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now