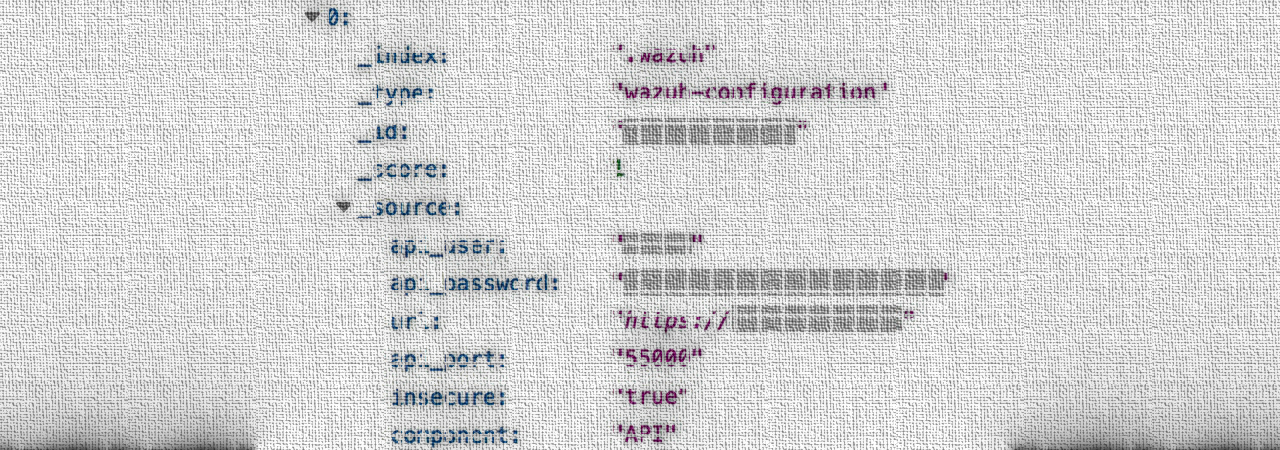
An unprotected server exposed for an unknown period security-related event logs and records of various hotel brands. The info originated from open-source intrusion detection systems (IDS) Wazuh handled by a hotel and resort management company.
Data amounting to 85.4GB was available from an Elasticsearch instance managed by Pyramid Hotel Group was publicly visible and included daily event logs events for monitoring and security alerts, system errors, policy violations, and attempted intrusions.
Internal infrastructure exposed
Not just the hotel systems were at risk, but guests, too, as details were available for devices that control hotel locking mechanisms, electronic safe boxes in the room, and various management systems for physical security.
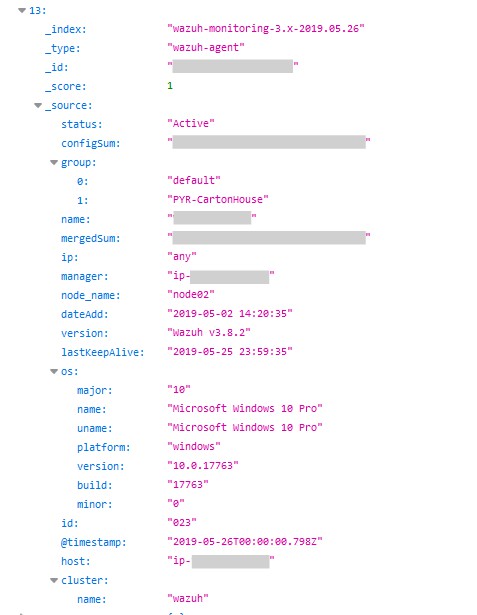
The records were extensive enough to include operating systems, security policies, internal networks, names for domains, computers, and the employees working for the affected company as well as usernames.
Researchers at vpnMentor found the database on Monday and informed Pyramid Hotel Group of the exposure. Two days later, on May 29, the company secured access to the server.
Among the hotel brands affected are Marriott property Aloft Hotels (Florida), Tarrytown House Estate (New York), Carton House Luxury Hotel (Ireland), and Temple Bar Hotel (Ireland).
Free reconnaissance info
vpnMentor compiled a list of the sensitive details exposed this way, which included server API key and password, IP addresses for incoming connections, info on open ports, restricted apps, brute-force attack detections, and alerts about local computers that ran without antivirus software.
This would be all the specifics a diligent adversary would collect in the reconnaissance stage of an attack, so access to these logs would save a lot of time and effort.
"This database gives any would-be attacker the ability to monitor the hotels’ network, gather valuable information about administrators and other users, and build an attack vector targeting the weakest links in the security chain. It also enables the attacker to see what the security team sees, learn from their attempts based on the alerts raised by the systems, and adjust their attacks accordingly" - vpnMentor
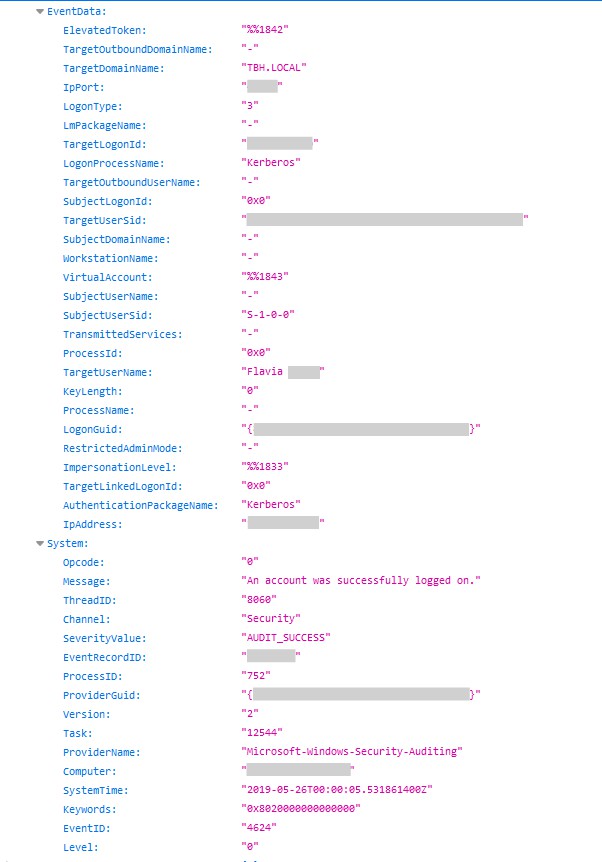
Based on the information exposed, hackers could customize their attacks to get access to the internal network of a company. The naming conventions a target uses along with the domains are valuable enough to understand how an organization set up its infrastructure and poke around for an opening.
"This data leak is disclosing information that is private, secret, and would typically be for the eyes of an internal-team or MSSP only. The irony is that what’s being exposed is from a system that is meant to protect the company from such vulnerabilities," say the researchers.
Break down IAM silos like Bitpanda, KnowBe4, and PathAI
Broken IAM isn't just an IT problem - the impact ripples across your whole business.
This practical guide covers why traditional IAM practices fail to keep up with modern demands, examples of what "good" IAM looks like, and a simple checklist for building a scalable strategy.









Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now