An unsecured database has exposed the personal information of 8 million people from the U.S. who participated in online surveys, sweepstakes, and requests for free product samples.
The way these types of sites work is you are offered free product samples, a chance to enter a sweepstake, or a prize for filling out a survey. In order to take advantage of these offers, though, you will be required to provide your personal information, which will then be used in later marketing campaigns or for lead generation.
Sanyam Jain, an independent security researcher and member of the GDI Foundation, discovered an unsecured Elasticsearch database that exposed the personal information of 8 million people who submitted entries to these types of sites.
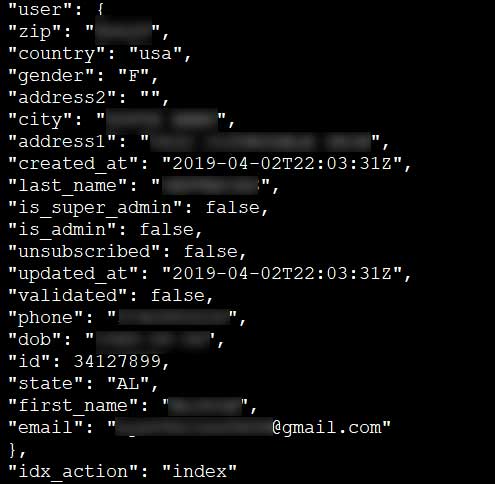
When reviewing a sample of the records provided to BleepingComputer by Jain, it was shown that the records contained personal information such as their full name, address, email address, phone number, date of birth, gender, and IP address. An example of a redacted record can be seen below.
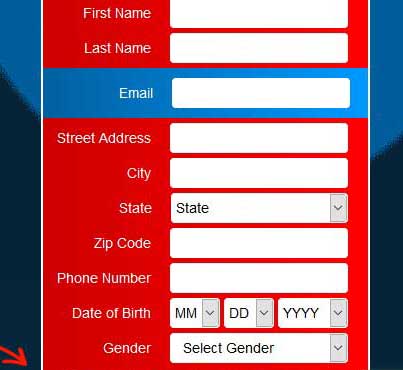
Also included in each record was the referrer, or page, where the submitted information came from. These pages were for online sweepstakes, free sample requests, and surveys as shown below.
 |
 |
When a user visits these surveys, they will ultimately be asked to submit their information.
When this information is submitted, it would be stored in the database discovered by Jain.
Finding the database owner
When an unsecured database is discovered, the first thing that most researchers do is try to determine who owns it. Unfortunately, doing so is not always easy.
In this particular case, Jain found that many of the records had a field that contained the "userenroll.com" domain in it. When visiting this page, it showed that it belonged to an online marketing company named PathEvolution.
At first it was difficult to get in touch with the owners, so Jain contacted Amazon who was hosting the database to alert them that it was unsecured and to assist in contacting the company and getting it secured.
Ultimately, I was able to track down the owner of the database by finding that PathEvolution was owned by a parent company named Ifficient, who describes themselves as a "performance based marketing" company.
In a statement to BleepingComputer, Ifficient stated that they secured the database on May 11th, 2019 after being contacted by Amazon. They further told us that even though Jain saw 130 million records in the database, the number of people affected is much smaller due to a large amount of duplicate "impression" records.
"The database alleged to have been involved in his matter contained limited information pertaining to about 8 million individuals. We received a single notification from Amazon and took necessary steps to address identified vulnerabilities, if any, within hours of being notified of the potential problem. Amazon referenced a far greater number of records exposed, but these records pertained to impression data and therefore included an extremely high number of duplicate records.
Our company takes the privacy and security of all information very seriously. The information contained within this database is not generally deemed to constitute personal information as defined by applicable state data breach notification statutes. We are committed to bolstering our security posture and to notifying potentially impacted individuals, if any, of this incident, again as required by applicable state data breach notification statutes."
In response to a follow up questions where we stated that the information exposed would be considered "personal information", we received this reply from the company.
"According to nearly all applicable state data breach notification statutes, this information does not constitute personal information. Most notably, we don't capture or store SSN, drivers license or state ID numbers, or financial account or payment card numbers. Regardless, we are currently taking steps to notify individuals for whom data sets defined by the applicable state statutes to constitute personal information was stored. We'll also be offering identity monitoring services to those individuals."
Responsible disclosure was appreciated
When researchers find exposed databases, in many cases they never receive a response or if they do, the companies are typically not appreciative. Ifficient, on the other hand, told us that they appreciate the work of independent researchers who try to secure data found on the Internet.
"We are grateful for any information pertaining to our data security, including the information shared here. We take the privacy and security of all information within our possession very seriously. Our investigation relating to this matter, and efforts to notify potentially affected individuals (if any), were undertaken immediately upon receiving the information here and are ongoing. Thank you."
Jain has told BleepingComputer that it is always nice to recognized for providing help rather receive legal threats when reporting these databases.
"I would first of all like to thank the organization for taking such quick action in securing the database. I would also like to suggest after seeing so many of these types of cases that organizations train their employees to have a good basic security hygiene so that these issues do not keep occurring.
Break down IAM silos like Bitpanda, KnowBe4, and PathAI
Broken IAM isn't just an IT problem - the impact ripples across your whole business.
This practical guide covers why traditional IAM practices fail to keep up with modern demands, examples of what "good" IAM looks like, and a simple checklist for building a scalable strategy.









Comments
berite100 - 6 years ago
couldnt you get this info from the whitepages? isnt that considered to be public info?
Lawrence Abrams - 6 years ago
No, date of birth, IP addresses, and gender are not typically found in the white pages.
berite100 - 6 years ago
thanks. yes. thats a no no.
Lawrence Abrams - 6 years ago
So, so. Really any time large amounts of personally identifiable information is grouped together in one place, it is a bad thing as it makes it easier for bad actors to amass a lot of information that can be used for a variety things.