.jpg)
Code and infrastructure from two known malware families have been observed with a new threat named Xwo, which helps operators of the MongoLock ransomware discover unprotected web services reachable over the internet.
MongoLock targets unprotected MongoDB databases, wiping them from the server and demanding a ransom to restore them.
Xwo is a Python-based bot scanner intended for reconnaissance activity. Based on IP ranges received from a command and control (C2) server, the utility probes for default passwords for services and reports back the results. In essence, it is not a malicious tool, but it enables malicious activity.
Scanner is rigorous in its survey
Research from the AT&T Cybersecurity shows that Xwo tries the default credentials for various database types (MySQL, PostgreSQL, MongoDB), Redis and Memcached in-memory data storage systems, and FTP services.
If the scanner finds Apache Tomcat on the system, it uses a module to check if it's protected with default logins and looks for misconfigurations. Additional information collected includes default paths for SVN, Git, and backup.

Xow is thorough in its exploration as it searches for the presence of the 'rsync' synchronization utility and for data from direct connections via RealVNC; these details may tell the attacker where to look for databases.
The instructions with the IP address ranges to scan come from several command and control (C2) servers that are associated with MongoLock:
s.propub3r6espa33w[.]tk
s.blockchainbdgpzk[.]tk
s.pcrisk[.]xyz
s.rapid7[.]xyz
"The above C2 infrastructure is associated with MongoLock," writes security researcher Tom Hegel, adding that whoever is behind the infrastructure registers domain names that mimic security and news organizations or websites (Rapid7, PCRisk, ProPublica).
These C2 servers used content delivery network services from Cloudflare. Following notification from AT&T Cybersecurity, the domains have been taken offline.
Despite not being malicious in nature, Xow does not move undetected. At the moment, 37 antivirus engines in VirusTotal scannning service flag it as a threat.
A dash of Xbash
Xwo scanner is not built on 100% original code. Some of it is identical with parts of Xbash, a malware with ransomware and cryptojacking capabilities that targets Linux and Microsoft servers.
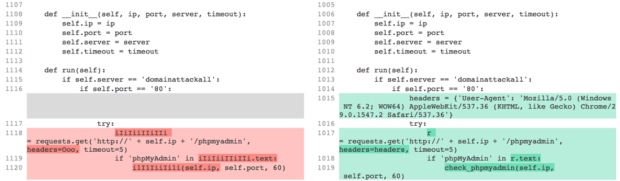
Created by the cybercrime group called Iron, Xbash is similar to MongoLock, as it looks for unprotected databases (MySQL, PostgreSQL, and MongoDB) and deletes them; what's left behind is a ransom note that should not be paid because the data cannot be restored.
Xbash is the creation of a cybercrime group called Iron, but a connection with Xow is not evident at this point, says Hegel, but they do not dismiss a potential link. It could also be a matter of repurposing public code.
Break down IAM silos like Bitpanda, KnowBe4, and PathAI
Broken IAM isn't just an IT problem - the impact ripples across your whole business.
This practical guide covers why traditional IAM practices fail to keep up with modern demands, examples of what "good" IAM looks like, and a simple checklist for building a scalable strategy.









Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now