-
New Fallout Exploit Kit Drops GandCrab Ransomware or Redirects to PUPs
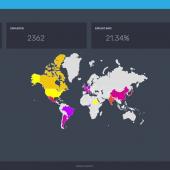
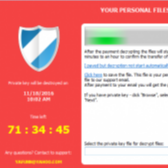
A new exploit kit called Fallout is being used to distribute the GandCrab ransomware, malware downloading Trojans, and other potentially unwanted programs (PUPs).
- September 06, 2018
- 06:24 PM
 0
0
-
Windows Task Scheduler Zero Day Exploited by Malware
Malware developers have started to use the zero-day exploit for Windows Task Scheduler component, two days after proof-of-concept code for the vulnerability appeared online.
- September 05, 2018
- 11:45 AM
 4
4
-
New Webinar: Choose Your Own Investigation — Browser Attack Edition

Modern attacks have shifted focus to the browser, yet detection tools remain largely blind to the crucial activity happening there.
Join Push Security on February 11th for an interactive "choose-your-own-adventure" webinar on ClickFix, credential phishing, and other in-browser attacks we've observed in the wild.
-
Exploit Published for Unpatched Flaw in Windows Task Scheduler
A security researcher has published on Twitter details about a vulnerability in the Windows OS. The vulnerability is a "local privilege escalation" issue that allows an attacker to elevate the access of malicious code from a limited USER role to an all-access SYSTEM account.
- August 28, 2018
- 04:57 AM
 2
2
-
Hackers Exploiting DLink Routers to Redirect Users to Fake Brazilian Banks
Attackers are targeting DLink DSL modem routers in Brazil and exploiting them to change the DNS settings to a DNS server under the attacker's control. This then allows them to redirect users attempting to connect to their online banks to fake banking websites that steal the user's account information.
- August 11, 2018
- 01:27 PM
 1
1
-
GandCrab Ransomware Author Bitter After Security Vendor Releases Vaccine App
The author of the GandCrab ransomware is a little bit bitter at South Korean security vendor AhnLab after the security firm released a vaccine for the GandCrab ransomware.
- August 03, 2018
- 10:24 AM
 1
1
-
Exploitation of Drupalgeddon2 Flaw Starts After Publication of PoC Code
The exploitation of a very dangerous Drupal vulnerability has started after the publication of proof-of-concept (PoC) code.
- April 13, 2018
- 05:43 AM
 0
0
-
NSA Exploits Ported to Work on All Windows Versions Released Since Windows 2000
A security researcher has ported three leaked NSA exploits to work on all Windows versions released in the past 18 years, starting with Windows 2000.
- February 05, 2018
- 07:10 AM
 0
0
-
PoCs for Two Magento Bugs Released
Security researchers from DefenseCode have released on Wednesday proof-of-concept code for two Magento vulnerabilities patched last month.
- October 06, 2017
- 03:35 AM
 0
0
-
Proof-of-Concept Exploit Code Published for Remote iPhone 7 WiFi Hack
A Google security researcher has published proof-of-concept code for a vulnerability that can be exploited remotely via a WiFi connection to take over iPhone 7 handsets.
- September 26, 2017
- 08:25 AM
 0
0
-
Exploit Broker Zerodium Offers $1 Million for Tor Browser Zero-Days
Zerodium, a company that buys exploits to sell to government agencies, is offering up to $1 million for zero-days affecting the Tor Browser.
- September 13, 2017
- 12:38 PM
 0
0
-
Second Researcher Drops Router Exploit Code After D-Link Mishandles Bug Reports
Embedi, a hardware security firm, has published details about two vulnerabilities that have yet to be patched in the firmware of D-Link routers. This marks the second incident of this sort in the last five days.
- September 13, 2017
- 06:20 AM
 1
1
-
Researcher Releases Fully Working Exploit Code for iOS Kernel Vulnerability
Adam Donenfeld, a researcher with mobile security firm Zimperium, has published today proof-of-concept code for zIVA — a kernel exploit that affects iOS 10.3.1 and previous versions.
- August 24, 2017
- 02:15 PM
 0
0
-
90% of Companies Get Attacked with Three-Year-Old Vulnerabilities
A Fortinet report released this week highlights the importance of keeping secure systems up to date, or at least a few cycles off the main release, albeit this is not recommended, but better than leaving systems unpatched for years.
- August 24, 2017
- 05:35 AM
 0
0
-
ROPEMAKER Lets Attackers Change Your Emails After Delivery
A new email attack scenario nicknamed ROPEMAKER allows a threat actor to change the content of emails received by targets via remote CSS files.
- August 23, 2017
- 02:25 AM
 2
2
-
New Disdain Exploit Kit Sold on Underground Hacking Forums
A malware developer using the pseudonym of Cehceny is currently advertising a new exploit kit on underground hacking forums.
- August 14, 2017
- 05:56 PM
 0
0
-
Exploit Derived From ETERNALSYNERGY Upgraded to Target Newer Windows Versions
Thai security researcher Worawit Wang has put together an exploit based on ETERNALSYNERGY that can also target newer versions of the Windows operating system.
- July 17, 2017
- 11:55 AM
 0
0
-
751 Domains Hijacked to Redirect Traffic to Exploit Kits
On July 7, French domain registrar Gandi lost control over 751 customer domains, which had their DNS records altered to point incoming traffic to websites hosting exploits kits.
- July 17, 2017
- 08:55 AM
 1
1
-
Security Researchers Are Gathering Funds to Buy Future Shadow Brokers Exploits
A group of security researchers have set up a Patreon page to raise funds necessary to buy their way into the first batch of monthly exploit the Shadow Brokers promised on Tuesday.
- May 31, 2017
- 02:00 PM
 0
0
-
2016's Most Popular Exploit Was the Vulnerability Used for the Stuxnet Attacks
One of the vulnerabilities used to spread the Stuxnet virus was 2016's most popular exploit, according to telemetry data gathered by Russia cyber-security firm Kaspersky Labs.
- April 24, 2017
- 08:45 AM
 0
0
-
CryptoLuck Ransomware being Malvertised via RIG-E Exploit Kits
A new ransomware called CryptoLuck has been discovered being distributed via the RIG-E exploit kit. This ransom also utilizes an interesting method of infecting a victim through the legitimate GoogleUpdate.exe executable and DLL hijacking.
- November 15, 2016
- 03:46 PM
 0
0