-
Malicious npm package steals WhatsApp accounts and messages
A malicious package in the Node Package Manager (NPM) registry poses as a legitimate WhatsApp Web API library to steal WhatsApp messages, collect contacts, and gain access to the account.
- December 22, 2025
- 11:08 AM
 0
0
-
WhatsApp API flaw let researchers scrape 3.5 billion accounts
Researchers compiled a list of 3.5 billion WhatsApp mobile phone numbers and associated personal information by abusing a contact-discovery API that lacked rate limiting.
- November 22, 2025
- 01:53 PM
 2
2
-
New Webinar: Choose Your Own Investigation — Browser Attack Edition

Modern attacks have shifted focus to the browser, yet detection tools remain largely blind to the crucial activity happening there.
Join Push Security on February 11th for an interactive "choose-your-own-adventure" webinar on ClickFix, credential phishing, and other in-browser attacks we've observed in the wild.
-
Microsoft Entra ID flaw allowed hijacking any company's tenant
A critical combination of legacy components could have allowed complete access to the Microsoft Entra ID tenant of every company in the world.
- September 21, 2025
- 01:30 PM
 4
4
-
Hackers hide behind Tor in exposed Docker API breaches
A threat actor targeting exposed Docker APIs has updated its malicious tooling with more dangerous functionality that could lay the foundation for a complex botnet.
- September 09, 2025
- 03:16 PM
 0
0
-
Max severity Argo CD API flaw leaks repository credentials
An Argo CD vulnerability allows API tokens with even low project-level get permissions to access API endpoints and retrieve all repository credentials associated with the project.
- September 05, 2025
- 11:30 AM
 0
0
-
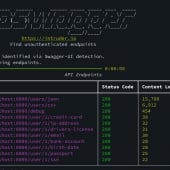
Free Autoswagger Tool Finds the API Flaws Attackers Hope You Miss
Exposed API documentation is a gift-wrapped roadmap for threat actors. The free Autoswagger tool from Intruder scans for exposed docs and flags endpoints with broken access controls—before attackers find them.
- July 28, 2025
- 10:01 AM
 0
0
-
New 'Defendnot' tool tricks Windows into disabling Microsoft Defender
A new tool called 'Defendnot' can disable Microsoft Defender on Windows devices by registering a fake antivirus product, even when no real AV is installed.
- May 17, 2025
- 10:09 AM
 7
7
-
Phishing kits now vet victims in real-time before stealing credentials
Phishing actors are employing a new evasion tactic called 'Precision-Validated Phishing' that only shows fake login forms when a user enters an email address that the threat actors specifically targeted.
- April 09, 2025
- 09:49 AM
 0
0
-
Verizon Call Filter API flaw exposed customers' incoming call history
A vulnerability in Verizon's Call Filter feature allowed customers to access the incoming call logs for another Verizon Wireless number through an unsecured API request.
- April 02, 2025
- 03:47 PM
 0
0
-
Cloudflare now blocks all unencrypted traffic to its API endpoints
Cloudflare announced that it closed all HTTP connections and it is now accepting only secure, HTTPS connections for api.cloudflare.com.
- March 22, 2025
- 11:35 AM
 5
5
-
Microsoft to remove the Location History feature in Windows
Microsoft announced the deprecation of the Location History feature from Windows, which let applications like the Cortana virtual assistant to fetch location history of the device.
- February 17, 2025
- 01:50 PM
 3
3
-
Google fixes flaw that could unmask YouTube users' email addresses
Google has fixed two vulnerabilities that, when chained together, could expose the email addresses of YouTube accounts, causing a massive privacy breach for those using the site anonymously.
- February 12, 2025
- 06:00 AM
 0
0
-
DocuSign's Envelopes API abused to send realistic fake invoices
Threat actors are abusing DocuSign's Envelopes API to create and mass-distribute fake invoices that appear genuine, impersonating well-known brands like Norton and PayPal.
- November 04, 2024
- 03:18 PM
 0
0
-
Microsoft overhauls security for publishing Edge extensions
Microsoft has introduced an updated version of the "Publish API for Edge extension developers" that increases the security for developer accounts and the updating of browser extensions.
- September 30, 2024
- 05:49 PM
 1
1
-
New Google Chrome feature will translate complex pages in real time
Google is testing a new API that uses machine learning models to offer real-time language translation for inputted text and to make it easier to translate web pages.
- September 22, 2024
- 10:19 AM
 4
4
-
Over 400,000 Life360 user phone numbers leaked via unsecured API
A threat actor has leaked a database containing the personal information of 442,519 Life360 customers collected by abusing a flaw in the login API.
- July 17, 2024
- 12:32 PM
 0
0
-
Email addresses of 15 million Trello users leaked on hacking forum
A threat actor has released over 15 million email addresses associated with Trello accounts that were collected using an unsecured API in January.
- July 16, 2024
- 01:57 PM
 0
0
-
Hackers abused API to verify millions of Authy MFA phone numbers
Twilio has confirmed that an unsecured API endpoint allowed threat actors to verify the phone numbers of millions of Authy multi-factor authentication users, potentially making them vulnerable to SMS phishing and SIM swapping attacks.
- July 03, 2024
- 12:43 PM
 10
10
-
Club Penguin fans breached Disney Confluence server, stole 2.5GB of data
Club Penguin fans hacked a Disney Confluence server to steal information about their favorite game but wound up walking away with 2.5 GB of internal corporate data, BleepingComputer has learned.
- June 05, 2024
- 04:15 PM
 1
1
-
Cox fixed an API auth bypass exposing millions of modems to attacks
Cox Communications has fixed an authorization bypass vulnerability that enabled remote attackers to abuse exposed backend APIs to reset millions of modems' settings and steal customers' sensitive personal information.
- June 03, 2024
- 05:10 PM
 0
0