-
Fake BianLian ransom notes mailed to US CEOs in postal mail scam
Scammers are impersonating the BianLian ransomware gang in fake ransom notes sent to US companies via snail mail through the United States Postal Service.
- March 04, 2025
- 09:18 PM
 0
0
-
Cloudflare mitigated a record-breaking 5.6 Tbps DDoS attack
The largest distributed denial-of-service (DDoS) attack to date peaked at 5.6 terabits per second and came from a Mirai-based botnet with 13,000 compromised devices.
- January 21, 2025
- 04:04 PM
 2
2
-
New Webinar: Choose Your Own Investigation — Browser Attack Edition

Modern attacks have shifted focus to the browser, yet detection tools remain largely blind to the crucial activity happening there.
Join Push Security on February 11th for an interactive "choose-your-own-adventure" webinar on ClickFix, credential phishing, and other in-browser attacks we've observed in the wild.
-
Dark Angels ransomware receives record-breaking $75 million ransom
A Fortune 50 company paid a record-breaking $75 million ransom payment to the Dark Angels ransomware gang, according to a report by Zscaler ThreatLabz.
- July 30, 2024
- 04:22 PM
 3
3
-
Panera Bread likely paid a ransom in March ransomware attack
Panera Bread, an American chain of fast food restaurants, most likely paid a ransom after being hit by a ransomware attack, suggests language used an internal email sent to employees.
- June 17, 2024
- 03:55 PM
 3
3
-
Ransomware payments reached record $1.1 billion in 2023
Ransomware payments in 2023 soared above $1.1 billion for the first time, shattering previous records and reversing the decline seen in 2022, marking the year as an exceptionally profitable period for ransomware gangs.
- February 07, 2024
- 09:00 AM
 1
1
-
An Overview of the Global Impact of Ransomware Attacks
With ransomware attacks disrupting businesses and governments worldwide, we take a look at the latest finding in a recent ransomware report.
- February 21, 2023
- 10:04 AM
 0
0
-
New 0mega ransomware targets businesses in double-extortion attacks
A new ransomware operation named '0mega' targets organizations worldwide in double-extortion attacks and demands millions of dollars in ransoms.
- July 08, 2022
- 03:22 PM
 0
0
-
Ransomware gang wanted $40 million in Florida schools cyberattack
Fueled by large payments from victims, ransomware gangs have started to demand ridiculous ransoms from organizations that can not afford them. An example of this is a recently revealed ransomware attack on the Broward County Public Schools district where threat actors demanded a $40,000,000 payment.
- April 02, 2021
- 07:03 AM
 2
2
-
La Porte County Pays $130,000 Ransom To Ryuk Ransomware
Another public administration in the U.S. surrenders cybercriminal demands as La Porte County, Indiana, pays $130,000 to recover data on computer systems impacted by ransomware.
- July 14, 2019
- 02:05 PM
 5
5
-
Over 12,000 MongoDB Databases Deleted by Unistellar Attackers
Over 12,000 unsecured MongoDB databases have been deleted over the last three weeks, with only a message left behind asking the owners of the databases to contact the cyber-extortionists to have the data restored.
- May 17, 2019
- 08:37 AM
 1
1
-
New Scam Holds YouTube Channels for Ransom
Scammers are abusing the YouTube policy violation system by filing fake copyright infringements against content creators until their channel is close to being suspended. These scammers then hold the channel ransom by telling YouTubers to send a payment or they will file another copyright infringement to have the channel suspended.
- February 02, 2019
- 10:00 AM
 0
0
-
Hacker Say They Compromised ProtonMail. ProtonMail Says It's BS.
A person or group claiming to have hacked ProtonMail and stolen "significant" amounts of data has posted a lengthy ransom demand with some wild claims to an anonymous Pastebin. ProtonMail states it's complete BS.
- November 16, 2018
- 09:23 AM
 0
0
-
Mongo Lock Attack Ransoming Deleted MongoDB Databases
An attack called Mongo Lock is targeting remotely accessible and unprotected MongoDB databases, wiping them, and then demanding a ransom in order to get the contents back.
- September 11, 2018
- 11:08 AM
 0
0
-
Shipping Firm Avoids Customer Data Dump in Last Year's Hack & Ransom Incident
UK-based shipping company Clarkson PLC (or Clarksons) has revealed more details about a security breach that took place last year, and during which hackers threatened to release some of the company's data online if it didn't pay a ransom demand.
- July 31, 2018
- 11:55 AM
 0
0
-
Europol Dismantles One of the Internet's Oldest Hacker Groups
Europol, French, UK, and Thai police arrested eight people they suspect to have been involved or to have been part of a notorious hacker group known as Rex Mundi (Latin for "King of the World").
- June 15, 2018
- 06:56 PM
 2
2
-
DDoSer Who Terrorized German and UK Firms Gets Off Without Jail Time
A German hacker who launched DDoS attacks and tried to extort ransom payments from German and UK firms was sentenced last month to one year and ten months of probation.
- May 07, 2018
- 01:30 AM
 0
0
-
Power Company in India Hacked and Billing Data Ransomed for 10 Million Rupees
Last week hackers gained access to the computer systems of the Uttar Haryana Bijli Vitran Nigam (UHBVN) power company in India and stole the billing data of their customers. In order to get the data back, the attackers are demanding 1 RS Core, or 10 million Rupess, for the stolen data. This is equivalent to approximately $150,000 USD
- March 29, 2018
- 02:39 PM
 1
1
-
Marriage Agency Executive Sentenced for DDoS Extortion Scheme
Ukrainian authorities have sentenced two individuals —a man and a woman— to five years suspended sentences for launching DDoS attacks and running a DDoS extortion scheme.
- March 07, 2018
- 01:13 PM
 0
0
-
Some Memcached DDoS Attackers Are Asking for a Ransom Demand in Monero
DDoS extortionists have already pounced on the Memcached DDoS attack vector in attempts to extract payments from attacked companies.
- March 02, 2018
- 07:34 PM
 0
0
-
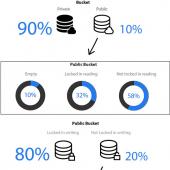
2% of Amazon S3 Public Buckets Aren't Write-Protected, Exposed to Ransom Attacks
New research published on Monday reveals that 5.8% of all Amazon S3 buckets are publicly readable, while 2% are publicly writeable —with the latter allowing anyone to add, edit, or delete data, and even hold a victim's data for ransom.
- February 28, 2018
- 06:06 AM
 0
0