
This week, the National Cyber Security Alliance (NCSA) reminds us that, “our day-to-day life depends on the country’s 16 sectors of critical infrastructure, which supply food, water, financial services, public health, communications and power along with other networks and systems. A disruption to this system, which is operated via the internet, can have significant and even catastrophic consequences for our nation.”
October is National Cyber Security Week and week 4 (this week), the emphasis is on the importance of securing critical infrastructure.
Currently, there are sixteen critical infrastructure sectors. The existing critical infrastructure sectors are:
- Chemical
- Commercial Facilities
- Communications
- Critical Manufacturing
- Dams
- Defense Industrial Base
- Emergency Services
- Energy
- Financial Services
- Food and Agriculture
- Government Facilities
- Healthcare and Public Health
- Information Technology
- Nuclear Reactors, Material, and Waste
- Transportation Systems
- Water and Wastewater Systems
US critical infrastructure continues to be vulnerable to attacks and has already been compromised as cybercriminals work to gain a foothold in the US.
Additionally, cybercriminals have been targeting the commercial sector with as much aggression and skill as their attacks against the government. Unfortunately, some attacks against corporations have national security ramifications, a fact not yet fully realized by all businesses.
The Atlantic Council reports:
“As just a few examples: ransomware payoffs fund terrorists and nation states seeking to evade sanctions; compromised computers act as relays to disguise attacks on critical infrastructure and steal secrets; stolen intellectual property accelerates the build-out of competitive enterprises weakening our economy and influence.
We live in an interconnected world full of cyber threats and vulnerabilities. Our national security depends on the resilience of implementing effective security controls across all sectors of our critical infrastructure. Our strength in addressing these evolving threats will require a much more collaborative effort with far more active engagement by the private sector in matters of systemic risk and national security. Collectively, we have the people, processes, and technology needed to combat this threat and remain safe.”
The 2018 Verizon Data Breach Investigations Report (DBIR) documented and analyzed 649 breaches in utilities, transportation, healthcare, and other verticals that use operational technology (OT) systems--typically used in critical infrastructure. In total, that represents 29.2% of reported breaches (not incidents) in industries who are components of the critical infrastructure. It should be noted that this doesn't even include financial services.
The most reported critical infrastructure vulnerabilities deal with the power grid. Also widely reported for vulnerabilities is electronic voting technology. And, hospitals continue to be a favorite target among cybercriminals.
To make matters worse, supply chain vulnerabilities are on the increase. This includes the use of "meaconing" at ports by sending fake GPS signals in order to route a ship incorrectly, which results in wreaking havoc on commerce. Also, ransomware can debilitate the software that aids the loading and unloading of ships and trucks, in addition to corrupting container loading stowage software which causes ships to become unbalanced.
ESET researchers recently exposed shadowy cyber-espionage group, GreyEnergy, the successor to the BlackEnergy APT group that terrorized the Ukraine and then went underground. It is also affiliated with TeleBots, which was responsible for NotPetya, believed by many to be the most damaging cyberattack ever experienced.
According to ESET, GreyEnergy’s malware toolkit "both mirrors and improves on already-sophisticated techniques used in the devastating NotPetya attacks and Ukraine power grid outages."
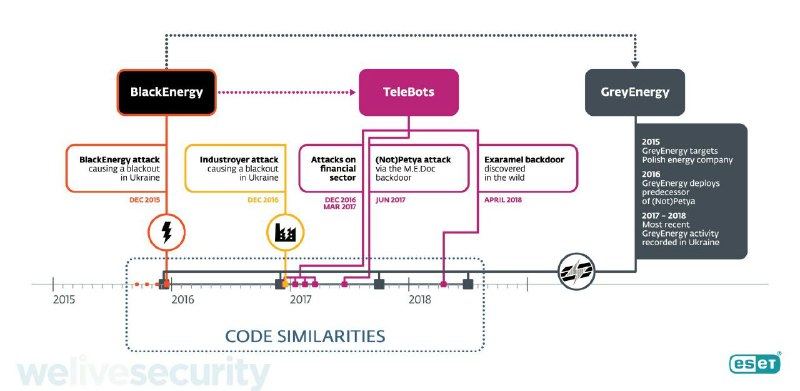
ESET also reports:
"...compared to BlackEnergy, GreyEnergy is a more modern toolkit with an even greater focus on stealth. ESET researchers have demonstrated that GreyEnergy has the capacity to take full control of entire company networks.
One basic stealth technique is to push only selected modules to selected targets, and only when needed. In addition, some GreyEnergy modules are partially encrypted and some remain fileless – running only in memory – with the intention of hindering analysis and detection.
To cover their tracks, typically, GreyEnergy’s operators securely wipe the malware components from the victims’ hard drives.
The modules described in ESET’s analysis were used for espionage and reconnaissance purposes and include: backdoor, file extraction, taking screenshots, keylogging, password and credential stealing."
Earlier this month, the Federal Emergency Management Agency (FEMA) performed the first successful test of the “Presidential Alert,” a text message sent simultaneously to cell phones nationwide.
The infrastructure to send presidential messages to smartphones has been around since 2012. In 2013, the security research firm IOActive published a report, which maintained that a hacker could log into the Emergency Alert System (EAS) server and either disrupt an emergency alert or send out a false one. It has also been suggested that a hacker with only “a moderate skill level” could hack the EAS and gain access to a considerable amount of information on the server.
The Presidential Alert System could also fall victim to Man-in-the-Middle attacks. Dr. Kenneth Williams, Executive Director of the Center for Cyber Defense and Program Director for the cybersecurity program at American Military University, agrees that the EAS system is vulnerable to attack. “Like any modern system, the EAS system is managed by software, making it susceptible to a number of known attacks including a man-in-the-middle attack,” he explained.
Spearheading the national effort to defend critical infrastructure is the Department of Homeland Security (DHS). The DHS provides strategic guidance to public and private partners, promotes a national unity of effort, and coordinates the overall federal effort to promote the security and resilience of the nation's critical infrastructure. Following this week of the NCSA’s focus on critical infrastructure, we head into November which is Critical Infrastructure Security and Resilience Month.
Break down IAM silos like Bitpanda, KnowBe4, and PathAI
Broken IAM isn't just an IT problem - the impact ripples across your whole business.
This practical guide covers why traditional IAM practices fail to keep up with modern demands, examples of what "good" IAM looks like, and a simple checklist for building a scalable strategy.









Comments
xrobwx - 7 years ago
Ours got attacked by Hurricane Michael.
Candice_Lanier - 7 years ago
Yes, devastating. Hope you didn't get hit too hard by it.
Bullwinkle-J-Moose - 7 years ago
"October is National Cyber Security Week and week 4 (this week), the emphasis is on the importance of securing critical infrastructure."
------------------------------------------------------------------------
Gee Whillakers
How many weeks are there in National Cyber Security Week Batman?