
Cloudflare announced that it closed all HTTP connections and it is now accepting only secure, HTTPS connections for api.cloudflare.com.
The move prevents unencrypted API requests from being sent, even accidentally, to eliminate the risk of sensitive information being exposed in cleartext traffic before the server closes the HTTP conection and redirects to a secure communication channel.
“Starting today, any unencrypted connection to api.cloudflare.com will be completely rejected,” reads Cloudflare’s announcement on Thursday.
“Developers should not expect a 403 Forbidden response any longer for HTTP connections, as we will prevent the underlying connection to be established by closing the HTTP interface entirely. Only secure HTTPS connections will be allowed to be established” - the internet services company added.
The Cloudflare API helps developers and system administrators to automate and manage Cloudflare services. It is used for DNS records management, firewall configuration, DDoS protection, caching, SSL settings, infrastructure deployment, accessing analytics data, and managing zero-trust access and security policies.
Previously, Cloudflare systems allowed API access over both HTTP (unencrypted) and HTTPS (encrypted), either by redirecting or rejecting HTTP.
However, as the company explains, even rejected HTTP requests may leak sensitive data like API keys or tokens before the server responds.
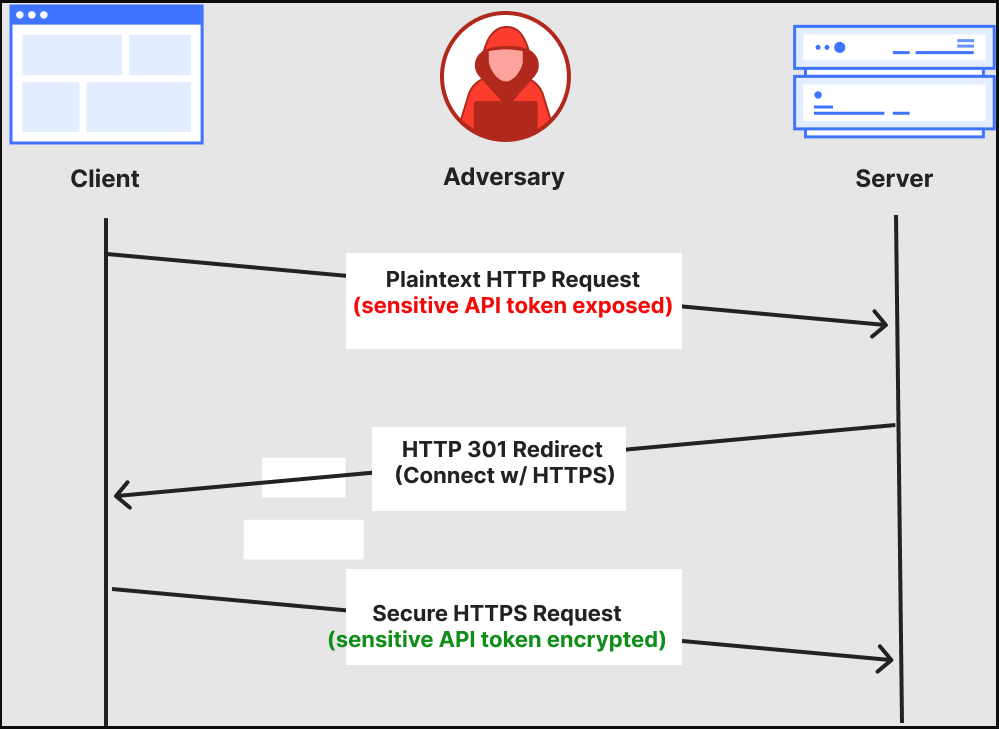
Source: Cloudflare
Such a sceario is more dangerous when the connection is over public or shared Wi-Fi networks where adversary-in-the-middle attacks are easier to pull off.
By disabling HTTP ports entirely for API access, Cloudflare blocks plaintext connections at the transport layer before any data is exchanged, enforcing HTTPS from the start.
Impact and next steps
The change immediately affects anyone using HTTP on the Cloudflare API service. Scripts, bots, and tools relying on the protocol will break.
The same applies to legacy systems and automated clients, IoT devices, and low-level clients that don’t support or don’t default to HTTPS due to improper configuration.
For customers with websites on Cloudflare, the company prepares to release a free option towards the end of the year that will disable HTTP traffic in a safe way.
Cloudflare data indicates that a small but significant percentage of roughly 2.4% of all internet passing through its systems is still done over the insecure HTTP protocol. When automated traffic is taken into account, the HTTP share jumps to nearly 17%.
Customers can track HTTP vs HTTPS traffic on their dashboard under Analytics & Logs > Traffic Served Over SSL before opting in, to estimate the impact it will have on their environment.
Break down IAM silos like Bitpanda, KnowBe4, and PathAI
Broken IAM isn't just an IT problem - the impact ripples across your whole business.
This practical guide covers why traditional IAM practices fail to keep up with modern demands, examples of what "good" IAM looks like, and a simple checklist for building a scalable strategy.









Comments
AnonyMik - 9 months ago
About time.. would be actually nice if they sorted their DNS resolvers.. Cloudflare has a shocking reputation for actually allowing the vast majority of query flood and dns amplification attacks.
Zutyro - 9 months ago
It's crazy that it was still possible until now.
deltasierra - 9 months ago
About time.
adversaryitm - 9 months ago
What is an "adversary-in-the-middle" attack and how does it differ from a MITM? Or are we just being respectful of a cyber-criminal's pronouns now?
deltasierra - 9 months ago
Yep, just political correctness. That and it could be attackers (plural), not a single attacker ("man") whereas "adversary" is vague enough to support both single attackers and a group.
Some security companies and orgs have already been doing this for years now;.