
New research released this week reveals that a large chunk of today Android VPN clients are a serious security and privacy risk, with some clients failing to encrypt traffic, and some even injecting ads in a customer's browsing experience.
The study analyzed 283 VPN apps from over 1.4 million Android apps hosted on the Google Play Store.
Researchers focused their efforts on those apps that requested access to BIND_VPN_SERVICE, the Android permission that grants apps access to a series of built-in Android VPN-specific functions.
After analyzing the internal structure of these apps and their behavior, researchers found a series of troubling issues that led them to conclude that a significant chunk of the Android VPN apps ecosystem doesn't protect its users enough.
Below is a summary of all the study's findings:
- 38% of analyzed VPN clients contain some malware presence according to VirusTotal.
- 75% of them use third-party tracking libraries.
- 82% request permissions to access sensitive resources including user accounts and text messages.
- 18% of the apps do not mention the entity hosting the terminating VPN server.
- 16% of the analyzed apps may forward traffic through other participating users rather than use servers hosted in the cloud.
- 4% of the analyzed VPN apps use the VPN permission to implement localhost proxies to intercept and inspect user traffic locally (primarily for antivirus and traffic filtering purposes).
- 18% of VPN apps don't encrypt traffic.
- 84% don't tunnel IPv6 traffic.
- 66% don't tunnel DNS traffic, exposing a user's browsing habits, mainly due to misconfigurations or developer-induced errors.
- 16% of VPN apps deploy non-transparent proxies that modify user’s HTTP traffic by injecting and removing headers or performing techniques such as image transcoding.
- 2 VPN apps actively injected JavaScript code in user’s traffic for advertisement and tracking purpose.
- 1 VPN app redirected e-commerce traffic to an external advertising partner.
- 4 VPN clients compromised the device's root-store by adding their own root certificates so they could intercept TLS encrypted traffic.
- 3 VPN apps claimed to provide traffic acceleration services, but they selectively intercepted traffic to specific online services like social networks, banking, e-commerce sites, email and IM services.
Below is a table of the biggest offenders, according to the research crew, and a table of the worst offenders, based on user reviews.
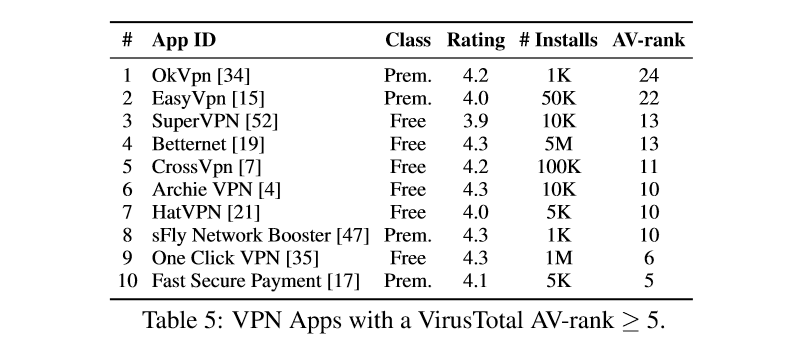
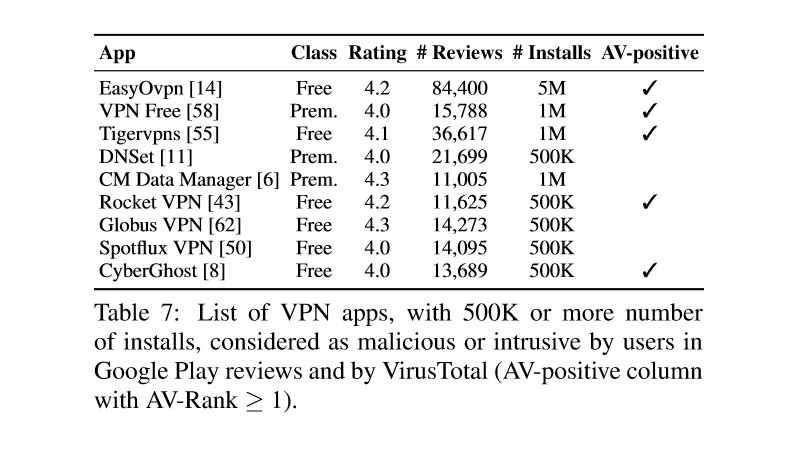
"Despite the fact that Android VPN-enabled apps are being installed by millions of mobile users worldwide, their operational transparency and their possible impact on user’s privacy and security remains 'terra incognita' even for tech-savvy users," the research team concludes.
"The ability of the BIND_VPN_SERVICE permission to break Android's sandboxing and the naive perception that most users have about third-party VPN apps suggest that it is urging to re-consider Android’s VPN permission model to increase the control over VPN clients," the researchers added.
Their full research, titled "An Analysis of the Privacy and Security Risks of Android VPN Permission-enabled Apps" is available for download from here.
Break down IAM silos like Bitpanda, KnowBe4, and PathAI
Broken IAM isn't just an IT problem - the impact ripples across your whole business.
This practical guide covers why traditional IAM practices fail to keep up with modern demands, examples of what "good" IAM looks like, and a simple checklist for building a scalable strategy.









Comments
mat9v - 8 years ago
Is there any VPN app that does not try to track/infiltrate/sell your traffic to third parties?
The article does not mention any - is this for "not advertising" purpose or that there is no app that is free from spying and does the job it should?
Jonas_Wright - 8 years ago
Well, I can only recommend app that it is coming from trusted VPN service provider. Question can again be how you can be sure it is all right and that's where you should do a little research about providers. For instance, I have trust only in VPN providers which doesn't use third party service and Google analytic stuff. One of them is Traceless VPN and I would always encourage to look for those kind of providers, which, believe me, is not the easiest thing these days.
campuscodi - 8 years ago
The research only highlighted the infringing apps. It was not its purpose to recommend a specific app.
airvpn_nl - 8 years ago
Although it's a good thing that this information is shared, it would be even better to mention trusted VPN services. Now people might not know what to do. There are a lot of decent and informative VPN comparison sites that might help out those people. AirVPN (http://www.airvpn.nl/content/try-airvpn) is based on OpenVPN and operated by activists and hacktivists in defence of net neutrality, privacy and against censorship. Do your own research on the internet and you will see that's the truth. #privacymatters
Cuckoothom - 8 years ago
That is not the case with the established VPN brands. However, most companies keep logs of their customers but the main thing of concern is where that data is being used. For e.g. PureVPN does not keep logs to be sold later but rather for the internal working of the organization and to make customer experience better.
DodoIso - 8 years ago
Google paid $8000 for some of the vulnerabilities in Chrome. They should pay the article researchers $8000 per infringing app. After all, the researchers did the job Google were supposed to do.