
A new version of the Banshee info-stealing malware for macOS has been evading detection over the past two months by adopting string encryption from Apple's XProtect.
Banshee is an information stealer focused on macOS systems. It emerged in mid-2024 as a stealer-as-a-service available to cybercriminals for $3,000.
Its source code was leaked on the XSS forums in November 2024, leading to the project shutting down for the public and creating an opportunity for other malware developers to improve on it.
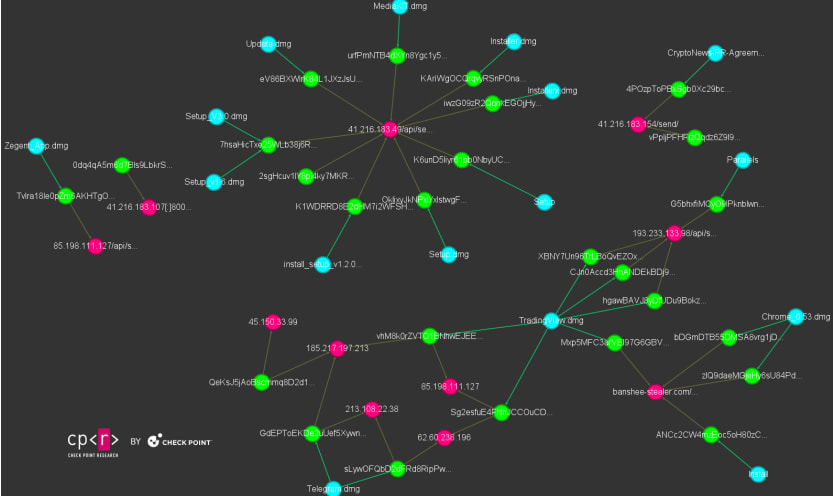
According to Check Point Research, which discovered one of the new variants, the encryption method present in Banshee allows it to blend in with normal operations and to appear legitimate while collecting sensitive information from infected hosts.
Another change is that it no longer avoid systems belonging to Russian users.
Source: Check Point
XProtect encryption
Apple's XProtect is the malware detection technology built into macOS. It uses a set of rules, similar to antivirus signatures, to identify and block known malware.
The latest version of Banshee Stealer adopted a string encryption algorithm that XProtect itself uses to protect its data.
By scrambling its strings and only decrypting them during execution, Banshee can evade standard static detection methods.
It is also possible that macOS and third-party anti-malware tools treat the particular encryption technique with less suspicion, allowing Banshee to operate undetected for longer periods.
Stealing sensitive data
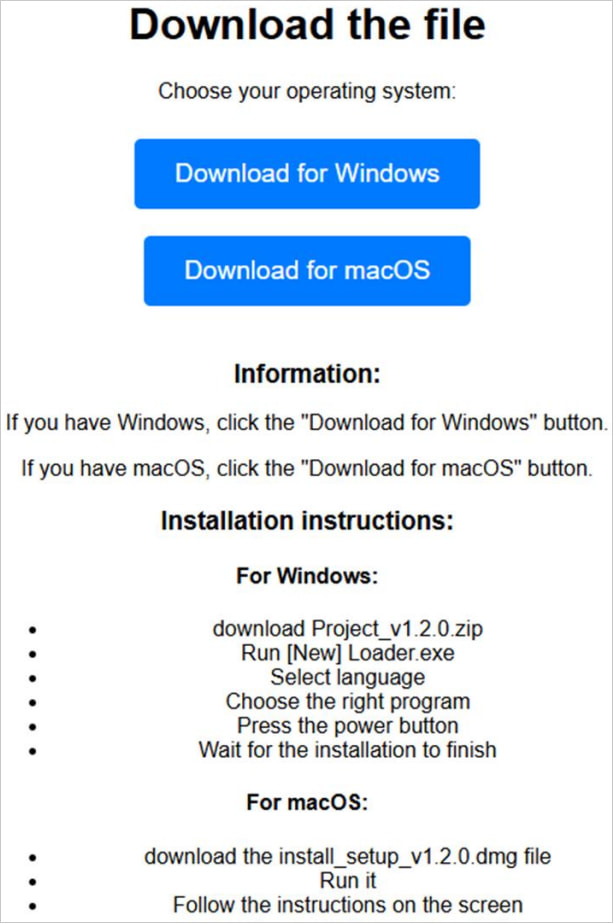
The latest Banshee stealer variant is primarily distributed via deceptive GitHub repositories targeting macOS users through software impersonation. The same operators also target Windows users, but with Lumma Stealer.
Source: Check Point
Check Point reports that while the Banshee malware-as-a-service operation has remained down since November, multiple phishing campaigns continued to distribute the malware since the source code leaked.
The infostealer targets data stored in popular browsers (e.g. Chrome, Brave, Edge, and Vivaldi), including passwords, two-factor authentication extensions, and cryptocurrency wallet extensions.
It also collects basic system and networking information about the host and serves victims deceptive login prompts to steal their macOS passwords.
Break down IAM silos like Bitpanda, KnowBe4, and PathAI
Broken IAM isn't just an IT problem - the impact ripples across your whole business.
This practical guide covers why traditional IAM practices fail to keep up with modern demands, examples of what "good" IAM looks like, and a simple checklist for building a scalable strategy.









Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now