
Researchers analyzing the electronic system for transactions and signatures used by the European Union member states found flaws that allowed impersonating any EU citizen.
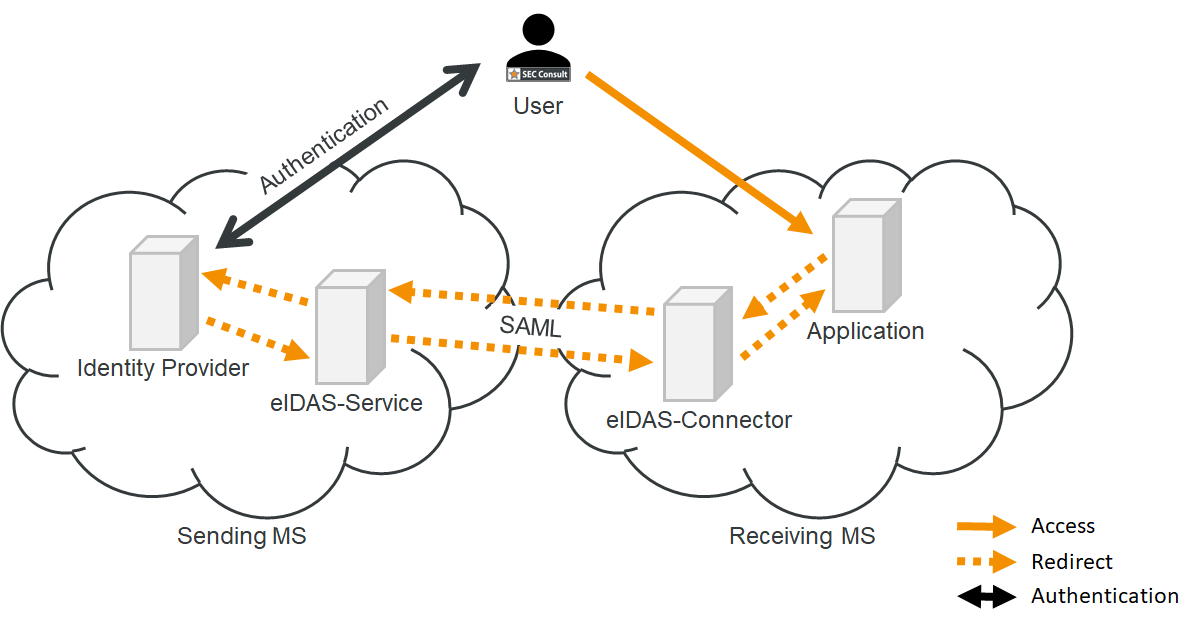
EU states use the eIDAS (electronic IDentification, Authentication, and trust Services) system to authenticate parties involved in online transactions (fund transfers, interaction with public services) and give them legal standing.
The standard allows citizens, businesses, and government entities in an EU state to access services in another member country in a secure way that involves validating them against national databases.
Insufficient checks
Vulnerability researchers from SEC Consult found two vulnerabilities in the eIDAS-Node Integration Package that facilitates communication with eIDAS nodes (Connector and Service) in each country.
The nodes exchange information using the Security Assertion Markup Language (SAML) open standard for authentication and authorization. This is a complex protocol prone to implementation errors, the researchers say.
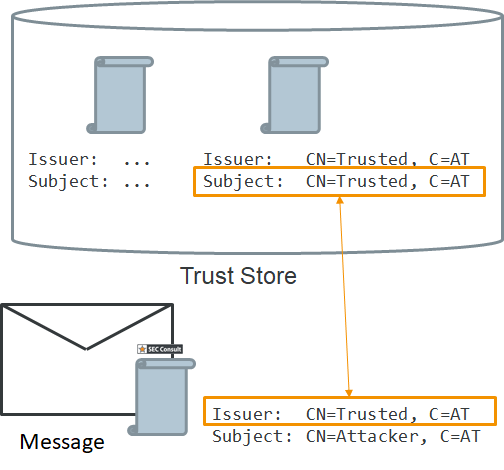
One of the weaknesses discovered allowed an attacker to avoid verification of the digital certificate signing the SAML message. Thus, threat actors could "send a manipulated SAML response to an eIDAS-Connector to authenticate as anybody."
The researchers explain that the certificate would be accepted if it was present in the local trust store. The problem was that validation was done by matching only the Distinguished Name (DN) information in the certificate received with the SAML response and the one in the trust store.
"Therefore, the entity certificate signature is not verified against the public key in the issuer certificate. An attacker can create a certificate with an arbitrary public key whose Issuer DN matches one of the Subject DN’s of the trusted certificates," SEC Consult writes in a report today.
The researchers created a video that demonstrates the flaw by authenticating with the name Johann Wolfgang von Goethe (yes, the famous18th-century German writer).
This vulnerability was found in version 2.3 of the eIDAS-Node component and the researchers reported it back in July. A patch is included in version 2.3.1, released today and available to all member states.
A similar flaw was found in an older version of the software, 2.1, which is no longer supported. Anyone using it is strongly recommended to install the latest release.
SEC Consult published proof-of-concept code to validate their findings.
This is not the first time SEC Consult researchers impersonated Goethe. Almost a year ago, they used it to demonstrate a flaw in the authentication process via German ID cards with RFID chips.
Break down IAM silos like Bitpanda, KnowBe4, and PathAI
Broken IAM isn't just an IT problem - the impact ripples across your whole business.
This practical guide covers why traditional IAM practices fail to keep up with modern demands, examples of what "good" IAM looks like, and a simple checklist for building a scalable strategy.









Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now