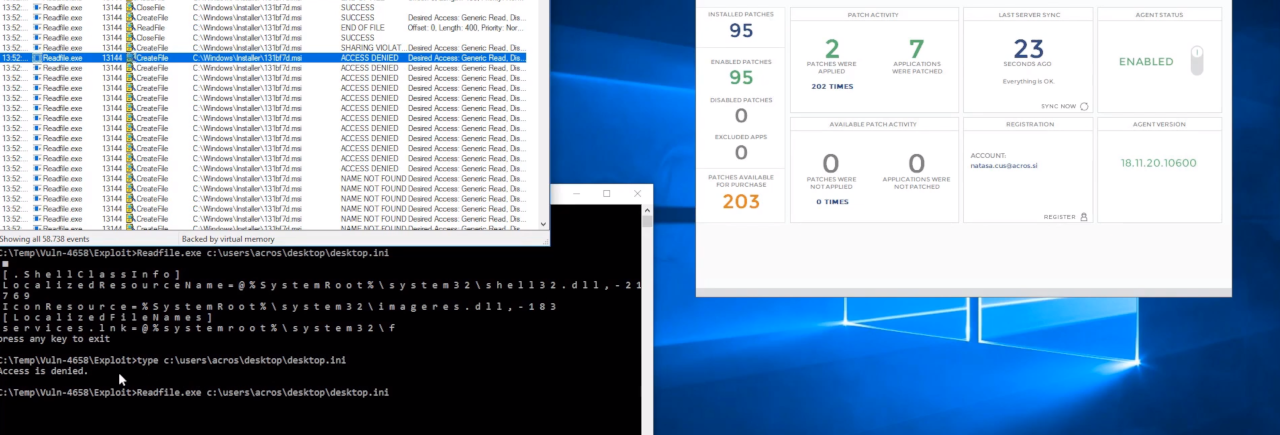
A micropatch is now available for a zero-day vulnerability in Windows that allows unauthorized read access with the highest privileges to any file on the operating system.
The temporary fix is for the third security bug released publicly by security researcher SandboxEscaper, and covered by BleepingComputer here.
An official patch from Microsoft is currently unavailable, although exploit code was published a month ago on GitHub, now a Microsoft-owned resource.
Interim fix to the rescue
Anyone looking to protect their systems from exploiting the "arbitrary file read vulnerability," as the researcher called it, can get a micropatch via the 0patch platform from Acros Security.
We have just issued a micropatch for SandboxEscaper's #readfile 0day. The vulnerability allows a local attacker to read arbitrary file on the system by exploiting Windows Installer's "advertisement" procedure. As always, the micropatch gets applied automatically - no reboot. pic.twitter.com/KxqlrRipql
— 0patch (@0patch) January 21, 2019
The video below shows how the exploit is rendered unsuccessful with the 0patch agent turned on:
The fix is free and works for the fully updated 64-bit Windows 10 version 1803 and 64-bit Windows 7. Users interested in a micropatch for other versions of the operating system should contact the company.
Fix was not easy to create
A day after SandboxEscaper disclosed the bug and the proof-of-concept code to exploit it, Acros Security CEO Mitja Kolsek said that they were hoping to get a micropatch out before the holidays.
Kolsek told BleepingComputer that the delay in pushing the fix today was because the patch was not an easy job. Also, the company's focus was on completing the beta stage for 0patch and getting everything ready for production.
An alert from the US CERT/CC says that exploitation of bug relies on a race condition vulnerability in Microsoft Windows MsiAdvertiseProduct function, "which can allow an authenticated attacker to elevate privileges to read" arbitrary files that are protected through the access control lists (ACL) on the filesystem.
On Friday, 0patch started to push a pro tem fix for another SandboxEscaper zero-day that can be exploited to overwrite files, including system ones. To demonstrate the validity of her exploit, the researcher overwrote the contents of 'pci.sys,' a system component tasked with correct booting of the operating system.
Kolsek says that the code corrections provided through 0patch should be considered temporary. Users should rely on the protection they provide only until an official patch becomes available.
Break down IAM silos like Bitpanda, KnowBe4, and PathAI
Broken IAM isn't just an IT problem - the impact ripples across your whole business.
This practical guide covers why traditional IAM practices fail to keep up with modern demands, examples of what "good" IAM looks like, and a simple checklist for building a scalable strategy.









Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now