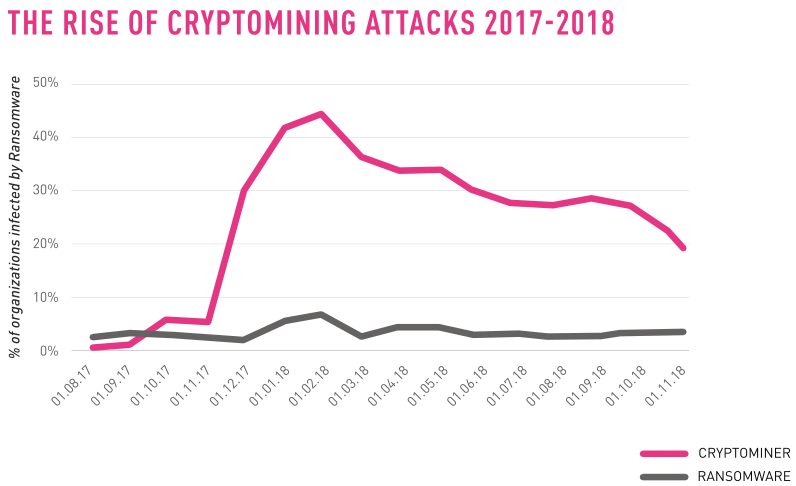
Cryptominers infected roughly ten times more organizations during 2018 than ransomware did, however only one in five security professionals knew that their company's systems have been impacted by a malware attack as reported by Check Point Research.
This follows a trend where threat actors have been doing their best to keep a low profile as much as possible, giving up on large scale ransomware attacks which get noticed immediately and switching to the harder to detect cryptojacking campaigns.
The ones that did not remove ransomware from their toolkit chose to be more specific with their attacks, targeting specific companies and individuals because of their higher profits potential.
Cryptojacking malware campaigns surreptitiously use a compromised computer's resources to mine cryptocurrency which is sent to crypto wallets owned by the threat actors which control it.
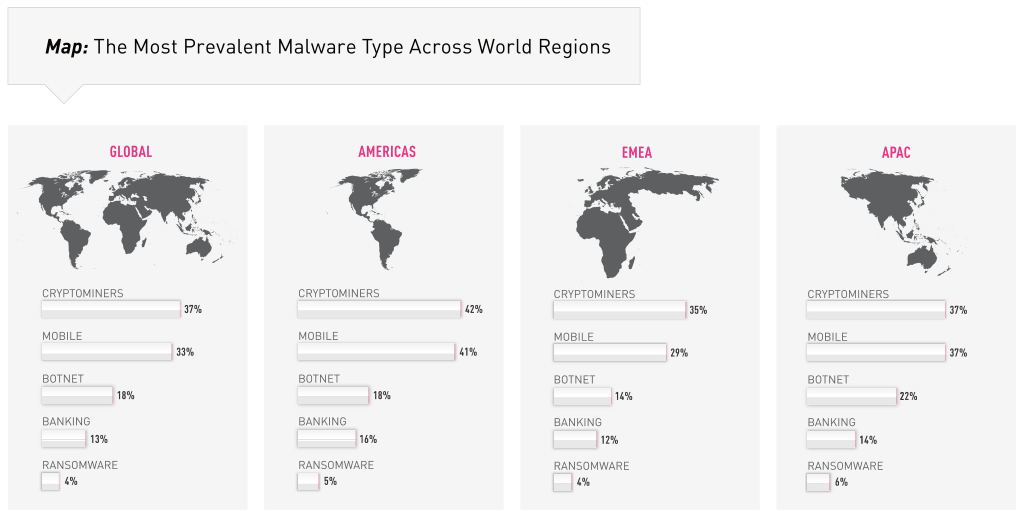
As detailed in Check Point's analysis, more and more malware families have also started to blend in new capabilities targeting cryptocurrency within their arsenal:
Ransomware, as well as prominent Banking Trojans, including Panda and TrickBot, are now targeting not only bank accounts but also cryptocurrency wallets and trading system accounts, adding features of cryptocurrency credential theft to their arsenal.
The cryptojacking campaigns that took the place of mass scale ransomware attacks have the advantage of being able to slide unnoticed on company networks, while also providing the bad actors with extra ways of using the compromised machines for their own profit.
To be more exact, once a network is infiltrated, the malware will also make it possible to drop other even more dangerous strains via built-in back doors if the attackers think it's necessary.
According to Check Point Research, "the most prominent cryptomining malware dominating the Global Top Cryptominers Malware list are Coinhive, CryptoLoot, and JSEcoin. These malware strains have also kept their place at the top of the list since 2017."
Cryptojacking allows threat actors to prolong their operations
Besides cryptojacking's stealthiness when compared to ransomware's obvious presence after the initial infection, attackers had a couple of other reasons for choosing to focus on amassing cryptocurrency.
First of all, ransomware attacks have become less and less effective, with fewer and fewer victims paying the ransoms (although WannaCry infected 400,000 computers it only earned $140,000 in total).
Secondly, given the constant drop in the value of cryptocoins such as Bitcoin, which are highly popular ransom payment currency, bad actors had to switch to another toolset to maintain their level of profits. Cryptojacking was the next best thing considering the high return on Investment (ROI) ratio.
Overall, the switch to cryptojacking campaigns provides threat actors with the means to lengthen their surreptitious operations and avoiding the scenario when their victims simply refuse to pay up ransoms.
Also, it enables them to always have a foothold within an organization's networks as long as the planted malware stays undetected, allowing for multi-stage attacks once they find a better way to profit from the compromised machines under their control.
While threat actors in the past were the ones who built and deployed their own tools, Malware-as-a-Service (MaaS) programs have been more and more prevalent during the past few years, with Dark Web platforms controlled by malware developers being the central place where cybercriminals can now shop around for the latest, most potent malware.
Additionally, "these forums serve as places where malware and tools crafted for malignant reasons can be traded or sold to affiliates and generate revenue without the developer being directly involved in an attack," says Check Point Research.
The online "malware shopping malls" also provide access to readily configured and simple to control malware kits, as well as stolen personal data that criminals can use as part of targeted attacks or to brute force their way into a computing system or organization network of their choice.
Malware markets provide a huge trove of malicious tools and services
Also, "The different Malware-as-a-Services available include the infamous AZORult, File-Locker and Kraken ransomware that made headlines over the past year. The authors of GandCrab ransomware even offer technical support and tutorial videos for their product."
While Dark Web markets have also been popular among malware developers as a marketing platform for their "merchandise," law enforcement agencies closed more and more of them and, in response, the malware markets have moved to more secure platforms such as Telegram.
On clandestine Telegram channels were malicious tools are promoted, threat actors who don't have the skills or the time to create their own can find anything from stolen data and custom-made hacking tools to phishing kits, botnets available for rent, and ransomware such as GandCrab with affiliate programs.
"Malware-as-a-Service provides everything a cyber criminal needs to get started and threatens modern organizations in two ways. It creates a demand for better, easier-to-use malicious programs, as malware developers seek to distinguish themselves from any competition. This leads to significant strides in the accessibility and sophistication of malware threats," Check Point Research concludes.
Break down IAM silos like Bitpanda, KnowBe4, and PathAI
Broken IAM isn't just an IT problem - the impact ripples across your whole business.
This practical guide covers why traditional IAM practices fail to keep up with modern demands, examples of what "good" IAM looks like, and a simple checklist for building a scalable strategy.









Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now