
The Akira ransomware gang was spotted using an unsecured webcam to launch encryption attacks on a victim's network, effectively circumventing Endpoint Detection and Response (EDR), which was blocking the encryptor in Windows.
Cybersecurity firm S-RM team discovered the unusual attack method during a recent incident response at one of their clients.
Notably, Akira only pivoted to the webcam after attempting to deploy encryptors on Windows, which were blocked by the victim's EDR solution.
Akira's unorthodox attack chain
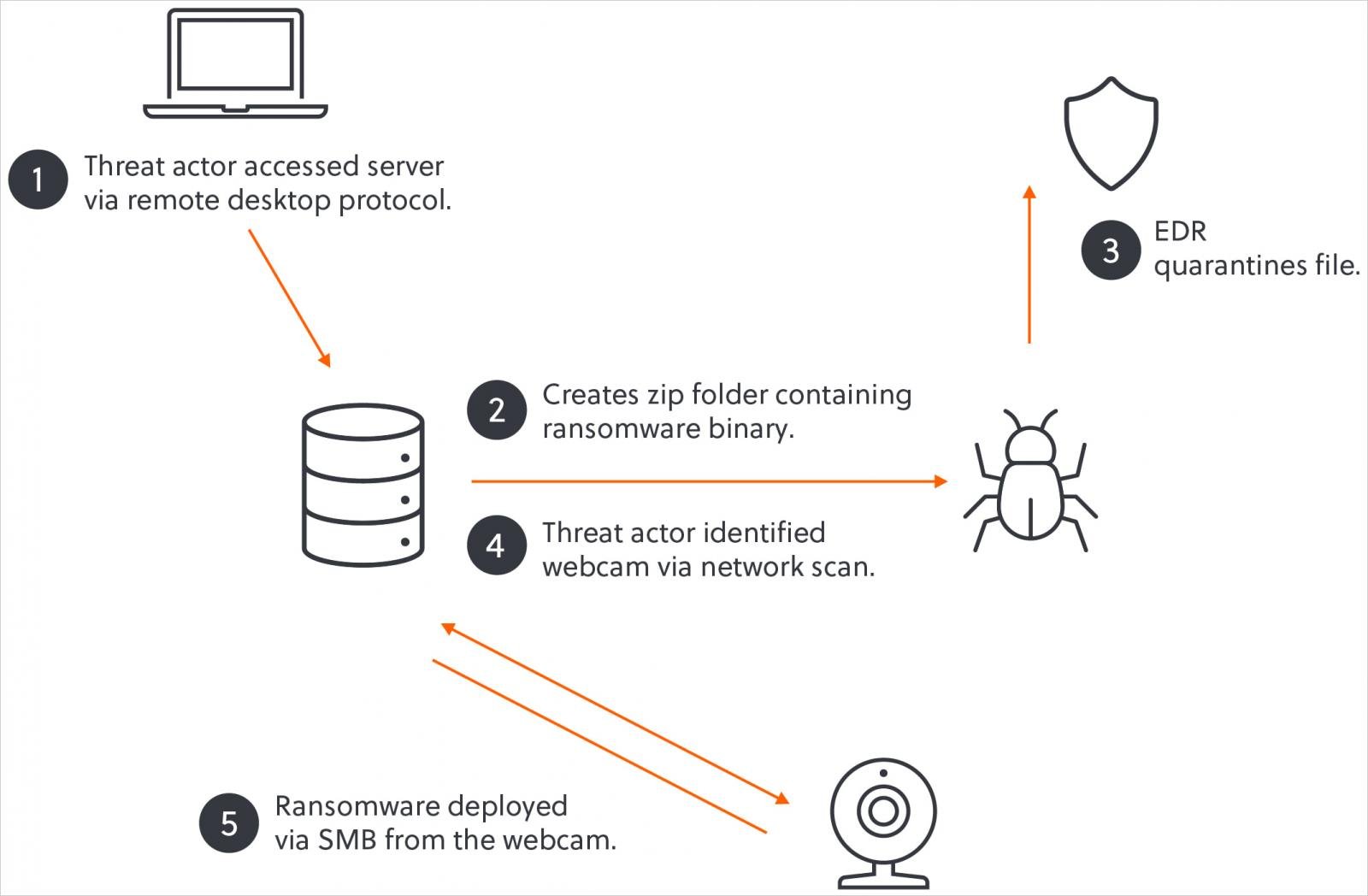
The threat actors initially gained access to the corporate network via an exposed remote access solution at the targeted company, likely by leveraging stolen credentials or brute-forcing the password.
After gaining access, they deployed AnyDesk, a legitimate remote access tool, and stole the company's data for use as part of the double extortion attack.
Next, Akira used Remote Desktop Protocol (RDP) to move laterally and expand their presence to as many systems as possible before deploying the ransomware payload.
Eventually, the threat actors dropped a password-protected ZIP file (win.zip) containing the ransomware payload (win.exe), but the victim's EDR tool detected and quarantined it, essentially blocking the attack.
After this failure, Akira explored alternative attack pathways, scanning the network for other devices that could be used to encrypt the files and finding a webcam and fingerprint scanner.
S-RM explains that the attackers opted for the webcam because it was vulnerable to remote shell access and unauthorized video feed viewing.
Furthermore, it ran on a Linux-based operating system compatible with Akira's Linux encryptor. It also did not have an EDR agent, making it an optimal device to remotely encrypt files on network shares.
Source: S-RM
S-RM confirmed to BleepingComputer that the threat actors utilized the webcam's Linux operating system to mount Windows SMB network shares of the company's other devices. They then launched the Linux encryptor on the webcam and used it to encrypt the network shares over SMB, effectively circumventing the EDR software on the network.
"As the device was not being monitored, the victim organisation's security team were unaware of the increase in malicious Server Message Block (SMB) traffic from the webcam to the impacted server, which otherwise may have alerted them," explains S-RM.
"Akira was subsequently able to encrypt files across the victim's network."
S-RM told BleepingComputer that there were patches available for the webcam flaws, meaning that the attack, or at least this vector, was avoidable.
The case shows that EDR protection isn't an all-encompassing security solution, and organizations shouldn't rely on it alone to protect against attacks.
Furthermore, IoT devices are not as closely monitored and maintained as computers but still pose a significant risk.
Due to this, these types of devices should be isolated from the more sensitive networks, like production servers and workstations.
Of equal importance, all devices, even IoT devices, should have their firmware updated regularly to patch known flaws that could be exploited in attacks.
Break down IAM silos like Bitpanda, KnowBe4, and PathAI
Broken IAM isn't just an IT problem - the impact ripples across your whole business.
This practical guide covers why traditional IAM practices fail to keep up with modern demands, examples of what "good" IAM looks like, and a simple checklist for building a scalable strategy.









Comments
scpcguy - 9 months ago
Goes to show that some days you can't win for losing in the CyberSecurity world. Interesting write-up and good information.
HurricaneAndrew - 9 months ago
Is this related to Edimax IP camera vulnerability or is it a separate issue?
deltasierra - 9 months ago
Ransomware being blocked by EDR should have raised ALL the alarm bells; things should have went into full IR and remediation mode. Instead, Akira had time to goof around some more and try this novel attack -- one that surprisingly worked! Something tells me that no one was actively managing this org's EDR solution.
feedbackbleeping938 - 9 months ago
You can’t handle people questioning your story, so you delete posts now.
Bleeping Computer has become less reliable, often reposting major news articles and publishing technically inaccurate stories. For instance, they recently reported on an SMB mount from a Linux camera deploying ransomware, but that doesn't make sense technically.
To clarify:
SMB from a camera: A camera would need to be compromised to act as an SMB server, which isn’t common. Systems don’t automatically mount SMB shares without specific configurations.
Execution of malware: Simply mounting an SMB share doesn’t trigger execution. A system would need prior compromise or user interaction for the ransomware to run.
EDR failure: Modern EDR systems would block this kind of attack, so it would require significant evasion techniques to bypass detection.
It seems like Bleeping Computer either oversimplified or misunderstood the technical aspects of this scenario, which damages their credibility.
woody188 - 9 months ago
An SMB server is not required to mount Windows SMB shares. Only a client is needed.
An EDR wouldn't detect the encryptor running over an SMB client. It might see the files being encrypted, but not the encryptor.
Some ransomware specific products could potentially detect the files being encrypted and disable the SMB or user account, but not EDR. Superna comes to mind, but these are enterprise SAN monitoring products. If they mounted admin shares and ran the encryptor over the network from the Linux based camera, game over.