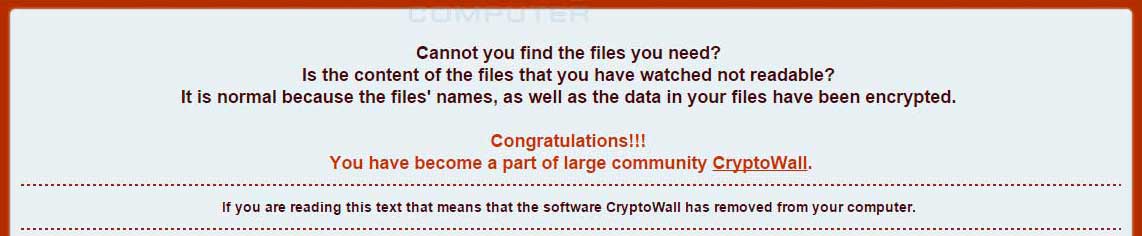
Brad Duncan, a security researcher for Rackspace and a ISC Handler, has posted a new ISC Handler Diary entry on how CryptoWall 4.0 has started being distributed through exploit kits. For quite some time, Brad has been following a particular criminal group called the "BizCN gate actor" and how they have been using exploit kits to distribute malware. Brad calls this group the BizCN gate actor because they use the Bizcn.com registrar to register the domains for all of their gateways. A gateway is the host that sits between a hacked site and the exploit kit landing page. On 11/20/2015, Brad noticed that the BizCN gate actor had switched from pushing CryptoWall 3.0 to the new CryptoWall 4.0 version.
The exploit kit that is currently being used by this group is the Nuclear Exploit Kit, which can be used to exploit vulnerabilities in programs that include Flash, Silverlight, PDF, Java, and Internet Explorer. These exploit kits are installed on hacked web sites, which redirect a victim user through a gateway to the exploit kit landing page. This landing page will then try to exploit a vulnerability, and if successful, deliver a malware payload that get's installed onto the victim's computer. Brad said in his diary that though other malware is installed as a payload from this group, the most common malware appears to be CryptoWall.
An interesting change, with how CryptoWall 4.0 is being distributed is the use of a NSIS installer to install CryptoWall on the infected machine. In the sample from Brad's site, malware-traffic-analysis.net, the NSIS installer includes some encrypted data files called MuskegCommuneKinesthesia and suppress.navigation.xml and a DLL called skiplanes.dll. The NSIS script shows that the installer is using this bundled DLL and passing along various arguments to install CryptoWall as shown below.
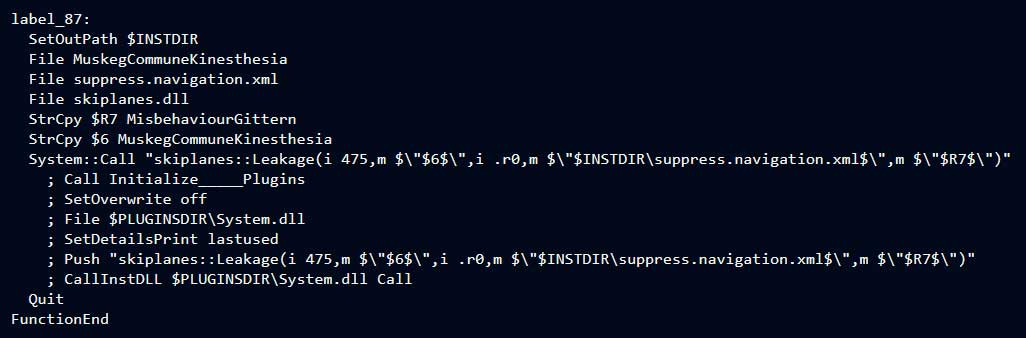
I do not have much experience with NSIS installers, but from what I have gathered the script is calling the Leakage function along with a variety of parameters. These parameters include the data file name of MuskegCommuneKinesthesia and the path to suppress.navigation.xml. If I would hazard a guess, this function is being used to decrypt the contents of suppress.navigation.xml, which is an executable that is then injected to install CryptoWall 4.0. If there is anyone who is more experienced with NSIS scripts and could elaborate further, please let us know.
If any further information is discovered about the NSIS installer, I will be sure to post it.
Break down IAM silos like Bitpanda, KnowBe4, and PathAI
Broken IAM isn't just an IT problem - the impact ripples across your whole business.
This practical guide covers why traditional IAM practices fail to keep up with modern demands, examples of what "good" IAM looks like, and a simple checklist for building a scalable strategy.









Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now