
The LockBit ransomware gang has suffered a data breach after its dark web affiliate panels were defaced and replaced with a message linking to a MySQL database dump.
All of the ransomware gang's admin panels now state. "Don't do crime CRIME IS BAD xoxo from Prague," with a link to download a "paneldb_dump.zip."
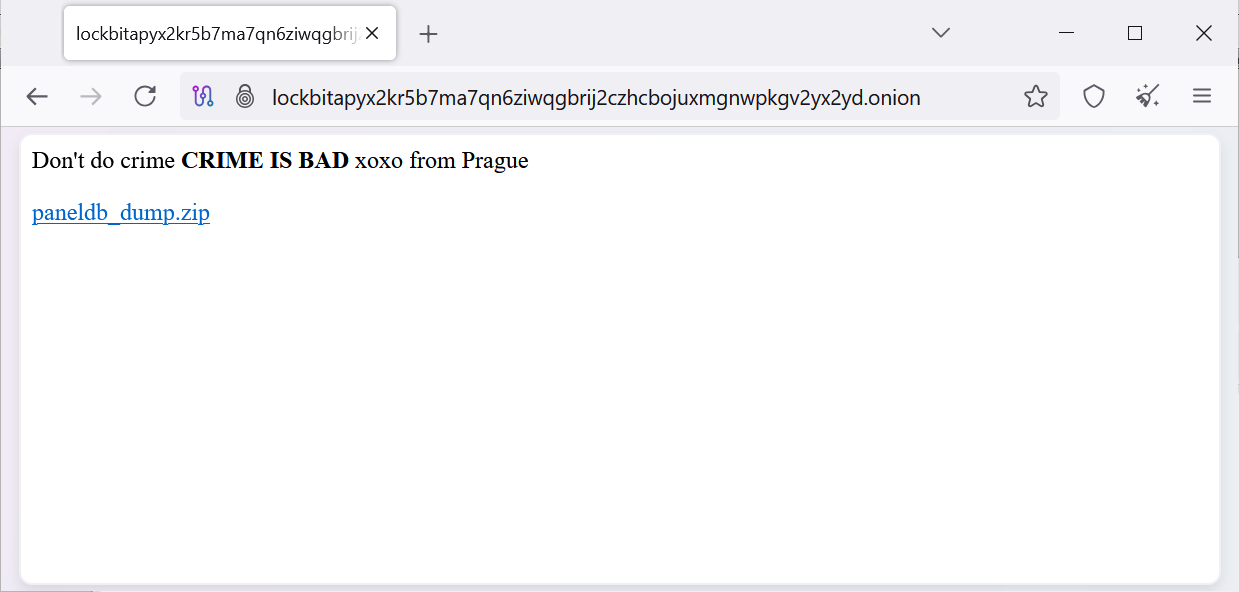
As first spotted by the threat actor, Rey, this archive contains a SQL file dumped from the site affiliate panel's MySQL database.
From analysis by BleepingComputer, this database contains twenty tables, with some more interesting than others, including:
- A 'btc_addresses' table that contains 59,975 unique bitcoin addresses.
- A 'builds' table contains the individual builds created by affiliates for attacks. Table rows contain the public keys, but no private keys, unfortunately. The targeted companies' names are also listed for some of the builds.
- A 'builds_configurations' table contains the different configurations used for each build, such as which ESXi servers to skip or files to encrypt.
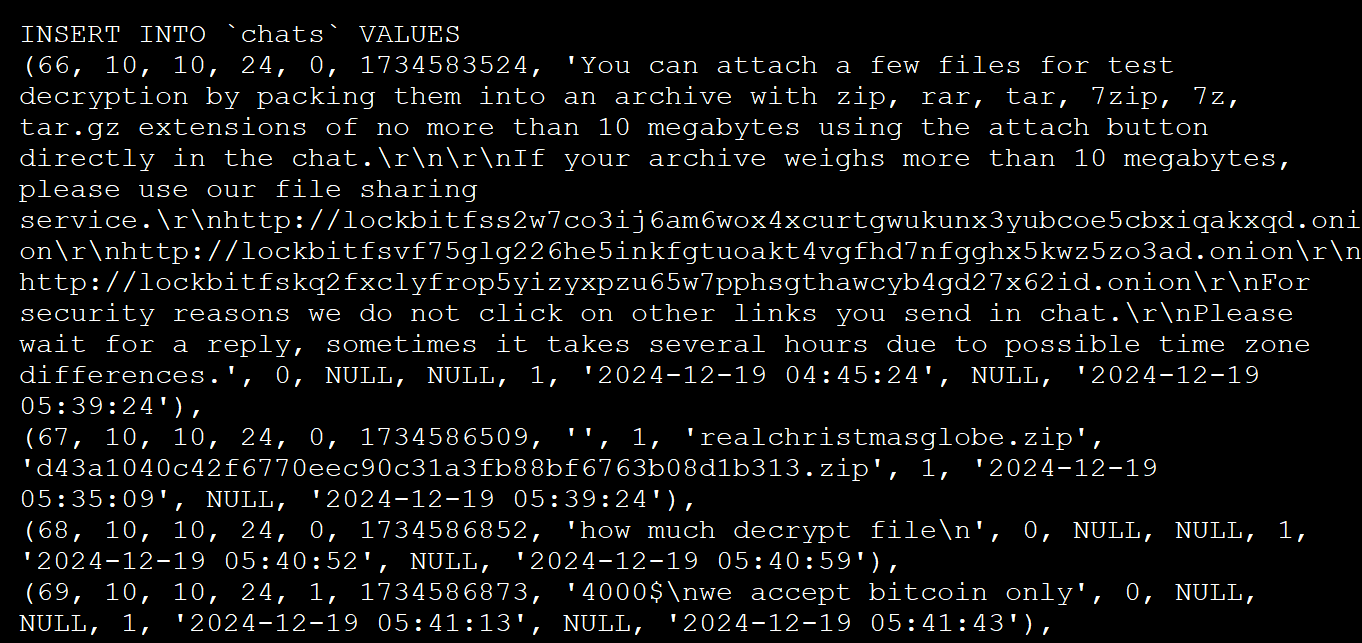
- A 'chats' table is very interesting as it contains 4,442 negotiation messages between the ransomware operation and victims from December 19th to April 29th.

Affiliate panel 'chats' table - A 'users' table lists 75 admins and affiliates who had access to the affiliate panel, with Michael Gillespie spotting that passwords were stored in plaintext. Examples of some of the plaintext passwords are 'Weekendlover69, 'MovingBricks69420', and 'Lockbitproud231'.
In a Tox conversation with Rey, the LockBit operator known as 'LockBitSupp' confirmed the breach, stating that no private keys were leaked or data lost.
Based on the MySQL dump generation time and the last date record in the negotiation chats table , the database appears to have been dumped at some point on April 29th, 2025.
It's unclear who carried out the breach and how it was done, but the defacement message matches the one used in a recent breach of Everest ransomware's dark web site, suggesting a possible link.
In 2024, a law enforcement operation called Operation Cronos took down LockBit's infrastructure, including 34 servers hosting the data leak website and its mirrors, data stolen from the victims, cryptocurrency addresses, 1,000 decryption keys, and the affiliate panel.
Although LockBit managed to rebuild and resume operations after the takedown, this latest breach strikes a further blow to its already damaged reputation.
It's too early to tell if this additional reputation hit will be the final nail in the coffin for the ransomware gang.
Other ransomware groups who have experienced similar leaks include Conti, Black Basta, and Everest.
Update 5/8/25: Updated article to remove potential PHP CVE the server was vulnerable to as that CVE only impacted Windows. Thanks Christopher.
Break down IAM silos like Bitpanda, KnowBe4, and PathAI
Broken IAM isn't just an IT problem - the impact ripples across your whole business.
This practical guide covers why traditional IAM practices fail to keep up with modern demands, examples of what "good" IAM looks like, and a simple checklist for building a scalable strategy.








Comments
NobodyImportant_69 - 7 months ago
This kind of news warms my heart.