-
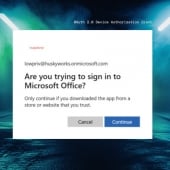
Microsoft 365 accounts targeted in wave of OAuth phishing attacks
Multiple threat actors are compromising Microsoft 365 accounts in phishing attacks that leverage the OAuth device code authorization mechanism.
- December 19, 2025
- 12:19 PM
 2
2
-
New ConsentFix attack hijacks Microsoft accounts via Azure CLI
A new variation of the ClickFix attack dubbed 'ConsentFix' abuses the Azure CLI OAuth app to hijack Microsoft accounts without the need for a password or to bypass multi-factor authentication (MFA) verifications.
- December 11, 2025
- 10:10 AM
 1
1
-
New Webinar: Choose Your Own Investigation — Browser Attack Edition

Modern attacks have shifted focus to the browser, yet detection tools remain largely blind to the crucial activity happening there.
Join Push Security on February 11th for an interactive "choose-your-own-adventure" webinar on ClickFix, credential phishing, and other in-browser attacks we've observed in the wild.
-
OAuth Device Code Phishing: Azure vs. Google Compared
Device code phishing abuses the OAuth device flow, and Google and Azure produce strikingly different attack surfaces. Register for Huntress Labs' Live Hack to learn about attack techniques, defensive tactics, and get an Identity Security Assessment.
- November 03, 2025
- 10:11 AM
 0
0
-
New CoPhish attack steals OAuth tokens via Copilot Studio agents
A new phishing technique dubbed 'CoPhish' weaponizes Microsoft Copilot Studio agents to deliver fraudulent OAuth consent requests via legitimate and trusted Microsoft domains.
- October 25, 2025
- 12:16 PM
 2
2
-
Find hidden malicious OAuth apps in Microsoft 365 using Cazadora
Malicious OAuth apps can hide inside Microsoft 365 tenants. Huntress Labs' Cazadora script helps uncover rogue apps before they lead to a breach. Dive deeper in their Tradecraft Tuesday sessions.
- October 20, 2025
- 10:00 AM
 0
0
-
Defend the Target, Not Just the Door: A Modern Plan for Google Workspace
The Salesloft Drift breach shows attackers don't need to "hack Google" — they just need to breach a trusted integration. Learn from Material Security how to secure OAuth, detect risky behavior, and protect data in Google Workspace.
- October 08, 2025
- 10:02 AM
 0
0
-
Webinar: Your browser is the breach — securing the modern web edge
The web browser has quietly become one of the most critical components of enterprise infrastructure—and one of the most dangerous. Join BleepingComputer, SC Media, and Push Security on September 29 at 12:00 PM ET for a live webinar on how attackers are targeting the browser to hijack sessions, steal data, and bypass security.
- September 16, 2025
- 07:01 AM
 0
0
-
6 browser-based attacks all security teams should be ready for in 2025
The browser is now the frontline for cyberattacks. From phishing kits and ClickFix lures to malicious OAuth apps and extensions, attackers are targeting the very place your employees access business-critical apps. Push Security explains how to defend where breaches begin.
- September 04, 2025
- 10:01 AM
 0
0
-
Salesloft breached to steal OAuth tokens for Salesforce data-theft attacks
Hackers breached sales automation platform Salesloft to steal OAuth and refresh tokens from its Drift chat agent integration with Salesforce to pivot to customer environments and exfiltrate data. The ShinyHunters extortion group claims responsibility for these additional Salesforce attacks.
- August 26, 2025
- 03:12 PM
 0
0
-
Hackers abuse OAuth 2.0 workflows to hijack Microsoft 365 accounts
Russian threat actors have been abusing legitimate OAuth 2.0 authentication workflows to hijack Microsoft 365 accounts of employees of organizations related to Ukraine and human rights.
- April 24, 2025
- 04:24 PM
 1
1
-
Fake "Security Alert" issues on GitHub use OAuth app to hijack accounts
A widespread phishing campaign has targeted nearly 12,000 GitHub repositories with fake "Security Alert" issues, tricking developers into authorizing a malicious OAuth app that grants attackers full control over their accounts and code.
- March 16, 2025
- 02:36 PM
 2
2
-
Malicious Adobe, DocuSign OAuth apps target Microsoft 365 accounts
Cybercriminals are promoting malicious Microsoft OAuth apps that masquerade as Adobe and DocuSign apps to deliver malware and steal Microsoft 365 accounts credentials.
- March 16, 2025
- 10:19 AM
 1
1
-
Google OAuth flaw lets attackers gain access to abandoned accounts
A weakness in Google's OAuth "Sign in with Google" feature could enable attackers that register domains of defunct startups to access sensitive data of former employee accounts linked to various software-as-a-service (SaaS) platforms.
- January 14, 2025
- 12:28 PM
 1
1
-
New details reveal how hackers hijacked 35 Google Chrome extensions
New details have emerged about a phishing campaign targeting Chrome browser extension developers that led to the compromise of at least thirty-five extensions to inject data-stealing code, including those from cybersecurity firm Cyberhaven.
- December 31, 2024
- 01:54 PM
 2
2
-
OAuth risks: How to identify, investigate, and mitigate them
OAuth apps can make our digital lives much easier, but it can also be a huge headache for security teams. Learn more from Nudge Security about these OAuth risks and how to investigate them.
- June 12, 2024
- 10:01 AM
 0
0
-
Microsoft: OAuth apps used to automate BEC and cryptomining attacks
Microsoft warns that financially-motivated threat actors are using OAuth applications to automate BEC and phishing attacks, push spam, and deploy VMs for cryptomining.
- December 12, 2023
- 06:53 PM
 0
0
-
Microsoft fixes Azure AD auth flaw enabling account takeover
Microsoft has addressed an Azure Active Directory (Azure AD) authentication flaw that could allow threat actors to escalate privileges and potentially fully take over the target's account.
- June 20, 2023
- 12:38 PM
 0
0
-
Microsoft disables verified partner accounts used for OAuth phishing
Microsoft has disabled multiple fraudulent, verified Microsoft Partner Network accounts for creating malicious OAuth applications that breached organizations' cloud environments to steal email.
- January 31, 2023
- 10:13 AM
 1
1
-
Microsoft: Exchange servers hacked via OAuth apps for phishing
Microsoft says a threat actor gained access to cloud tenants hosting Microsoft Exchange servers in credential stuffing attacks, with the end goal of deploying malicious OAuth applications and sending phishing emails.
- September 22, 2022
- 01:13 PM
 1
1
-
Heroku admits that customer credentials were stolen in cyberattack
Heroku has now revealed that the stolen GitHub integration OAuth tokens from last month further led to the compromise of an internal customer database. The Salesforce-owned cloud platform acknowledged the same compromised token was used by attackers to exfiltrate customers' hashed and salted passwords from "a database."
- May 05, 2022
- 04:06 AM
 0
0
- 1
- 2