
The lean-coded, fast, modern, and secure WireGuard VPN protocol has made it into the Linux kernel as Linus Torvalds merged it into his source tree for version 5.6.
The wait is closely coming to an end, with the next Linux kernel expected to be released in just a few months, considering that the latest refresh occurred on January 26.
First on the list
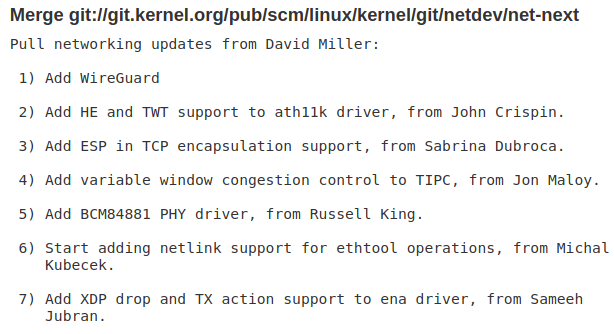
Around 1 a.m. CET on Wednesday, Torvalds pulled the networking updates from David Millers' repository, with WireGuard being at the top of the list.
Jason Donenfeld himself was excited about this step and shared that he tried to stay awake to see it happen, "refreshing Linus' git repo on my phone until I was dreaming."
"I look forward to start refining some of rougher areas of WireGuard now," announced the original author and developer of the project.
Torvalds is a supporter of the WireGuard project. When Donenfeld made the pull request in 2018 to have it integrated into the Linux kernel, Torvalds expressed hope that the merge would happen soon.
"Can I just once again state my love for [WireGuard] and hope it gets merged soon? Maybe the code isn't perfect, but I've skimmed it, and compared to the horrors that are OpenVPN and IPSec, it's a work of art" - Linus Torvalds
In March 2019, the man overseeing the big changes in the Linux kernel reiterated his support for the WireGuard project and the direction Donenfeld was leading it.
What is all the hype about
The WireGuard protocol and its implementation is a project from security researcher and kernel developer Jason Donenfeld, who created it as an alternative to IPsec and OpenVPN.
In its current form, WireGuard has about 4,000 lines of code, a fraction of the more than 100,000 what makes OpenVPN tick without the required OpenSSL or the hundreds of lines behind the IPsec VPN.
Compared to current options, WireGuard relies on a small set of carefully chosen modern cryptographic primitives that are stronger, perform better, have been under the scrutiny of cryptographers and received their vote.
- ChaCha20 for symmetric encryption, authenticated with Poly1305, using RFC7539's AEAD construction
- Curve25519 for ECDH (elliptic-curve Diffie-Hellman) key agreement
- BLAKE2s for hashing and keyed hashing, described in RFC7693
- SipHash24 for hashtable keys
- HKDF for key derivation, as described in RFC5869
WireGuard provides perfect forward secrecy, protection against denial-of-service, brute-force attacks, key impersonation, and replay attacks, as well as support for an additional layer of symmetric-key cryptography to offer some post-quantum resistance, as confirmed by this analysis from the Prosecco team of researchers at INRIA Paris.
As seen in the primitives listed above, it does away with offering choices for encryption, key encryption, and hashing algorithms. While this may be a problem for interoperability and backward compatibility, it also minimizes the risk resulting from insecure deployments and from supporting obsolete cryptographic algorithms.
As a whole, WireGuard is faster because it lives in the kernel space, easier to audit for security vulnerabilities, and simple to configure and deploy.
A technical paper include the low-level details that make this protocol what it is.
WireGuard was initially released for the Linux kernel but now it is cross-platform (Windows, macOS, BSD, iOS, Android) and widely deployable. It currently in development and the first stable release has yet to emerge.
However, some VPN service providers (Mullvad, AzireVPN, IVPN, VPN.ac, TorGuard) already offer WireGuard servers, showing that the code is sufficiently reliable for its purpose.
Break down IAM silos like Bitpanda, KnowBe4, and PathAI
Broken IAM isn't just an IT problem - the impact ripples across your whole business.
This practical guide covers why traditional IAM practices fail to keep up with modern demands, examples of what "good" IAM looks like, and a simple checklist for building a scalable strategy.









Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now