Security researchers have discovered a new exploitation technique that they say can bypass the kernel protection measures present in the Windows operating systems.
Discovered by security researchers Omri Misgav and Udi Yavo from enSilo, the technique is named Turning Tables, and exploits Windows' page tables.
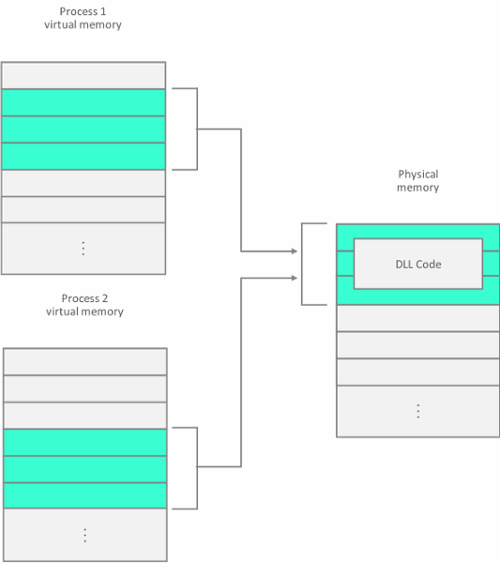
Page tables are a data structure common to all operating systems, not just Windows, that are used to store mappings between virtual memory and physical memory. Virtual addresses are used by the program executed by an OS process, while physical addresses are used by hardware components, and more specifically, by the RAM subsystem.
Because physical memory (RAM) is limited, operating systems create so-called "shared code pages" where multiple processes can store the same code and call upon it when needed.
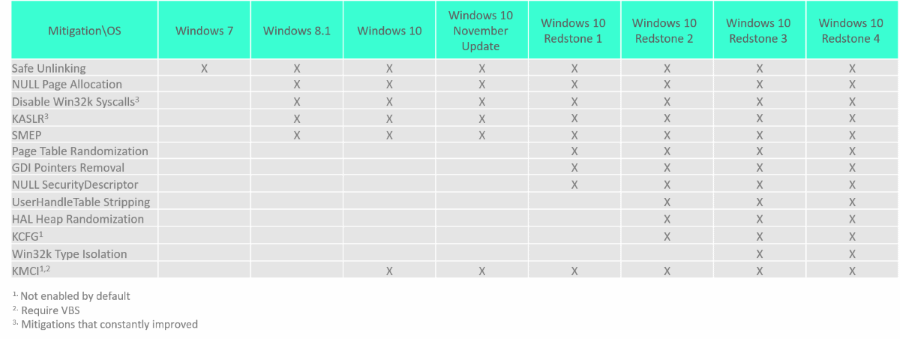
|
|
|
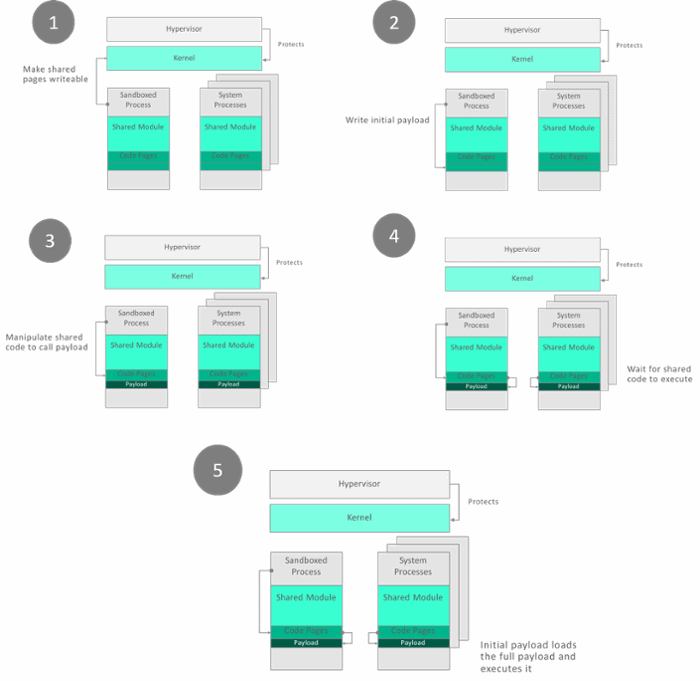
Misgav and Yavo say the Turning Tables technique relies on crafting malicious code that alters these "shared code pages" in a negative way to affect the execution of other processes, some of which have higher privileges.
By doing this, the Turning Tables technique allows attackers to elevate the privileges of their code to higher levels, such as SYSTEM.
The two enSilo researchers say the technique can also be used to alter applications running in sandboxes, which are isolated environments created for the sole purpose of protecting apps against such attacks. For example, Turning Tables can be used to poison browsers that run inside a sandbox, such as Chrome.
Turning Tables also impacts macOS, Linux
Furthermore, since the concept of page tables is also used by Apple and the Linux project, macOS and Linux are, in theory, also vulnerable to this technique, albeit the researchers have not verified such attacks, as of yet.
"The reason why is that the technique is based on an optimization leveraged by almost all modern operating systems," the enSilo team said.
But the thing that stands out about this technique the most is that it bypasses all the kernel-level security protections that Microsoft has added to the Windows OS in recent years, the researchers said.
The two enSilo researchers said they informed Microsoft about the Turning Tables technique. A Microsoft spokesperson was not available for comment before this article's publication.
Misgav and Yavo presented their research at the BSides Las Vegas security conference held at the start of the month. A recorded live stream of the conference's proceedings is available below. The Turning Tables presentation starts at the 8:57:26 mark. The slides presented at the conference are available here.
Break down IAM silos like Bitpanda, KnowBe4, and PathAI
Broken IAM isn't just an IT problem - the impact ripples across your whole business.
This practical guide covers why traditional IAM practices fail to keep up with modern demands, examples of what "good" IAM looks like, and a simple checklist for building a scalable strategy.









Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now