-
Fake Microsoft Office add-in tools push malware via SourceForge
Threat actors are abusing SourceForge to distribute fake Microsoft add-ins that install malware on victims' computers to both mine and steal cryptocurrency.
- April 08, 2025
- 04:53 PM
 2
2
-
Hackers weaponize Microsoft Visual Studio add-ins to push malware
Security researchers warn that hackers may start using Microsoft Visual Studio Tools for Office (VSTO) more often as method to achieve persistence and execute code on a target machine via malicious Office add-ins.
- February 02, 2023
- 03:23 PM
 0
0
-
New Webinar: Choose Your Own Investigation — Browser Attack Edition

Modern attacks have shifted focus to the browser, yet detection tools remain largely blind to the crucial activity happening there.
Join Push Security on February 11th for an interactive "choose-your-own-adventure" webinar on ClickFix, credential phishing, and other in-browser attacks we've observed in the wild.
-
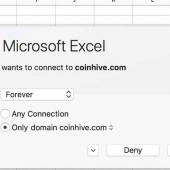
PoC Developed for CoinHive Mining In Excel Using Custom JavaScript Functions
Within days of Microsoft announcing that they are introducing custom JavaScript equations in Excel, a security researcher has developed a way to use this method to load the CoinHive in-browser JavaScript miner within Excel.
- May 08, 2018
- 10:13 PM
 0
0