
Sextortion emails stating that your computer was hacked and video was created of you on porn sites have become so common that many ignore them and treat them simply as another spam. That does not mean, though, that they are not profitable as a new report shows that the attackers are generating a decent revenue stream by utilizing infected PCs to do their dirty work.
For those who are not familiar with sextortion spam, they are emails that pretend to be from a hacker who states they installed software on your computer and was able to video you while on porn sites. They then demand anywhere between $300 USD to $5,000 USD in bitcoins or they will send the video to all of your contacts.
In a new report by Check Point Research, researchers show how the Phorpiex botnet is being used to distribute millions of sextortion emails and are generating a tidy sum doing so.
Phorpiex botnet makes you do the dirty work
The almost decade old Phorpiex botnet, otherwise known as Trik, is a worm that spreads via email. Once a machine is infected, the malware will download further malware onto an infected computer or perform other malicious activity, such as using the computer to send spam.
Check Point Research has recently discovered that Phorpiex has added a new payload that acts as a spam bot to distribute sextortion emails.
"The spam bot is one of the final payloads in each Phorpiex campaign observed in 2019," the researchers stated in their report. "The Phorpiex spam bot doesn’t have its own persistence mechanism, as it is downloaded and executed by other Phorpiex modules."
When installed, the spam bot module will connect to the malware's command & control servers and attempt to download email databases consisting of up to 20,000 email addresses per database. Some of these spam campaigns had 325 to 1363 email databases on a single command & control server, allowing an infected PC to spam millions of potential victims with sextortion emails like the one below.
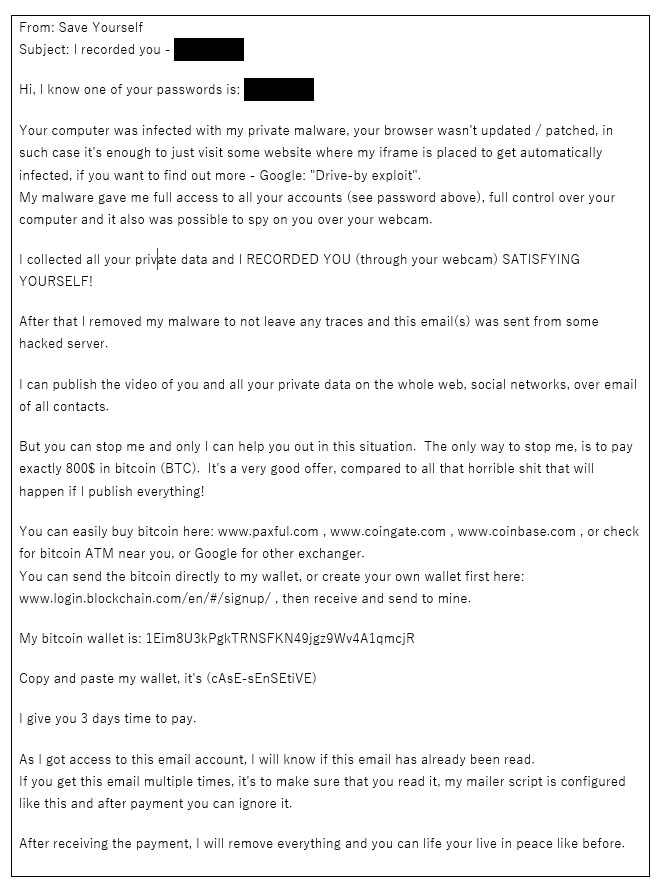
(Click to see full image)
Some of the campaigns also use email databases that include associated passwords that were revealed in data breaches. These passwords are added to the sextortion emails to add further legitimacy to the hacker's claims.
"The most interesting feature of the last spam campaigns is that Phorpiex/Trik spam bot uses databases with leaked passwords in combination with email addresses. A victim’s password usually included in a spam email message to make it more persuasive and show that password is known to the attacker. To shock the victim a spam message starts from the string with the password"
When sending the spam, Phorpiex will create 15,000 threads that are each individually used to send spam. Due to the large amount of active threads sending email at one time, Check Point estimates that a single infected device can send up to 30,000 sextortion emails per hour.

With this type of volume, the sextortion emails have been quite profitable for the Phorpiex botnet.
Easy money with little effort
By monitoring the sextortion emails distributed by this botnet, Check Point was able to keep tabs on the amount of payments being made from these exortion demands.
Since April 2019, the researchers monitored 74 bitcoin addresses and have seen a total of 157 payments totaling 11.99545 bitcoins. This comes out to approximately to $95,721.89 USD, or $16K per month, at today's prices over a period of 6 months.
Compared to other cyber threat such as the Sodinokibi Ransomware, where an affiliate earned $287,499.00 worth of ransom payments in just 72 hours, the sextortion earnings do not seem that great.
At the same time, it is important to remember that this is a final payload on an infected machine, the PC has already been wrung dry from other malicious activity, and there is little to no overhead of the spam bots.
This allows the threat actors to focus on other more lucrative tasks, while still earning a steady recurring revenue stream.
Break down IAM silos like Bitpanda, KnowBe4, and PathAI
Broken IAM isn't just an IT problem - the impact ripples across your whole business.
This practical guide covers why traditional IAM practices fail to keep up with modern demands, examples of what "good" IAM looks like, and a simple checklist for building a scalable strategy.









Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now