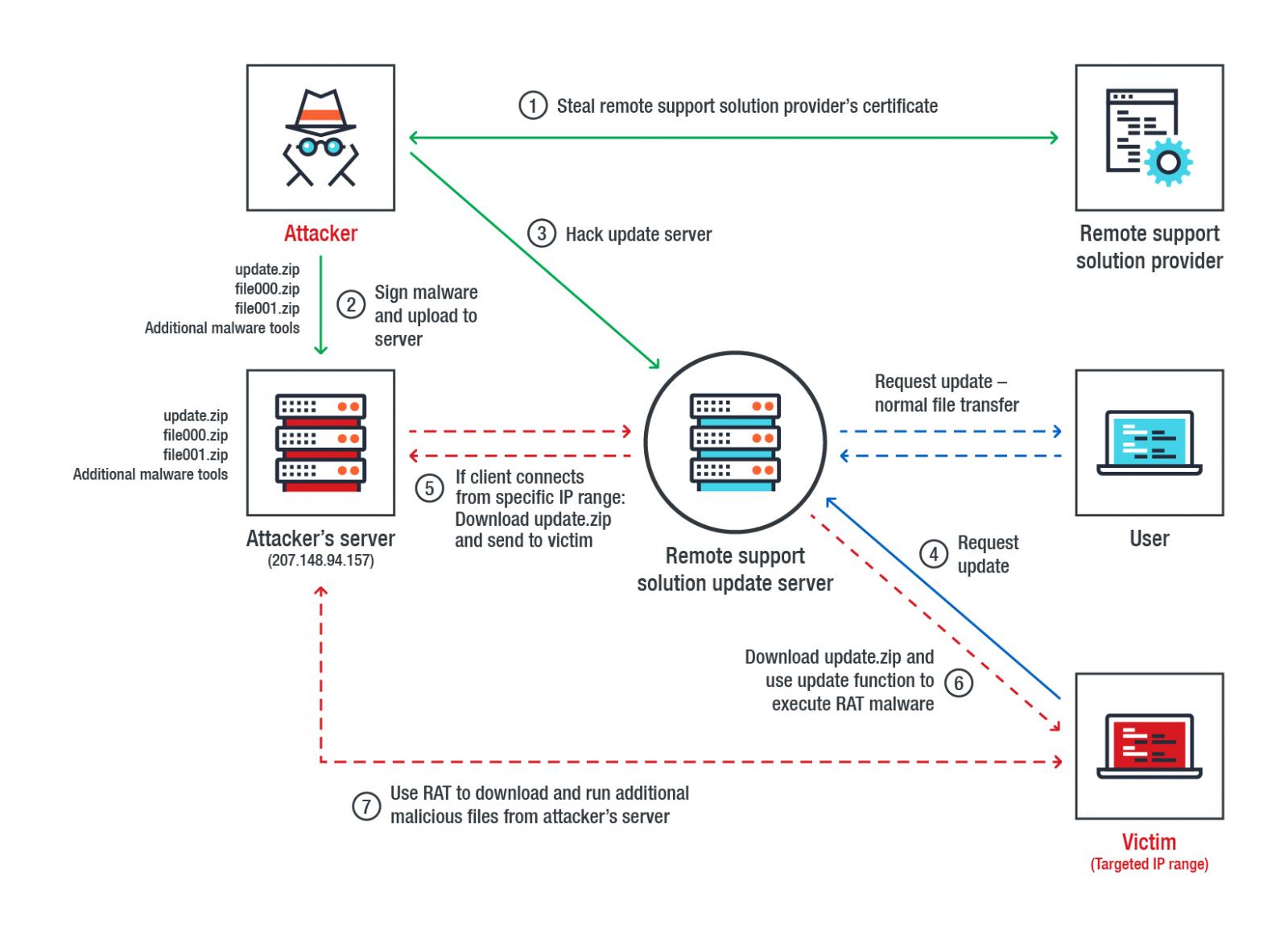
Security researchers have uncovered a new supply chain attack that targets organizations in South Korea. The threat actor chooses the victims selectively, based on an IP range for groups of interest.
Operation Red Signature popped on the researcher’s radar towards the end of July. To infiltrate the victims’ systems without triggering an alarm, the threat actor used the update server of a remote support solutions provider.
In a blog post today, TrendMicro’s Cyber Safety Solutions Team says that the compromised server was used to deliver an update tainted with a remote access tool called 9002 RAT.
The malicious actor made sure that the compromised version of the software did not spread to entities that were not of interest. For this, they set up the update server to send out the infected files only if their target was located within a specific range of IP addresses.
To avoid detection, the malicious update was signed with a valid certificate stolen from the remote solutions provider. It is unclear when this occurred, but researchers say that on April 8 they found a piece of malware that hid under the same stolen certificate.
With signed malware and access to the update server, all the threat actor had to do was to wait for a client to request a software update.
If the call came from the targeted IP range, the attacker sent the update server the malicious file packaged as “update.zip.” When the update executed, so did the 9002 RAT inside it.
“9002 RAT also installed additional malicious tools: an exploit tool for Internet Information Services (IIS) 6 WebDav (exploiting CVE-2017-7269) and an SQL database password dumper. These tools hint at how the attackers are also after data stored in their target’s web server and database,” says TrendMicro.
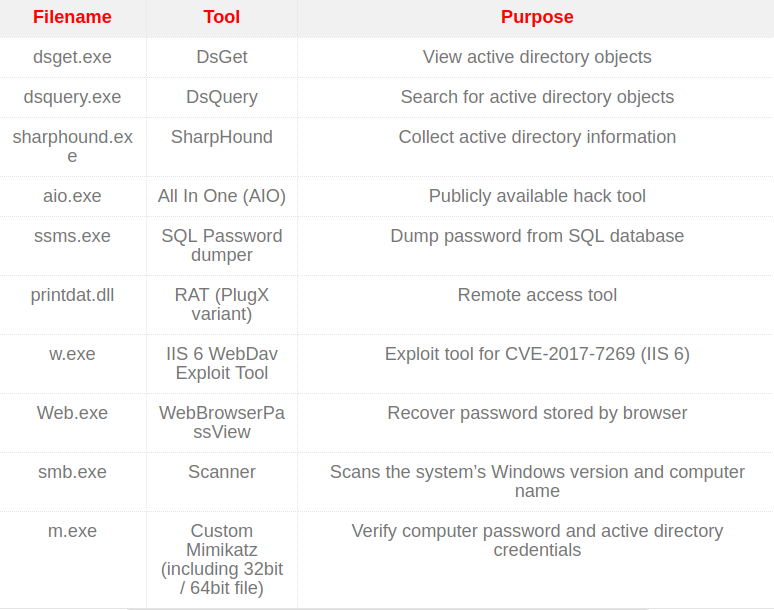
According to the researchers, the purpose of 9002 RAT is to collect information - a typical early stage activity. It was compiled on July 17 and was active starting the next day until July 31.The malware handlers set it to become inactive in August.
Supply-chain attacks growing popular
The same method was used for the NotPetya attack last year, which caused hundreds of millions of US dollars in damages to major companies across the globe.
An identical approach was used in the ShadowPad attack, which planted a backdoor in a server management software product for financial institutions.
A more recent incident is the one that contaminated CCleaner utility program, infecting more than two million machines.
Like Operation Red Signature, both the ShadowPad and the CCleaner attack relied on valid certificates that signed the compromised version of the software distributed to victims. This allows the threat actor to remain under the radar for a longer period and prepare new stages of the attack.
Supply-chain attacks are very difficult to detect and prevent because malware comes from an outside source considered trustworthy. Contaminating the waterhole, though, is sometimes easier to achieve than going directly after the target, who may have strong defenses in place.
Break down IAM silos like Bitpanda, KnowBe4, and PathAI
Broken IAM isn't just an IT problem - the impact ripples across your whole business.
This practical guide covers why traditional IAM practices fail to keep up with modern demands, examples of what "good" IAM looks like, and a simple checklist for building a scalable strategy.









Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now