
A database with over 200GB of data was found on a server left defenseless and open to public query, to anyone knowing where to find it.
The storage included about 445 million customer records from Veeam, a Swiss-based company that provides intelligent data management services for virtual, physical and cloud infrastructures.
Security researcher Bob Diachenko discovered the trove of information on Amazon infrastructure on September 5 and saw it vanish four days later, suggesting that the company heeded his notifications and took steps to secure its MongoDB server.
The exposure time of the records is uncertain, but according to Diachenko the IP address of the server had been indexed by Shodan on August 31.
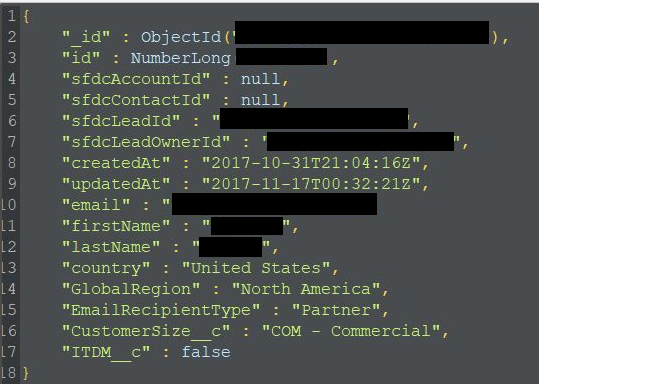
The collection consisted of customer personal information such as first and last name, email address, and country of residence.
Diachenko says that additional details available on the server included marketing attributes, like the type of customer and organization size (enterprise, commercial, SMB), IP addresses, referrer URLs, or user agent.
Looking for details that could help him determine the owner of the server, Diachenko discovered entries created as far back as four years ago.
Veeam counts about 307,000 customers. Among them are Norwegian Cruise Line, Gatwick Airport, Scania, healthcare and educational institutions (several universities and school districts).
Miscofigured MongoDB should be exinct by now
MongoDB was initially used for access from local networks. As its use went beyond these confinements, administrators continued to rely on the default setup, which was not ready for online access.
Starting version 2.6.0, MongoDB no longer allows networked connections unless the administrator explicitly configures them. This was implemented in the most popular deployment packages, RPM and DEB, about five years ago.
Ever since the first misconfigured instances of MongoDB have been reported, cybercriminals began building an extortion business around them.
They search the internet for open-access servers, may export the content, delete it and leave instead a ransom note.
One of the latest campaigns is Mongo Lock. The attackers behind it have automated the operation.
However, as reported by BleepingComputer, the scripts are unreliable and sometimes create the ransom note but leave the data intact.
Veeam replied to a request for comments from BleepingComputer, saying that the information was part of their marketing databases, and was exposed to third parties for a short period.
"It has been brought to our attention that one of our marketing databases, leaving a number of non-sensitive records (i.e. prospect email addresses), was possibly visible to third parties for a short period of time. We have now ensured that ALL Veeam databases are secure. Veeam takes data privacy and security very seriously, and a full investigation is currently underway," reads the statement from Veeam
Break down IAM silos like Bitpanda, KnowBe4, and PathAI
Broken IAM isn't just an IT problem - the impact ripples across your whole business.
This practical guide covers why traditional IAM practices fail to keep up with modern demands, examples of what "good" IAM looks like, and a simple checklist for building a scalable strategy.









Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now