
An exploit for a vulnerability in Tor Browser was delivered today in a tweet that left sufficient room for comments. A security vulnerabilities broker disclosed the details because it no longer served its purpose.
The exploit was part of Zerodium's portfolio and worked for Tor Browser 7.x. It existed in the NoScript component, which is a browser add-on that stops web pages from executing JavaScript, Flash, Java or Silverlight.
An exploit that one can only assume Zerodium paid good money for, is just a matter of setting the Content-Type of the attacker's HTML/JS page, or a hidden service in the Tor network, to "text/html/json," to suppress any reaction from NoScript and permit all JavaScript code through.
The bug worked when the user configured NoScript to block out all JavaScript by selecting the add-on's "Safest" security level.
Advisory: Tor Browser 7.x has a serious vuln/bugdoor leading to full bypass of Tor / NoScript 'Safest' security level (supposed to block all JS).
— Zerodium (@Zerodium) September 10, 2018
PoC: Set the Content-Type of your html/js page to "text/html;/json" and enjoy full JS pwnage. Newly released Tor 8.x is Not affected.
The recently released Tor Browser 8 is based on the new Firefox Quantum engine and did not inherit the flaw; neither is the latest NoScript version, which was re-written as a web extension.
Zerodium burning this exploit was also prompted by the fact that Tor Browser, like all modern browsers, comes with an auto-update mechanism, which is enabled by default.
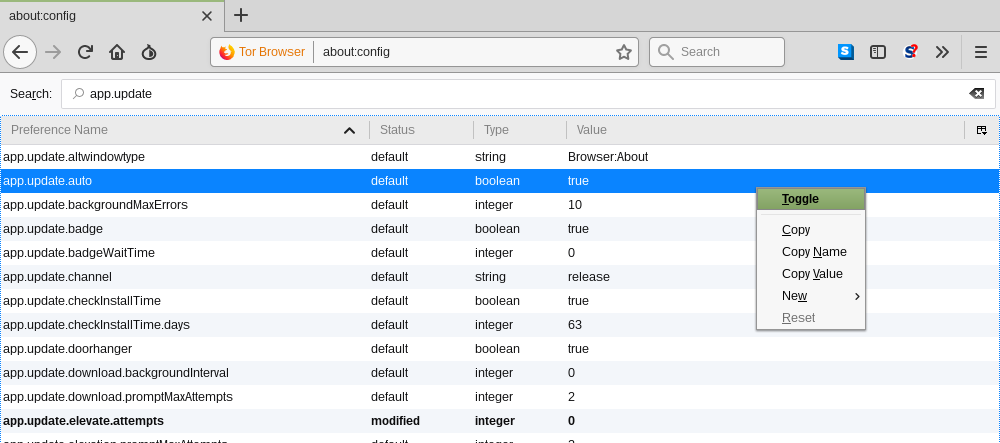
This makes sure that users are not affected in any way by exploits that have already been addressed. One can disable this feature from the 'app.update' parameter in the 'about:config' menu.
While some users prefer to deploy updates manually for sensitive software such as Tor Browser, the mechanism proves beneficial in such instances.
Giorgio Maone, the developer of NoScript, said today on Twitter that he updated the classic version of the add-on to 5.1.8.7, which continues to be actively developed for users of Firefox 52 ESR (Extended Support Release).
The release notes for the new release 'thank' Zerodium for "unresponsible disclosure."
Fixed in 5.1.8.7 "Classic": https://t.co/UVKqsYJ7vN
— Giorgio Maone (@ma1) September 10, 2018
You may need to open about:config and set your xpinstall.signatures.required to false in order to install, since @mozilla's @mozamo doesn't support signatures for legacy add-ons anymore.
cc: @torproject , @campuscodi
Break down IAM silos like Bitpanda, KnowBe4, and PathAI
Broken IAM isn't just an IT problem - the impact ripples across your whole business.
This practical guide covers why traditional IAM practices fail to keep up with modern demands, examples of what "good" IAM looks like, and a simple checklist for building a scalable strategy.









Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now