
Microsoft has confirmed the August 2024 Windows security updates are causing Linux booting issues on dual-boot systems with Secure Boot enabled.
The issue is caused by a Secure Boot Advanced Targeting (SBAT) update applied to block Linux boot loaders unpatched against the CVE-2022-2601 GRUB2 Secure Boot bypass vulnerability.
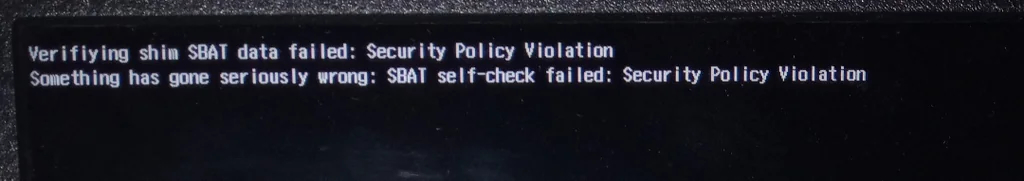
"Resulting from this issue, your device might fail to boot Linux and show the error message 'Verifying shim SBAT data failed: Security Policy Violation. Something has gone seriously wrong: SBAT self-check failed: Security Policy Violation,'" Microsoft explained.
"The August 2024 Windows security update applies a Secure Boot Advanced Targeting (SBAT) setting to devices that run Windows to block old, vulnerable boot managers."
The company added that the SBAT update designed to block vulnerable UEFI shim bootloaders will not be delivered to devices where dual booting is detected.
However, it also acknowledged that "the dual-boot detection did not detect some customized methods of dual-booting and applied the SBAT value when it should not have been applied."
As BleepingComputer reported on Tuesday, many Linux users confirmed they were affected following this month's Patch Tuesday. They say that their systems (running Ubuntu, Linux Mint, Zorin OS, Puppy Linux, and other distros) stopped booting into Linux after installing the August security updates on the Windows OS.
What if you already updated?
Linux users who tried working around this known issue say that suggested solutions like deleting the SBAT policy or wiping the Windows installation, and then restoring Secure Boot to factory settings will not work on all affected devices.
The only verified way to revive any impacted system is to disable Secure Boot, install the latest version of your favorite Linux distro, and re-enable Secure Boot.
Microsoft also provided a workaround for those who haven't yet completed the installation of the August 2024 security updates by rebooting, which requires using the following opt-out registry key to interrupt the deployment process and stop the buggy updates from installing:
reg add HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecureBoot\SBAT /v OptOut /d 1 /t REG_DWORD
The company is investigating the issue with its Linux partners and will provide an update when more details are available.
Break down IAM silos like Bitpanda, KnowBe4, and PathAI
Broken IAM isn't just an IT problem - the impact ripples across your whole business.
This practical guide covers why traditional IAM practices fail to keep up with modern demands, examples of what "good" IAM looks like, and a simple checklist for building a scalable strategy.









Comments
doncoyote - 1 year ago
"Our updates worked exactly as planned."
NoneRain - 1 year ago
These assumptions that MS care enough about dual booting to go after it don't make sense.
They did what they have being doing for the last decade: automated testing + push to prod, that's all. It's pure incompetence rather than malicious intent.
Seeprime - 1 year ago
Laying off the 10,000 QA team nine years ago is making Microsoft's complex software more fragile and breakable more and more over time.
NoneRain - 1 year ago
AI will fix QA, trust us - MS, probably