A new version of the TeslaCrypt Ransomware has been discovered by BloodDolly, the creator of TeslaDecoder, that was built on January 12, 2016 @ 09:39:43. This release calls itself version 3.0 and uses a different encryption key exchange algorithm. Furthermore, all encrypted files will now have the new .XXX, .TTT, .MICRO extensions appended to them.
The major and most problematic change, though, is key exchange being modified. In the past there were ways to recover the private key from an encrypted file. Now with this modification, this is longer possible for new victims. BloodDolly is currently analyzing the new algorithm and as more information is available, we will post it at BC.
Maybe I am reading too much into the time of the year and trying to find sneaky things left by malware developers, but I find the autorun key to be interesting. The autorun key used by the TeslaCrypt installer is called meryHmas. The fact that we are around the holidays, leads me to believe that the developer is having a little fun at the victim's expense. Then again, I could be reading something from nothing.
Update 1/13/16: Updated the article to reflect that TeslaCrypt is not using a different encryption algorithm, but rather a different protection/key exchange algorithm.
Update 1/14/16: TeslaCrypt 3.0 has been updated to use the .TTT extension for encrypted files.
Update 1/15/16: TeslaCrypt 3.0 has been updated to use the .Micro Extension
Related Files:
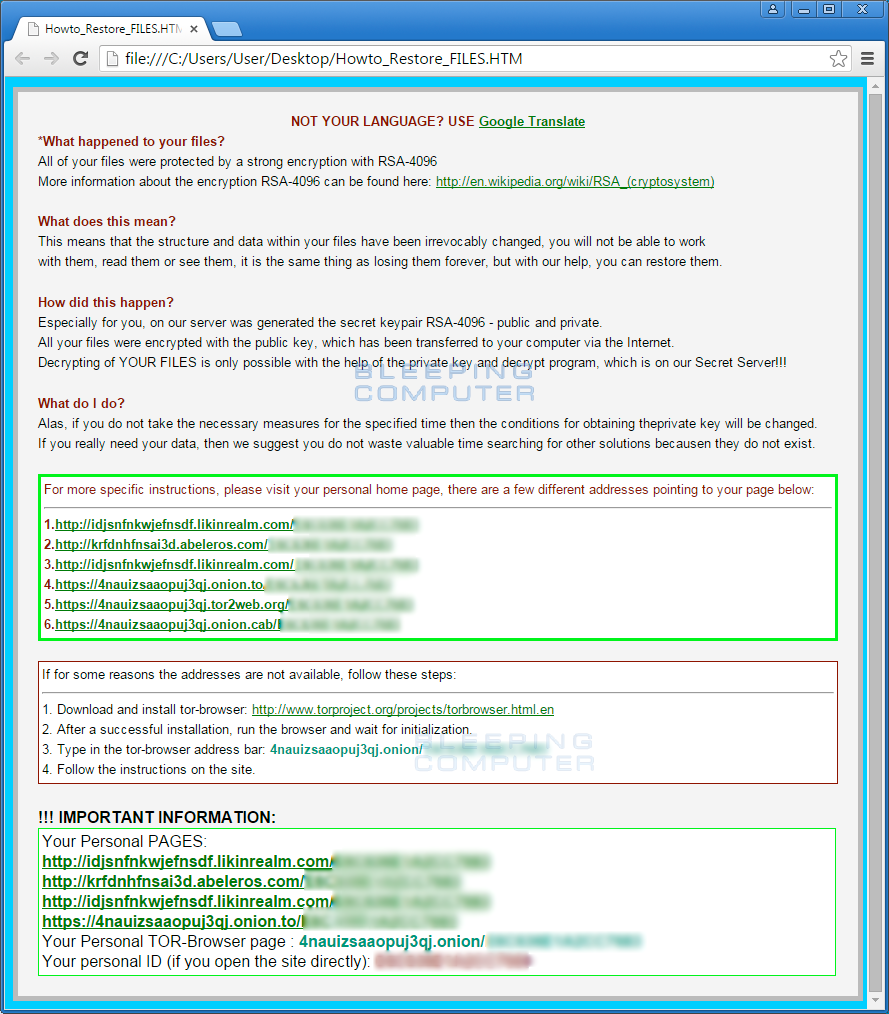
C:\Users\User\Desktop\Howto_Restore_FILES.BMP
C:\Users\User\Desktop\Howto_Restore_FILES.HTM
C:\Users\User\Desktop\Howto_Restore_FILES.TXT
C:\Users\User\Documents\recover_file_[random].txt
C:\Users\[username]\AppData\Roaming\[random].exe
Related Registry Keys:
HKCU\Software\Microsoft\Windows\CurrentVersion\Run\meryHmas C:\Users\[username]\AppData\Roaming\[random].exe
HKCU\Software\[random]
HKCU\Software\xxxsys
Break down IAM silos like Bitpanda, KnowBe4, and PathAI
Broken IAM isn't just an IT problem - the impact ripples across your whole business.
This practical guide covers why traditional IAM practices fail to keep up with modern demands, examples of what "good" IAM looks like, and a simple checklist for building a scalable strategy.









Comments
Zeone - 9 years ago
.Great tools.Thanks BloodDolly.
jfyang - 9 years ago
Dear all
my computer is attacked by malware, so called, telsacrypt 3. now all the data in my computer is encrypted with extension file format of .mp3. I noticed so many people also suffered from this problem. may I ask does any body find any effective way to recover the data. thanks
vilhavekktesla - 9 years ago
As you expected, a new verison is ready for field tesiting, hmm.
Do you know what... there is only one remedy and that is constant backup, rendering these ransom-"requests" futive. Unfortunately doing backup is way to complicated for everyone to do it, so maybe the best fight back is education.
Angoid - 9 years ago
There are plenty of backup tools out there to help you, and to make it easy. There are fewer and fewer excuses to not back up every day.
I've been using the AOMEI Backupper tool:
http://www.backup-utility.com/free-backup-software.html
There is also Acronis True Image:
http://www.acronis.com/en-gb/personal/computer-backup/
And then there is also EaseUS:
http://www.easeus.com/backup-software/
Education is great - we need that. Coupled with keeping good backups, this is a formidable weapon against the onslaught of ransomware.
vilhavekktesla - 9 years ago
Hi, Angoid. Go out on the streat in your city. Pick 200 people as they pass you, and ask about backups :) They will certainly fill you with excuses. You might even get the question, what is backup:) I informed about 1000 people I knew about a few days after 1. december a new ransomware is active. Only a few reacted, how do I protect my self, and what can I do to manage. My simple answer that time was backups / copies before you are attacked.
The one I was helping had a backup from 2014-9 so I could restore the computer to that stage. I for instance removed my NAS-drives and need to implement other backup routines.
So yes I do agree, there are noe excuses, but never the less we still loos some data every now and then. This ransomware is at least a big warning shot and eyopener. And as go with education I'm thinking of involving the media in my country, as Lawrence said, possibly only TV-media will help against these threaths. Youtube is not my thing (regarding own privacy among others)
I use Macrium image backup for drives and data files. In free personal version
the backup routin can do dfferential backup saving som space. In payed version you can do similar things as Aomei in pro version. I did not knew about aomi, so I will check it out. In Macrium free I can make xml-settings files helping the users to manage themselves, but as of today, I have been the one to setup the system in the first place and I can't force anyone to do backup. And I'm reluctant setting up scheduled backups unless I know the need space and remaining space on backup media.
Needles to say, the users that have hade a harddrive crash or infection in the past are the easiest to educate:)
yasarsahbaz - 9 years ago
Hello. how to fix .micro virus? Where is the download link?
vilhavekktesla - 9 years ago
Hi, please PM BloodDolly for more information and guidance
tech91 - 9 years ago
have you found the key? how can I write and Blood Dolly?
ahmedrufai - 9 years ago
My laptop has just been infected with the new version of the TeslaCrypt. It's crazy!!!!
Can it be reversed? Or is that just it? Nearly 1TB of data all gone... ?
Someone please help
Hunting.Targ - 9 years ago
You should take your situation here:
https://www.bleepingcomputer.com/forums/f/79/security/
That's the best place to start.
vilhavekktesla - 9 years ago
Hi, please PM BloodDolly for more information and guidance
lcurros - 9 years ago
Hi!
I've just been infected by this variant of teslacrypt.
Most of my files are encrypted with extension ttt.
Fortunatelly most of information was in backup.
For BloodDolly: Two misterious files was in "my documents" folder. I thinlk they take some kind of relation with encryption key. They are recover_file_odswmfyst.txt and recover_file_kgsaletmk.txt.
Their content is something like a key:
1EbudjAVnSXiz2ui67dtjXCSsHeHK6X85F
047D8EACE16E258202F424FCCD98BFDD0BF9ADA7F04E7508DB99B967C22972CD4D8D102FCEAE613D36E3EDF4F49DADB40F10057A19DC9EA0C80BABD5C33.........and more
Could be in this files the key tp recover the information???
vilhavekktesla - 9 years ago
Hi, please PM BloodDolly for more information and guidance
Lawrence Abrams - 9 years ago
At this point there is no way to decrypt this version. If anything is discovered we will be sure to publish it.
vilhavekktesla - 9 years ago
And for the rest there are a few active forums these day discussing different types of Tesla-enryption. One is speciffically for rescuing data the other discusses parts of tesla among others.
Both forums might have interesting information forr all users.
Here are the two links. Please read the first post in each forum-thread giving you an idea what it is all about.
https://www.bleepingcomputer.com/forums/t/601379/teslacrypt-vvv-ccc-etc-files-decryption-support-requests/
https://www.bleepingcomputer.com/forums/t/576600/tesladecoder-released-to-decrypt-exx-ezz-ecc-files-encrypted-by-teslacrypt/
RickCP - 9 years ago
Thanks for another good informational article, Grinler.
Noted a missing 'NO' in second paragraph you may wish to correct... "Now with this modification, this is [NO] longer possible for new victims."
tech91 - 9 years ago
Hi, I have been attacked by this virus. I have some important files with extension .micro. I cleared the virus. Now I try to run as administrator KeyFinder 1.0.0.0 analyze any PC but can not find the key. The type of encryption is RSA-4096.
What can I do to find the key. Help me I have some important files. Thanks to anyone answer me.
savioldp - 9 years ago
Hello,
related to virus infection tesla v.3 with .micro files, as we hope to be found a solution, an idea emerged that applied may bring us a solution.
the idea is:
1 - Backing up the infected PC.
2 - Disconnect the PC from other networks
3 - Connect the PC infected the Internet
4 - Use any network sniffer tool (Wireshak, SniffPass, NetworkMiner or other)
5 - Create clean file to force an infection.
6 - Using the network sniffer and try capiturar the key decryption
I hope this idea will help us in some way to find a possible solution, but need help from members who have deeper knowledge to apply this idea and the results.
I'm sorry for my English.
Demonslay335 - 9 years ago
Afraid that would not help at all. The key is encrypted with AES256 before it is sent over the network, which only reveals another layer that is guarded with ECHD. You would have to have the private key that the malware developers have in order to decrypt the encryption key. It is under multiple layers of encryption. It would take hundreds of years for a supercomputer to brute-force it even if you do capture the network packets.
alexandraa05 - 9 years ago
hi guys, I was infected yesterday by the Tesla virus and all my files was converted to .micro. could you be so kind to inform me about what I need to do to recover my files and delete the virus? thanks!!!
GrumpyToo2 - 9 years ago
Used norton and malware bytes to remove teslascript. Hoping it has worked - so far so good!
Believe some members are working on decyption routine for .mirco files, but no solution yet (other than restore from backup!), as yet......unless some else has an update? Currently patiently waiting, hoping to be able to get files back!
GrumpyToo2 - 9 years ago
Used norton and malware bytes to remove teslascript. Hoping it has worked - so far so good!
Believe some members are working on decyption routine for .mirco files, but no solution yet (other than restore from backup!), as yet......unless some else has an update? Currently patiently waiting, hoping to be able to get files back!
DEEKAY123456 - 9 years ago
hi guys my all data encrypted RSA 4096 shows .micro format pllz help me how can i recover my all lost data.
DEEKAY123456 - 9 years ago
hi guys my all data encrypted RSA 4096 shows .micro format pllz help me how can i recover my all lost data.
gurpreetsinghsaini - 9 years ago
I have all the files extension encrypted to .micro....it has also effected the google drive. Where in all the files in google drive has also been affected.
Please help. I have kids photos right when they were born and I will lose them.
Demonslay335 - 9 years ago
We are still working on a solution, no developments at this time I'm afraid.
For Google Drive, you can try reverting to previous versions of files.
https://support.google.com/drive/answer/2409045?hl=en
vip5786 - 9 years ago
My computer infected and change all my xls file to xls.micro. File can open but content cannot be read.
Is there any way to fixed ? plz tell me the solution dear................ Thanks
Sneakydude - 9 years ago
Network drive - data drive was hit with the .micro encrytption virus crytpo.
It broke the mirror Thursday night shadowcopy the person used the server for a day, then the server and the master computer came up with the virus
The only files i can find on the server is the .micro
It effected mostly the pdf, txt, word, excel etc... which its suppose to do. It was a standard network share.
used malwarebytes, and hitman pro no detections found so far. Running a few more tools.
Since it is a network encryption and only shared to this one directory i am forced to rebuild the data from whatever backup source i can find.
moved over from https://www.bleepingcomputer.com/forums/t/543518/decryption-keys-are-now-freely-available-for-victims-of-cryptolocker/page-10
apologize for the incorrect virus link.
Edit = I am not able to see the shadow copy version of 2003 server and no .micro files showing. It broke the mirror and it showed the files on thurs. I am extracting those data dir files now. Wish me luck....
Sneakydude - 9 years ago
Server had 16000 files damaged with .micro
Server had only the effected shared data directory.
Server also had 2 entries in the applications data folders called crypto.
Server had 0 virus entries.
All is good was able to rebuild the mirror, data restored and it only lost 2 days of work which did not effect the server. It did however cost this company a butt load of time and employee stares.
Workstation, 3000-4000 virus entries found with eset online scanner.
Malwarebytes found 1620 entries on the computer of various garbage, nothing else.
Eset online scanner also called it win32/fileencoder.TeslaCrypt Trojan renaming all files mostly as .micro listed in the top section.
Since this is a mirror of the orginal setup, i am going to remove the variants and restore and re mirror it from an existing machine. change the lic and drive forward.
I do recommend people concider having a 5 day cycle backup system to restore from, since these type of problems can cause major issues.
Hope to have helped someone out there.
Daniel2 - 9 years ago
Hi, My entire Harddrive was infected with TeslaCrypt 3.0 as well. I lost a whole bunch of data, including every single e-book and all of my families pictures. The backup drive was infected as well. All files now have the .micro ending. I´m not rich since im a 24 year old student from Germany but i would gladly pay some genius for coming up with a way to decrypt the .micro ending. Thank you all for your efforts guys. You are doing a great job and helping a lot of people!
DanielGl - 9 years ago
Hi
I have some encrypted files with the TeslaCrypt 3.0...
Also i have a decryption tool and a personal key to decrypt the files.
Would these help to create a general decryption tool for other?
Demonslay335 - 9 years ago
Unfortunately not, the key is unique for every victim. TeslaDecoder already has the capabilities to decrypt files if you are able to obtain the private key for the victim. It will be of no use to use your key on other's files.
lakeway9 - 9 years ago
This is the best site i recommend for removing Teslacrypt virus / .micro file extension virus check out at http://sureshotsoftware.com/guides/micro-file-virus
Demonslay335 - 9 years ago
The article simply puts a link to SpyHunter and says to restore from backups. There is no new information here that isn't already in the BleepingComputer guide.
mznu6968 - 9 years ago
High (these types of viruses are among the most dangerous – all affected data is made unusable and cannot always be recovered). There also may be a Trojan in your system.Or visit this web site.
http://sureshotsoftware.com/guides/teslacrypt-mp3/
lovly52452 - 9 years ago
Thanks a lot sing up your web site
http://sureshotsoftware.com/guides/teslacrypt-mp3/
TechniSmart - 9 years ago
Why is the latest Malware Antimalwarebytes Pro blocking this site as malicious?
nabook1 - 9 years ago
How can I find the private key??
Demonslay335 - 9 years ago
There is no way to obtain the private keys without paying the ransom at this time.
syu888 - 9 years ago
Hello Fellow Crypto Victims,
While I am waiting for a decryption tool for Tesla Crypto 3.0 (crossing my fingers), I just used Shadow Explorer (http://www.shadowexplorer.com/downloads.html) to recover some of the most important files from my laptop. The process was pretty easy and fast but it only worked on my main drive C and I am running Win 7 Pro 32-bit. I hope this is helpful to some of you and good luck in recovering your important files.
syu888 - 9 years ago
Hi All,
Is Malwarebytes still the best free malware removal tool? Does anyone have any experience (good/bad) using SpyHunter? Thanks in advance for your help.
GrumpyToo2 - 9 years ago
Did a search on the web for Tesla and got SpyHunter come up. On first glance it looks like it will even fix your encrypted files. Sadly it doesn't, but the marketing sounds like it can. Read somewhere it hard to un install too. Stuck with Malwarebytes, and after some comments on the web I am sure SpyHunter is not for me!
aquananu - 9 years ago
where can we share the files which could be helpful to Bloodydolly
Demonslay335 - 9 years ago
There is no need, we do not need any more samples. How the ransomware works has been deciphered for a long time - it is a matter of solving a large math problem pretty much, and seeing if it is possible to do within our lifetime.
jcpense - 9 years ago
Is there any way we can help with the math? Would more computational power help?
NarcisWBI - 9 years ago
Hello! I removed the "virus" from computer with Nod32. Now i still waiting a solution for encrypted files with .micro. All photo is corupted.
y0d4 - 9 years ago
is there some updates for new ver.? (3.0)
nensns - 9 years ago
this is my recover_file_ogrgdhwxa.txt
this is content:
1JWC8Qi9tG4yP5xHpMJZ4RvNuMXA1WFNKZ
044F742A8234C1566197AF652B84C327719F8CBA10981527D8A6CC80C39F5835BE69BD1CACC90769EE47D4E4E540AE664A254B57744BF2D9F46D633CBC3A454E4C2AE7385D53C03280FF42D79C0F36F1D7EE97BFE7AAB3B37E9446A9C06F241580
96974F3C6F4DC74
40
and this is key for this:
0A44940C499C95D9617B9C9FF2864F5C09FE0011B7C6788F88B72475F0935CF1
We pay runsom but key is not funcional.
Probably becouse we have two recovery files.
other is:
recover_file_rgwuwobjd.txt
this is content:
1LG2t8CkBYDuDr5qmn8fs7dXP24XvjA8cp
04E31BE6F483E4DB0F8951371B412A24C0C10960FA8EC11694386220AF55D155A735980E1BD60B27AFED15B68230ED364AE6CD2E3EEDBACCEFDE447379876F64D31721FD1855906CBEFC8A9227C6DEBB11A190BE9AE304DBB7B75869482506696C
9DFFD55210BBFC65
40
if somebody can decode this I will appreciate.
AND MOST IMPORTANT
DON'T PAY RANSOM THERE IS NO GUARANTEE THAT IT WILL WORK
1 FILE DEMO DECRYPTION ON SITE WORK FINE BUT ON YOUR PC WONT WORK
wojtekoxx - 9 years ago
dude, first time when I decrypted files it DIDN'T WORK, but I tried second time and it worked. Also, decryptor runs out of memmory quite fast, so you must use it on every main folder on all your disks. I mean, if your disk E has 5 folders, you must use "dictionary" option 5 times! Don't use it for whole disk at once, and never use "decrypt all" option
nensns - 9 years ago
Hi all,
After negotiating with hijackers I got new key which work.
sttools - 9 years ago
Ok .... the payment did not work ?
Did someone pay already and got all files restored sucessfully?
wojtekoxx - 9 years ago
I paid and got the files
sttools - 9 years ago
Me also, I paid and am able to decrypt.
cmarrero - 9 years ago
I'm getting desperate and about to blow $500 in bitcoins. For those of you that paid, has the decrypter been legit or do you get screwed either way?
Demonslay335 - 9 years ago
As long as the criminals give you the correct private key, you will be able to decrypt your data using TeslaDecoder (recommended over trusting an executable from the same people who infected you).
cmarrero - 9 years ago
thanks. I guess i'll try in the morning
vito1985 - 9 years ago
@cmarrero you mean tesladecoder works with .micro extansion?????
Demonslay335 - 9 years ago
Yes, TeslaDecoder works with .micro files... IF YOU HAVE THE PRIVATE KEY. There is no way to get this key yet, other than paying the ransom.
cmarrero - 9 years ago
I was going to pay the ransom to get the key and then use tesladecoder. I'll let you know how it goes
cmarrero - 9 years ago
Paid the ransom. Got the key. Decrypting seems to be working so far.
bmois - 9 years ago
Can you tell us which was the procedure to decrypt your files? They just send you the decryption key and you have used some free program to decrypt them or they send you also a program ?
Where did you find your public key ?
Demonslay335 - 9 years ago
If you pay the ransom, they provide you with the private key, and a decrypter. I would recommend using TeslaDecoder instead; better than trusting an executable from those who just infected you. You don't need the public key, as it is embedded in the files, and the decrypter takes care of that.
bmois - 9 years ago
One of my computers in the network has been infected. All of the files in this computer have been encrypted and renamed with .micro extension. Also a lot of files in shared folders in the network have been encrypted too.
How can I participate on efforts for finding a solution? I am a programmer and I think that I can help somehow.
sn00ky - 9 years ago
I too have been affected by this. Been using computers for 15 years and they finally got me!
5000 songs, 13000 family photos, numerous other files, gonzo to the extension of .micro.
First question is, and I know the obvious answer is "yes" but; is this from downloading torrents?
More specifically, I have been downloading torrents for years, no issue as I don't execute any files until I am aware of what they are, and certainly no exe files. I only downloaded files...
How does the ransom-ware virus infiltrate if nothing is executed? Or is things being executed within, or due to, my torrent software that I am not aware of?
Second question is; Is there any harm what-so-ever to keeping the .micro files, just in case there is a shred of hope of being able to get them back? I don't mind the disk usage, just want to be sure it isn't going to further infect other data?
I have deleted the *.html, *.jpg and *.txt files it left hanging around in all my folders; you know, the "I screwed your day" files...
Thanks to any and all support!
Demonslay335 - 9 years ago
The biggest spread of TeslaCrypt currently is hacked websites with the Angler exploit kit, and malicious email attachments. Haven't heard of anyone specifically hit by torrents, but never out of the question.
The encrypted files themselves are not malicious, and are safe to archive for future decryption (hopefully). The virus usually deletes itself, but make sure to run scans to make sure. I would definiltey run MalwareBytes Anti-Malware for starters. If you believe you may still have an infection, you can post a topic in the "Am I Infected?" forums (make sure to note that you only want assistance with the malware, and are aware data cannot be decrypted as of now).
sn00ky - 9 years ago
That's interesting, what do you mean by the Angler exploit kit? I don't even use this computer for email anymore, so that wouldn't be it. Hrm, any suggestions on how to narrow in the cause / source?
Thanks for the info on the files, will archive and hope!
Currently re-imaging my drive, which should take care of the problem (image is from 2 years go well before the infection).
Once that's complete I will run more scans and post to the mentioned topic.
Thanks!
Demonslay335 - 9 years ago
It's like a drive-by "shotgun" of exploits that gets injected into websites and tries to attack you on multiple fronts at once. There are several such exploit kits being sold on the dark web as "services", but Angler has become one of the biggest threats lately, right next to Nuclear.
Here's a good article on Angler, without diving straight into technical analysis.
https://heimdalsecurity.com/blog/ultimate-guide-angler-exploit-kit-non-technical-people/
giacomobe - 9 years ago
Hi,
In most case the exe file is downoaded by a js file.. I think.. the first way to neutralize this virus should be update a list of sites who host this exe file and block by the firewall.
Does it exists a list like this?
Vehab123 - 9 years ago
http://sureshotsoftware.com/guides/teslacrypt-mp3/
Vehab123 - 9 years ago
http://sureshotsoftware.com/guides/teslacrypt-mp3/
nensns - 9 years ago
Hi all,
After negotiating with hijackers I got new key which work.
McMicroHater - 9 years ago
share the key please!
adhiea7x - 9 years ago
hey dude,, I also infected file tesla v30, all the files into a micro dot extension,, I had to reinstall my computer. if the file I can still be restored again
bdurmus - 9 years ago
On 10 February 2016, my files were encrypted by a ransomware, it has either added (.micro) extension to the names of files, or without changing the name of the file, changed its type.
At that time, windows defender was on online protection, and it could not prevent this ransomware.
After about 1 week, I scanned my laptop in full mode by Windows Defender, ıt caught many Tescrpt.D and Tescrypt.E ransomware, quarantined them, then later I removed them.
However, my files still remain encrypted by this ransomware.
I assume that Tescrypt.D and Tescrypt.E are different ransomware than the one which added ".micro" to the extension of my files.
Pls kindly inform how your works are progreesing to find a software to decrypt the micro-extension encrypter?
lio06 - 9 years ago
on 03/06/16, the teslacrypt v3 hits in France. in my hospital, 3 computer got it and shares on network were corrupted and renamed in ".mp3"
NO probleme to restore the share docs with ours two dayly snapshot. on servers
but all documents on PC were lost. no matter for two "standard" PC but one user keeps all his docs in local storage, whithout backup of course
Is there any news on the possibility to decrypt without paying ?
thanks for help
Dumbdodo - 9 years ago
So, I was wondering. Since it is next to impossible to decipher a RSA4096 key encrypted with Teslacrypt 3.0. Wouldn't it be possible to reversely generate a key under a certain condition. Lets say you had a text document saved in a backup, but you lost a pile of your files to this virus, since the backup never completed.. Sigh..... Would it be possible to generate a key based on the before and after of the file you had a safe backup of? BTW.. This isn't a first hand experience, but i have seen it happen.
Demonslay335 - 9 years ago
TeslaCrypt 3.0 doesn't use RSA4096, it actually lies about that. It uses ECHD to protect the keys, mixed with another layer of AES256. AES256 with CBC mode by design is not vulnerable to plaintext attacks, so a before/after is of no help - we would have seriously solved this the day it came out if that was the case. One thing you have to factor is that this ransomware, along with the other big ones like Locky and CryptoWall, use nearly the same cryptography that secures your bank transactions - if we could break it easily, we'd have a bigger problem (and bounty on our heads) at stake.
GrumpyToo2 - 9 years ago
I read a article that basically said the TeslaCrypt 3.0 infection deletes the orginal file! They said it is therefore possible to run a data recovery tool over your disc and possibly get some of your files back? Has anybody read this and tired it? I would be interested to hear what tool you have used and how successful you have been!?
Demonslay335 - 9 years ago
This is discussed at length in the FAQ and the support topic. Very few have had success, but it is always worth a shot. You can try Recuva, ShadowExplorer, PhotoRec, TestDisk, and OnTrack Recovery.
mekemeke - 9 years ago
hope?
Nadia_V - 9 years ago
@Demonslay335 Those recovery Tools you mentioned, would they lead to different results or would they all lead to the same amount of recovered data? Looking Forward to your reply. Thanks for putting so much energy in this I appreciate it and follow you on twitter regarding a solution Teslacrypt3. (I got the .ttt ransomware) cheers nadia
Demonslay335 - 9 years ago
Sometimes different tools may have different results, you never know. They are all free (except OnTrack I think) so there's no risk in trying them all anyways. Beware that the more low-level tools like PhotoRec may simply pull junk files like temp files, and they won't be named (e.g. "file001.JPG", " file002.JPG"...).
Overall, pre-emptive backups is always the best solution. Moving forward, you should really invest time into setting up a backup scheme. I recommend a simple cloud service such as Dropbox, Carbonite, or CrashPlan, all affordable options that include versioning, which allows you to restore a previous version of files from before the ransomware overwrote the files.
suzauddaula - 9 years ago
how is it works?
http://sureshotsoftware.com/guides/micro-file-virus/
Demonslay335 - 9 years ago
They don't actually decrypt files. It's another misleading article that promises a solution, then just says "recover from backups". I would NOT trust any tools from that site, aside from ShadowExplorer, which is already mentioned as something to try in the guides here on BC.
elyogui - 9 years ago
Good afternoon, I have the following variant, is there any solution at the moment?
Thanks for your support
Identified by
sample_extension: .mp3
sample_bytes: [0x0 - 0x98] 0x0000000000000000AABD7DAB3F89924B0000000000000000
Lawrence Abrams - 9 years ago
TeslaCrypt has closed its doors and released the master decrypt key. BloodDolly has already updated his tool so it can now decrypt all files encrypted by TeslaCrypt 3.0 and 4.x. More info here:
https://www.bleepingcomputer.com/news/security/teslacrypt-shuts-down-and-releases-master-decryption-key/
Tauni - 9 years ago
I am infected with Trojan-Ransom.Win32.CryptXXX Variant of the virus and all my files have .crypt extensions and there is a ransom note on a notepad document called !Recovery followed by a personal ID. I have tried Kaspersky RannohDecryptor but it doesn't work it states that this variant is not supported. Is there a Decryptor that anyone could suggest? Or am I the target of a NEW variant and all my files will remain in lock down until l someone comes up with a decryptor?
iiDarkBlox - 9 years ago
UPDATE: If you were infected by this virus, download Malwarebytes and run a scan quickly where the directory the ransomware is, you can easily find it. You can remove it easily. TeslaCrypt has also been decrypted and a flaw allows it's victims to recover their files.