-
Yeabests.cc: A fileless infection using WMI to hijack your Browser
A new fileless browser hijacker called Yeabests.cc or TopYea has been discovered. This infection creates a WMI event handler that executes a VBScript script every 10 seconds to infect your browsers shortcuts so it opens a site under the developers control.
- April 25, 2016
- 09:15 AM
 19
19
-
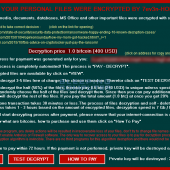
The 7ev3n-HONE$T ransomware encrypts and renames your files to R5A
A new ransomware named 7ev3n-HONE$T has been discovered that is a variant of the 7ev3n ransomware. This ransomware will encrypt your files and then require a $400 USD bitcoin payment to decrypt your files. At this time there is no way to decrypt your files for free.
- April 23, 2016
- 06:10 PM
 0
0
-
New Webinar: Choose Your Own Investigation — Browser Attack Edition

Modern attacks have shifted focus to the browser, yet detection tools remain largely blind to the crucial activity happening there.
Join Push Security on February 11th for an interactive "choose-your-own-adventure" webinar on ClickFix, credential phishing, and other in-browser attacks we've observed in the wild.
-
TeslaCrypt 4.1b Released with Few Modifications
A quick post that version 4.1b of the TeslaCrypt Ransomware has been released. I am unsure when this was released, but a victim submitted a sample today of this new variant. It is currently unknown what has changed internally to the program, but there have been additional payment gateways added.
- April 20, 2016
- 05:55 PM
 18
18
-
Decrypted: The new AutoLocky Ransomware fails to impersonate Locky
A new ransomware was discovered that tries to impersonate the well known Locky ransomware. This impersonator is created in the AutoIt scripting language and has a vulnerability that allows encrypted files to be decrypted.
- April 16, 2016
- 05:39 PM
 9
9
-
Why Everyone should uninstall QuickTime Now!
Yesterday US-Cert released a security alert about two new critical vulnerabilities in in QuickTime for Windows. As Apple has announced that they are no longer supporting QuickTime and will not be fixing these vulnerabilities, it is suggested that you uninstall this program from your computer.
- April 15, 2016
- 05:12 PM
 3
3
-
Adware uploads Screenshot of your Active Windows without your Permission
A new adware has been discovered that performs a severe privacy breach by uploading a screenshot of the user's active windows to a server under their control. This means that any info on the screen, whether it is a tax return, password manager, or corporate secrets is now available the adware company.
- April 15, 2016
- 03:56 PM
 3
3
-
Adware Bundlers pushing CryptoCurrency Miners on Unsuspecting Victims
Adware bundlers are now installing cryptocurrency miners on victim's computers. A new offer called VNLGP Miner has been discovered that installs a cryptocurrency miner that utilizes 70% of the user's graphics card in order to generate revenue for the developer.
- April 14, 2016
- 09:15 AM
 4
4
-
Patch Tuesday fixes critical vulnerabilities in Microsoft and Adobe Products
For the April's Patch Tuesday, both Microsoft and Adobe have released security updates for their products. Some of these updates were for critical vulnerabilities in Microsoft and Adobe products, which could allow attackers to remotely execute commands on a vulnerable computer.
- April 12, 2016
- 03:52 PM
 0
0
-
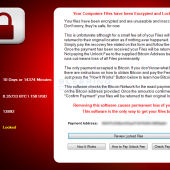
Jigsaw Ransomware Decrypted: Will delete your files until you pay the Ransom
When the Jigsaw Ransomware threatens to delete your files, it's not kidding. This is the first ransomware that we have seen that carries out its threats and will delete increasingly greater amounts of files each hour until the payment has been made. Thankfully, a method has been discovered that can decrypt these files for free.
- April 11, 2016
- 05:20 PM
 44
44
-
Petya Ransomware's Encryption Defeated and Password Generator Released
A method to decrypt Petya Ransomware encrypted hard drives have been discovered. Using a special site and tools, it is now possible to extract data from the encrypted drive that can then be used to create the password required to decrypt it.
- April 10, 2016
- 04:46 PM
 14
14
-
CryptoHost Decrypted: Locks files in a password protected RAR File
A new ransomware called CryptoHost was discovered that encrypts your data and then demands a ransom of .33 bitcoins or approximately 140 USD to get your files back. In reality, though, your data is not encrypted, but rather copied into a password protected RAR archive.
- April 08, 2016
- 01:52 PM
 13
13
-
Adobe releases the Flash Player 21.0.0.213 emergency update to resolve Critical Vulnerabilities
Adobe has released an emergency update to resolve critical vulnerabilities in their Adobe Flash Player product. The new version is 21.0.0.213 and resolves critical vulnerabilities that could allow an attacker to remotely take control of your computer.
- April 08, 2016
- 11:00 AM
 2
2
-
The Rise of the Interactive Tech Support Scam
Tech Support Scammers are always trying new tricks to squeeze as much money out of a victim as they can. Recently I have seen a new approach that I call Interactive Tech Support Scams that are not meant to scare you, but rather to appear as if they are trying to help you.
- April 08, 2016
- 09:15 AM
 5
5
-
Adobe releases Security Advisory on Critical Vulnerability CVE-2016-1019
Adobe released an updated security advisory yesterday regarding a critical vulnerability (CVE-2016-1019) that exists in Adobe Flash Player 21.0.0.197 and earlier versions. Though an emergency update may be released tomorrow, all Flash users are advised to immediately upgrade to the latest version.
- April 06, 2016
- 08:30 PM
 1
1
-
Rokku Ransomware Encrypts each file with its own Unique Key
The Rokku Ransomware has been discovered that encrypts each file with its own individual encryption key. Another interesting feature of Rokku is its use of the uncommon encryption algorithm called Salsa20, which has greater speeds than AES and supposedly greater security.
- April 03, 2016
- 08:14 PM
 14
14
-
The KimcilWare Ransomware targets web sites running the Magento Platform
Web sites running the Magento eCommerce platform are currently being targeted by an attacker who infects them with a new ransomware called KimcilWare. This ransomware will encrypt all the data on the web site and demand $140 to $415 USD in order to get the data back.
- March 30, 2016
- 05:26 PM
 10
10
-
DOJ gains access to iPhone and withdraws case, Apple Responds
Today the FBI dropped legal actions against Apple as they were able to gain access to the iPhone used by Syed Farook. Though this case, and its related privacy and security issues, have been put on hold, the knowledge that this vulnerability exists is going to spur more people, and probably the wrong ones, into discovering it.
- March 28, 2016
- 11:44 PM
 6
6
-
Apple blocks insecure Flash 21 and 18 Versions in OS X
Due to an undisclosed vulnerability in Flash player versions prior to 21.0.0.182 and 18.0.0.333, Apple has blocked access to Flash when using Safari in OS X. When visiting sites that require Flash you will now be greeted with a warning that it has been blocked and instructions on how to update it.
- March 28, 2016
- 05:28 PM
 0
0
-
Paying the Coverton Ransomware May Not get your Data Back
A new family of ransomware called Coverton was released last week that due to poor design is leaving people who payed the ransom without a working decryptor. For those who may be affected by the Coverton Ransomware, you should strongly reconsider if you plan on paying the ransom.
- March 28, 2016
- 03:35 PM
 4
4
-
Petya Ransomware skips the Files and Encrypts your Hard Drive Instead
Instead of targeting your files, the Petya ransomware goes for it all by encrypting the Master File Table on a victim's drive. This prevents any files, including Windows, from being accessible until a victim pays the ransom.
- March 25, 2016
- 02:29 PM
 65
65