
Attackers are exploiting a recently disclosed WebLogic vulnerability to install a new ransomware called Sodinokibi. As this vulnerability is trivial to exploit, it is important that server admins install the patch immediately in order to prevent infections or unauthorized access.
Earlier this month, a deserialization vulnerability (CVE-2019-2725) was discovered in Oracle WebLogic Server that allows attackers to gain full access to the server in order to install malware or use it as a launchpad for further attacks. On April 26th, Oracle released a patch that should be immediately installed so that you become protected.
Unfortunately, attackers have already utilized this vulnerability to install malware such as miners, botnets, and now the Sodinokibi Ransomware.
To make matters worse, the Cisco Talos group, who discovered the Sodinokibi Ransomware, found that the attackers also installed GandCrab on already infected servers as an additional method to earn ransom payments.
"After finishing deploying Sodinokibi ransomware inside the victim's network, the attackers followed up with an additional CVE-2019-2725 exploit attempt approximately eight hours later. However, this time, the attackers chose to distribute Gandcrab v5.2. We find it strange the attackers would choose to distribute additional, different ransomware on the same target. Sodinokibi being a new flavor of ransomware, perhaps the attackers felt their earlier attempts had been unsuccessful and were still looking to cash in by distributing Gandcrab."
The Sodinokibi Ransomware
When the Sodinokibi Ransomware is executed it will issue the following commands to delete shadow volume copies and disable Windows startup repair.
"C:\Windows\System32\cmd.exe" /c vssadmin.exe Delete Shadows /All /Quiet & bcdedit /set {default} recoveryenabled No & bcdedit /set {default} bootstatuspolicy ignoreallfailures
It will then proceed to encrypt the files on the server. When encrypting files, it will utilize a random extension that is unique for each infected machine.
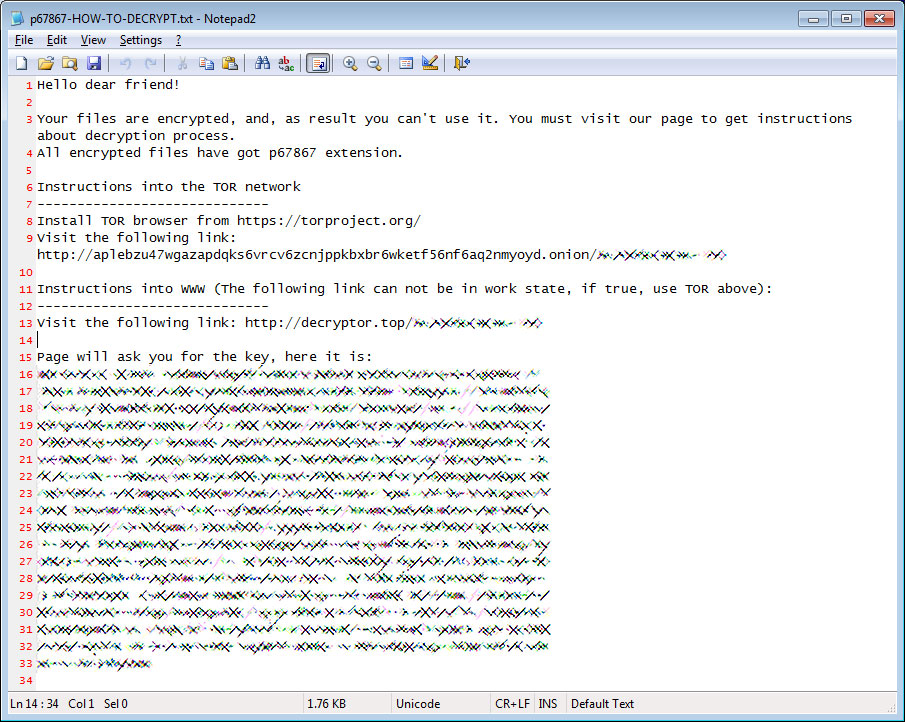
For each folder that is scanned for files, it will also create a ransom note that is named in the format [extension]-HOW-TO-DECRYPT.txt. These ransom notes contain a unique key and links to a payment site.
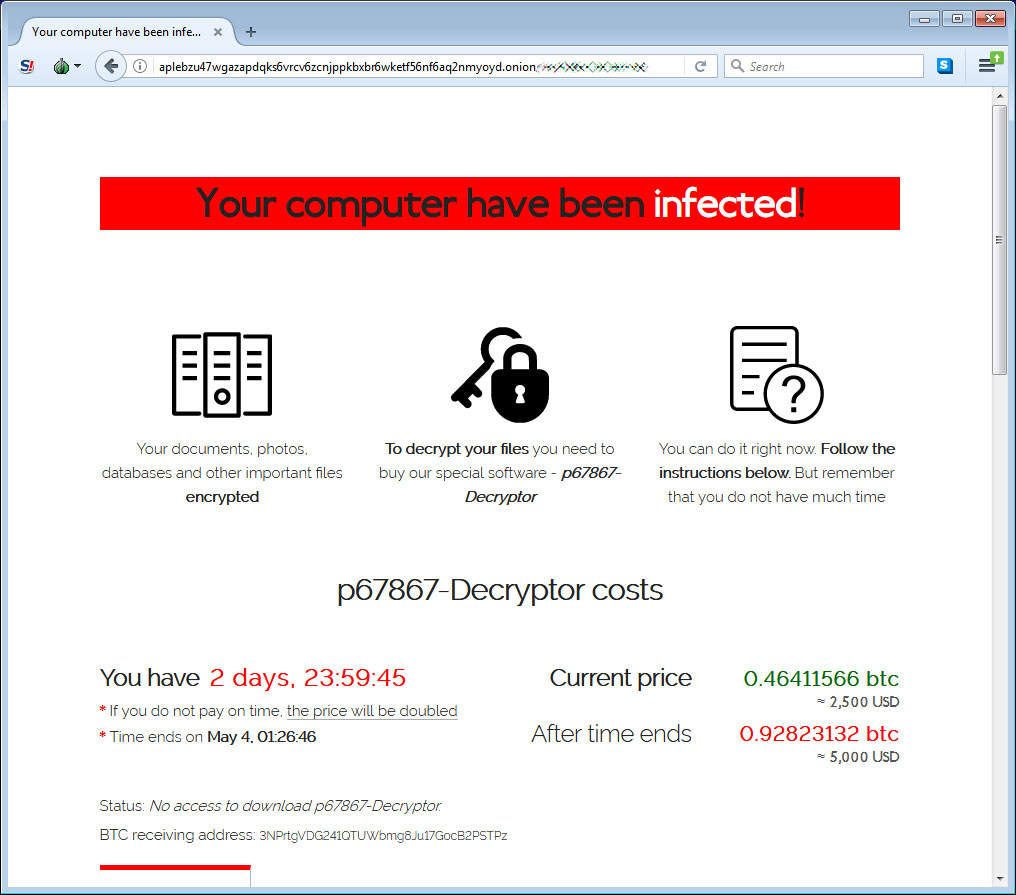
When a victim visits the site, they will be asked to enter their unique extension and key. Once submitted, they will be shown a page that displays the ransom amount and a bitcoin address that should be used to make a payment.
It is not known if there are any weaknesses in this ransomware family, but if any new information becomes available we will update this article.
Protecting yourself from the Sodinokibi Ransomware
Due to the ease of exploitation, if you are running a WebLogic server, there is a good chance it may have been compromised.
With this in mind, you should immediately install the Oracle's WebLogic patch and then perform a thorough audit of the server for suspicious activity.
This includes examining the %Temp% folder for downloaded malware, examining event logs, and checking autostarts for suspicious programs. If possible, a wipe and reinstall is recommended.
To further harden WebLogic servers again future attacks, Cisco Talos recommends you use the following steps:
- Log and centrally collect web, application, and operating systems events.
- Restrict the access of the account used to run the WebLogic process
- Monitor for signs of compromise:
-
- Egress network communications from data center systems.
- Ransomware "Canary" files.
- External HTTP POSTs to new URIs.
- Web shells.
- Unexpected activity of service/system accounts (WebLogic user).
- Scan for, understand, and mitigate your vulnerability posture.
- Restrict egress Data Center communications.
- Segment the network for defense and monitoring.
- Control URL access (in this case external access to "/_async/*" and "/wls-wsat/*").
- Plan for Disaster Recovery, including maintaining and testing data backups and recovery.
- Configure PowerShell to execute only signed scripts.
IOCs
Associated sites:
decryptor.top
http://aplebzu47wgazapdqks6vrcv6zcnjppkbxbr6wketf56nf6aq2nmyoyd.onion
Associated files:
[extension]-HOW-TO-DECRYPT.txt
%Temp%\[random].bmp
Interesting strings:
https://
wp-content
static
content
include
uploads
news
data
admin
images
pictures
image
temp
tmp
graphic
assets
pics
game
jpg
png
gif
Ransom note text:
Hello dear friend!
Your files are encrypted, and, as result you can't use it. You must visit our page to get instructions about decryption process.
All encrypted files have got p67867 extension.
Instructions into the TOR network
-----------------------------
Install TOR browser from https://torproject.org/
Visit the following link: http://aplebzu47wgazapdqks6vrcv6zcnjppkbxbr6wketf56nf6aq2nmyoyd.onion/[id]
Instructions into WWW (The following link can not be in work state, if true, use TOR above):
-----------------------------
Visit the following link: http://decryptor.top/[id]
Page will ask you for the key, here it is:
[key]
Break down IAM silos like Bitpanda, KnowBe4, and PathAI
Broken IAM isn't just an IT problem - the impact ripples across your whole business.
This practical guide covers why traditional IAM practices fail to keep up with modern demands, examples of what "good" IAM looks like, and a simple checklist for building a scalable strategy.









Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now