
The SynAck ransomware gang released the master decryption keys for their operation after rebranding as the new El_Cometa group.
When ransomware operations encrypt files, they usually generate encryption keys on a victim's device and encrypt those keys with a master encryption key. The encrypted key is then embedded in the encrypted file or ransom note and can only be decrypted using the ransomware gang's master decryption keys (private keys).
Today, the SynAck ransomware operation released the master keys, the gang's decryptors, and a manual on using the master keys, and shared them on their data leak site and with the cybersecurity news site TheRecord.
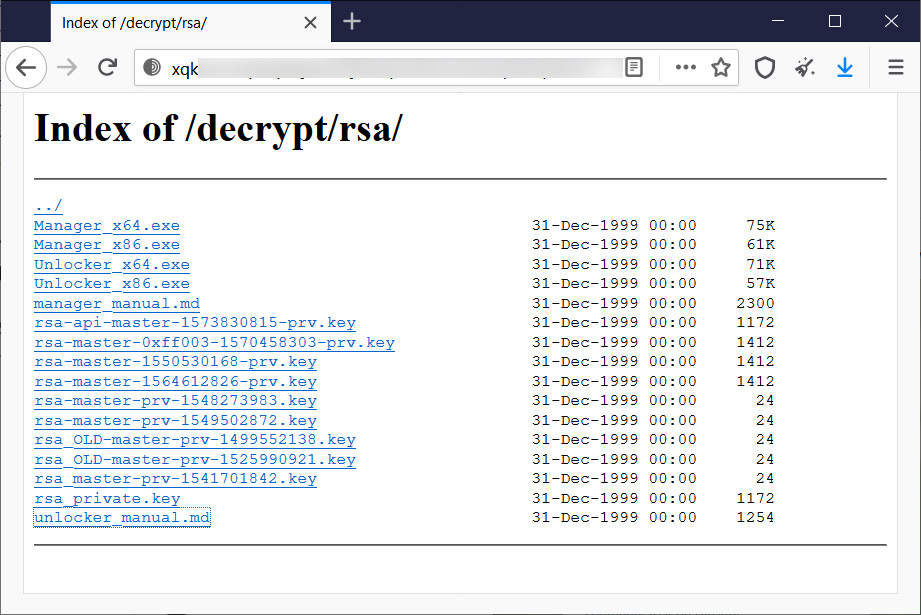
After receiving the keys, TheRecord shared them with ransomware expert Michael Gillespie who verified that the keys are legitimate and will be creating a SynAck decryptor so victims can recover their files for free.
Emsisoft CTO Fabian Wosar told BleepingCompuer that the archive contains a total of sixteen master decryption keys.
Keys released after rebranding to El_Cometa
The SynAck ransomware operation launched in August/September 2017 but was never a very active group. Their most activity was in 2018 but slowly tapered off at the end of 2019.
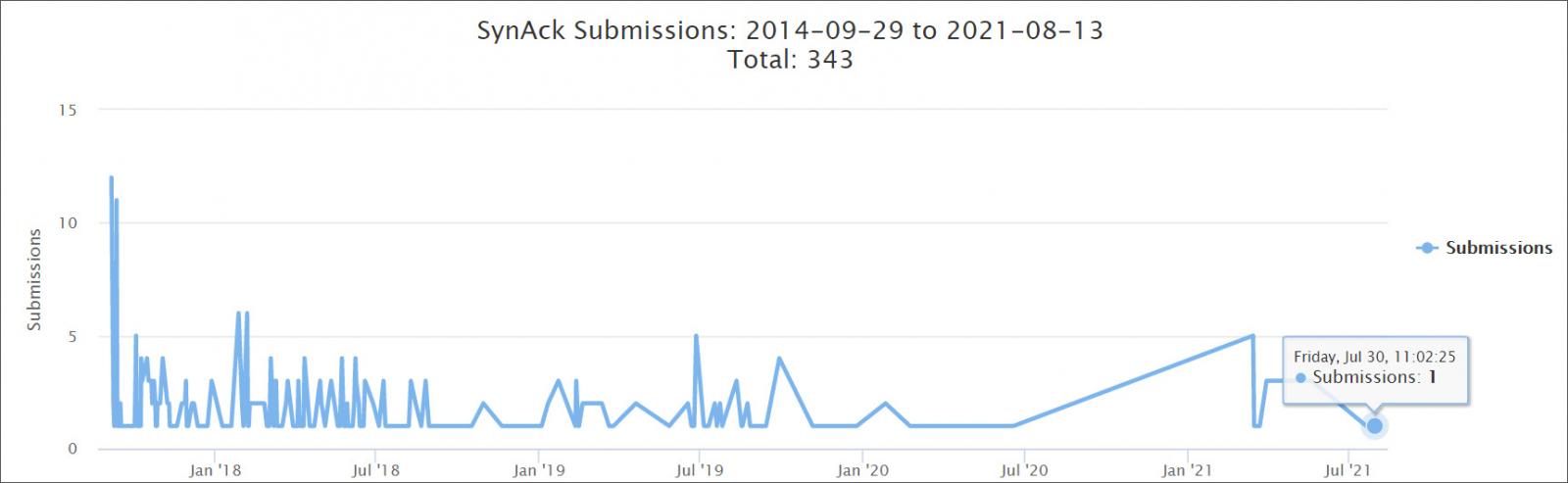
Source: ID Ransomware
At the end of July 2021, the ransomware group rebranded as El_Cometa and became a ransomware-as-a-service (RaaS), where they recruit affiliates to breach corporate networks and deploy their encryptor.
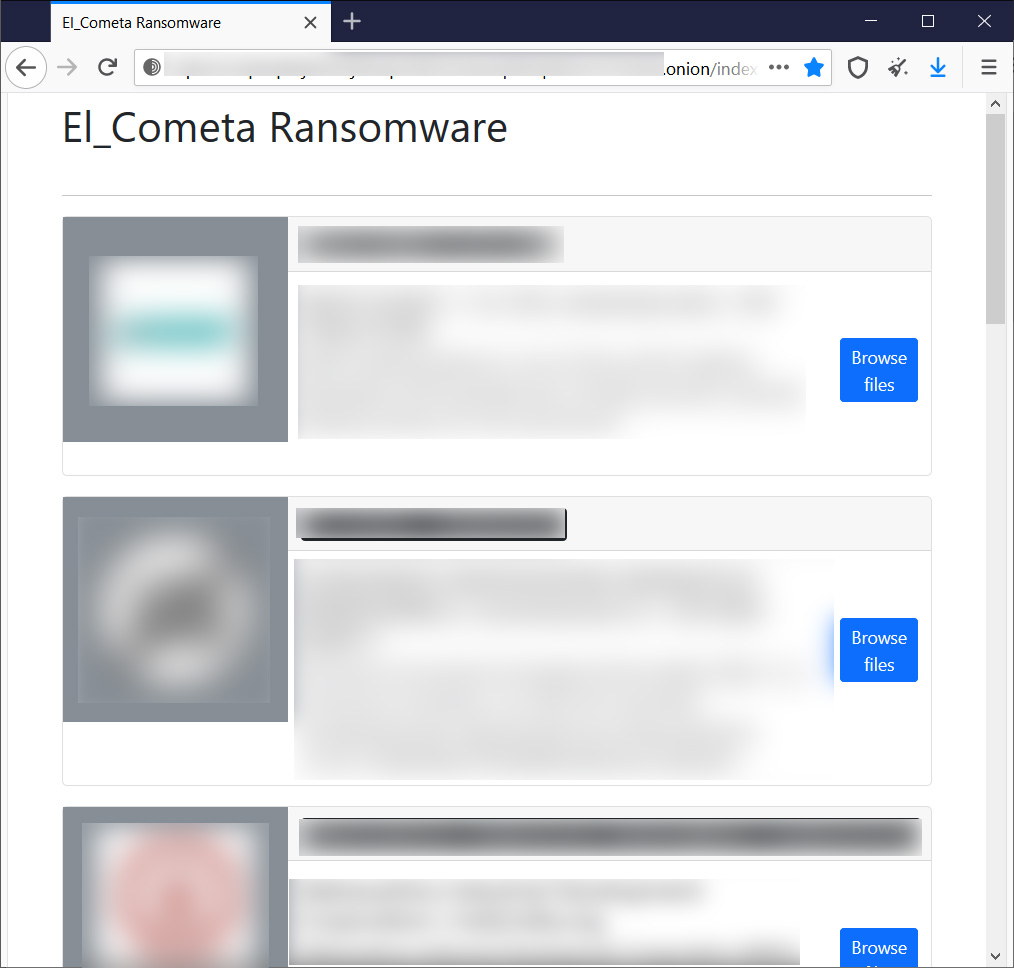
While it is not common for ransomware gangs to release master decryption keys, it has happened in the past when operations shut down or rebrand to a new name.
Other ransomware gangs that have released master decryption keys include Avaddon, TeslaCrypt, Crysis, AES-NI, Shade, FilesLocker, Ziggy, and FonixLocker.
Break down IAM silos like Bitpanda, KnowBe4, and PathAI
Broken IAM isn't just an IT problem - the impact ripples across your whole business.
This practical guide covers why traditional IAM practices fail to keep up with modern demands, examples of what "good" IAM looks like, and a simple checklist for building a scalable strategy.









Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now